Trusted authentication and safe access control method of MPLS network
A technology of secure access and control methods, applied in the field of network communication, can solve problems such as PPPoE inapplicability and network bottlenecks, and achieve high flexibility and processing speed, good application prospects, and good compatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
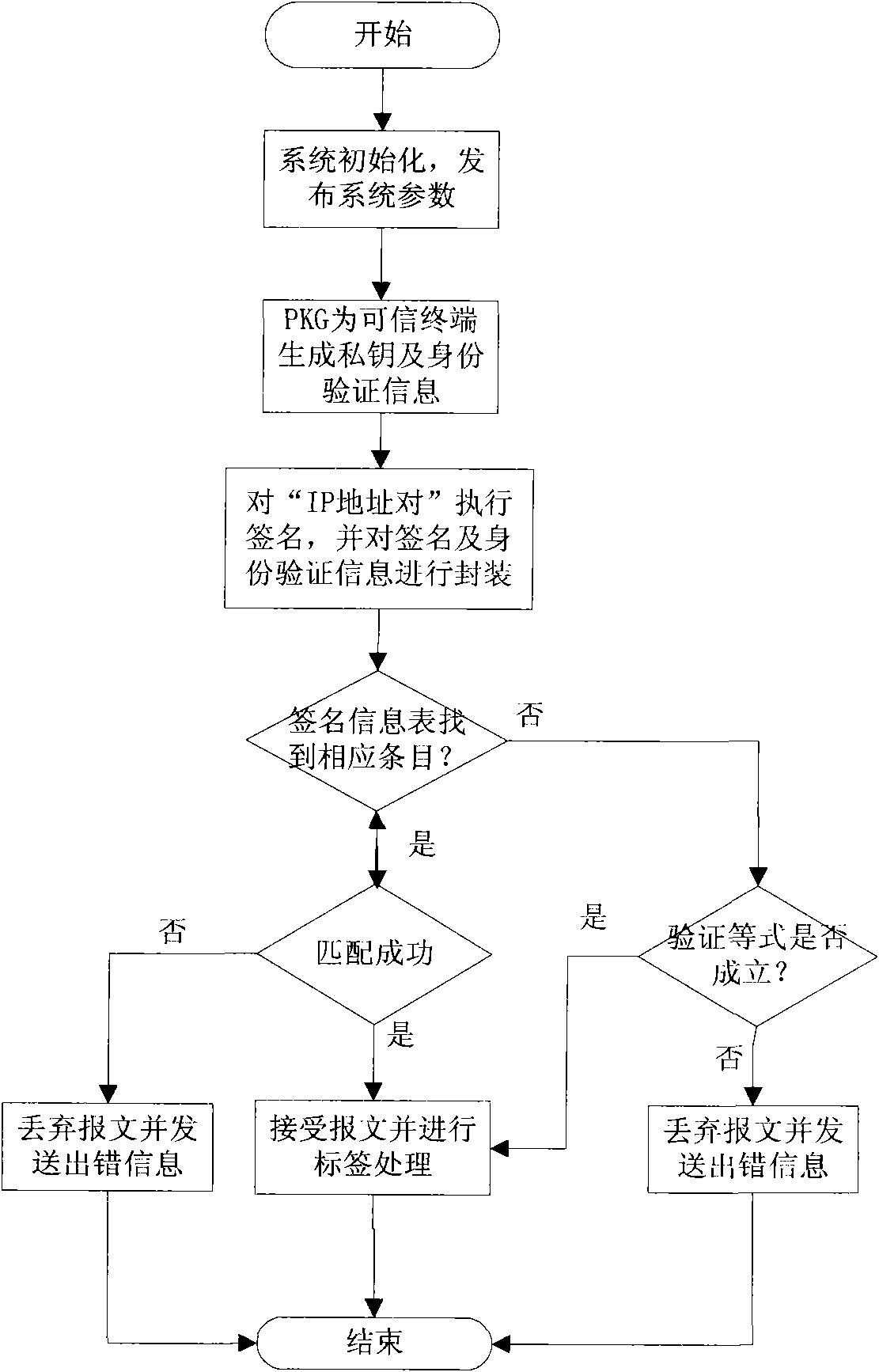
[0033] In order to make the purpose, implementation and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0034] see figure 1 , introduces the IP address pair short signature principle of the method of the present invention. PKG generates private key S for trusted end nodes ID and authentication information P ID . figure 1 IP in pair It is the message to be signed: the result string after concatenating the source and destination IP address pairs of this communication and performing AND operation with a random value. Authentication information is sent to the LER for use in the signature verification process.
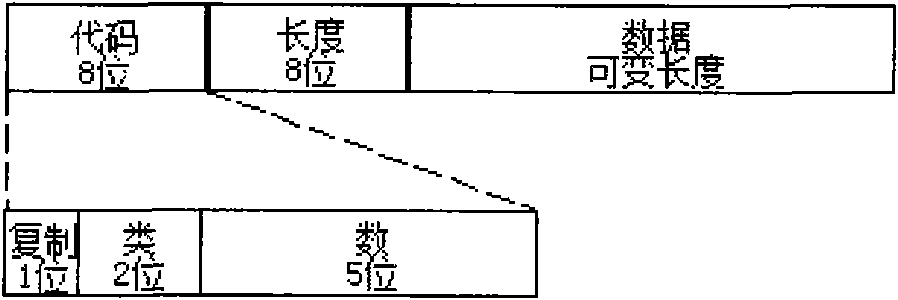
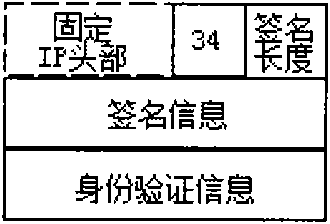
[0035] see Figure 2 to Figure 3 , introduces the signature information encapsulation of the method of the present invention. The method consists of the following two phases:
[0036](1) Traditional signature verification needs to be performed by the destina...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com