Data integrity verification method for shared outscored database
A technology for data integrity and integrity verification, applied in digital data protection, electronic digital data processing, special data processing applications, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0011] The present invention will be further described below in conjunction with the accompanying drawings and examples, but these examples should not be construed as limiting the present invention.
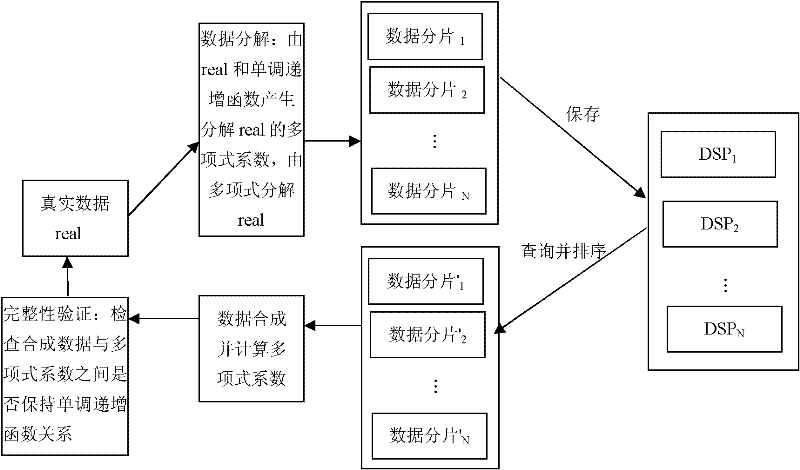
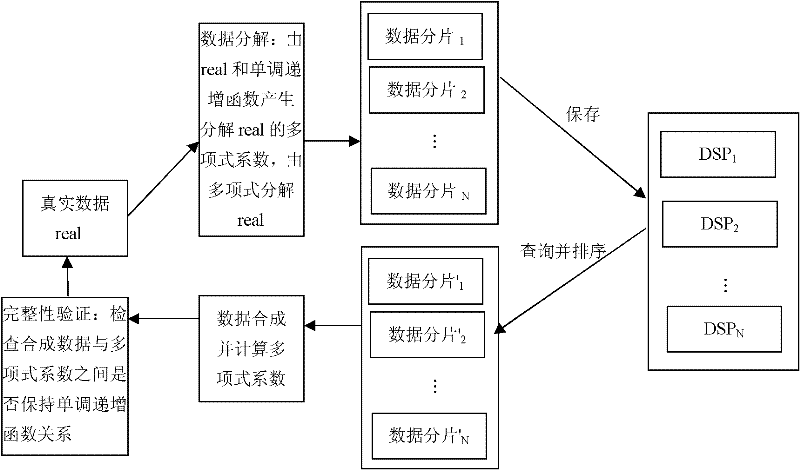
[0012] The present invention implements in three steps:
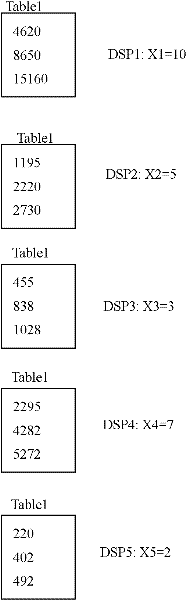
[0013] Define a basic table Table1 (coll int) in the database, and create a table with the same name in the database servers of N=5 database service providers to store the decomposed data fragments. Suppose K=3 at this time, where (X1, X2, X3, X4, X5)=(10, 5, 3, 7, 2), that is, the five DSPs are numbered 10, 5, 3, 7, 2 respectively. The polynomial that decomposes the original data is: a 1 x i 2 +a 2 x i +real(i=1,...,5), where real is a true value, x i The value is the number of the DSP server. a 1 The coefficient is generated by a monotonically increasing function f(x)=2x+5, a 2 The coefficients are generated with a monotonically increasing function g(x)=|_logx_|+6, and the variable x=real.
[0014] During syste...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com