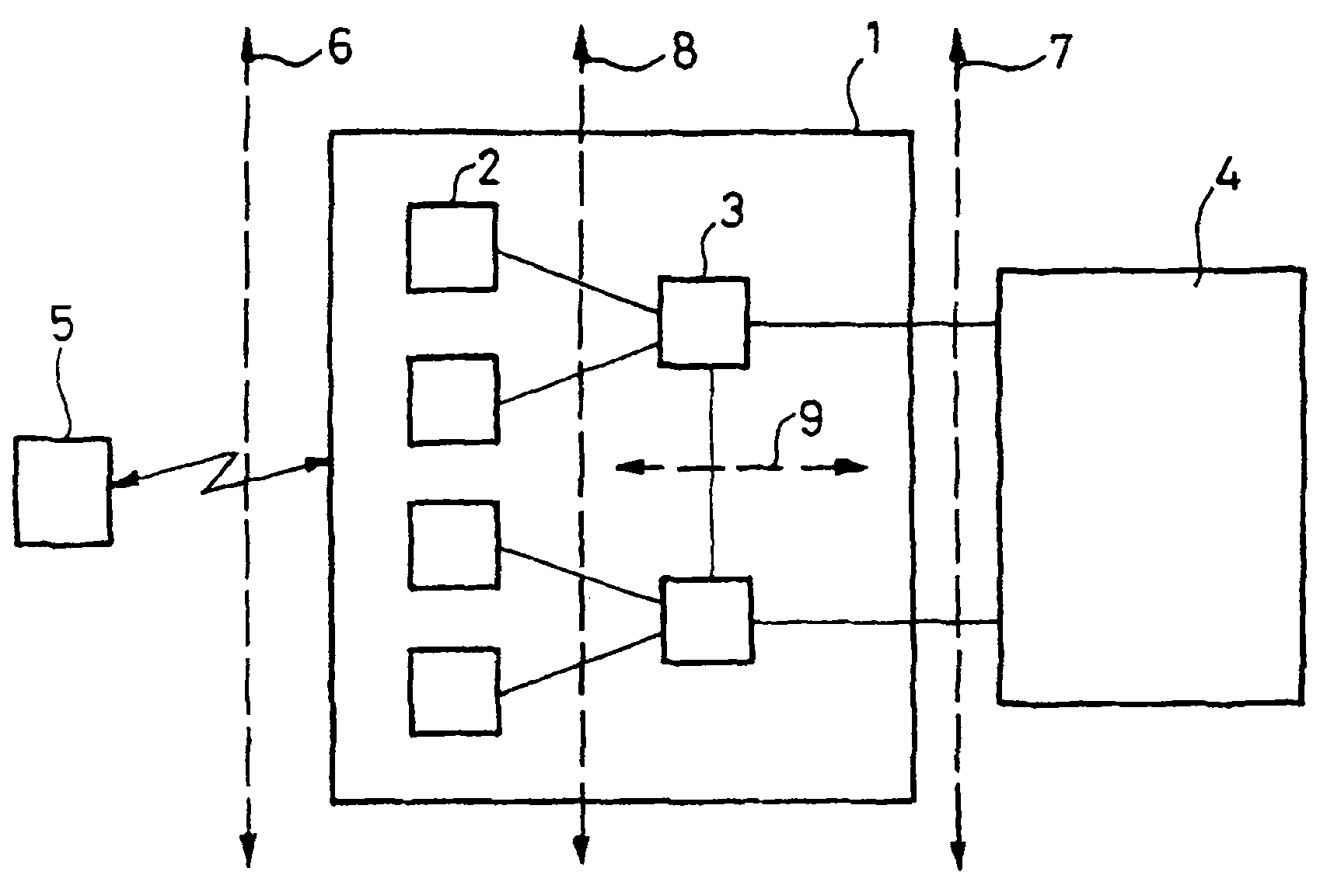
Method for protecting the integrity of messages in a mobile communications system
A mobile wireless and messaging technology, applied in transmission systems, wireless communications, wireless network protocols, etc., can solve the problems of increasing source SRNC processing capacity and complexity, lack of flexibility, and different algorithms
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
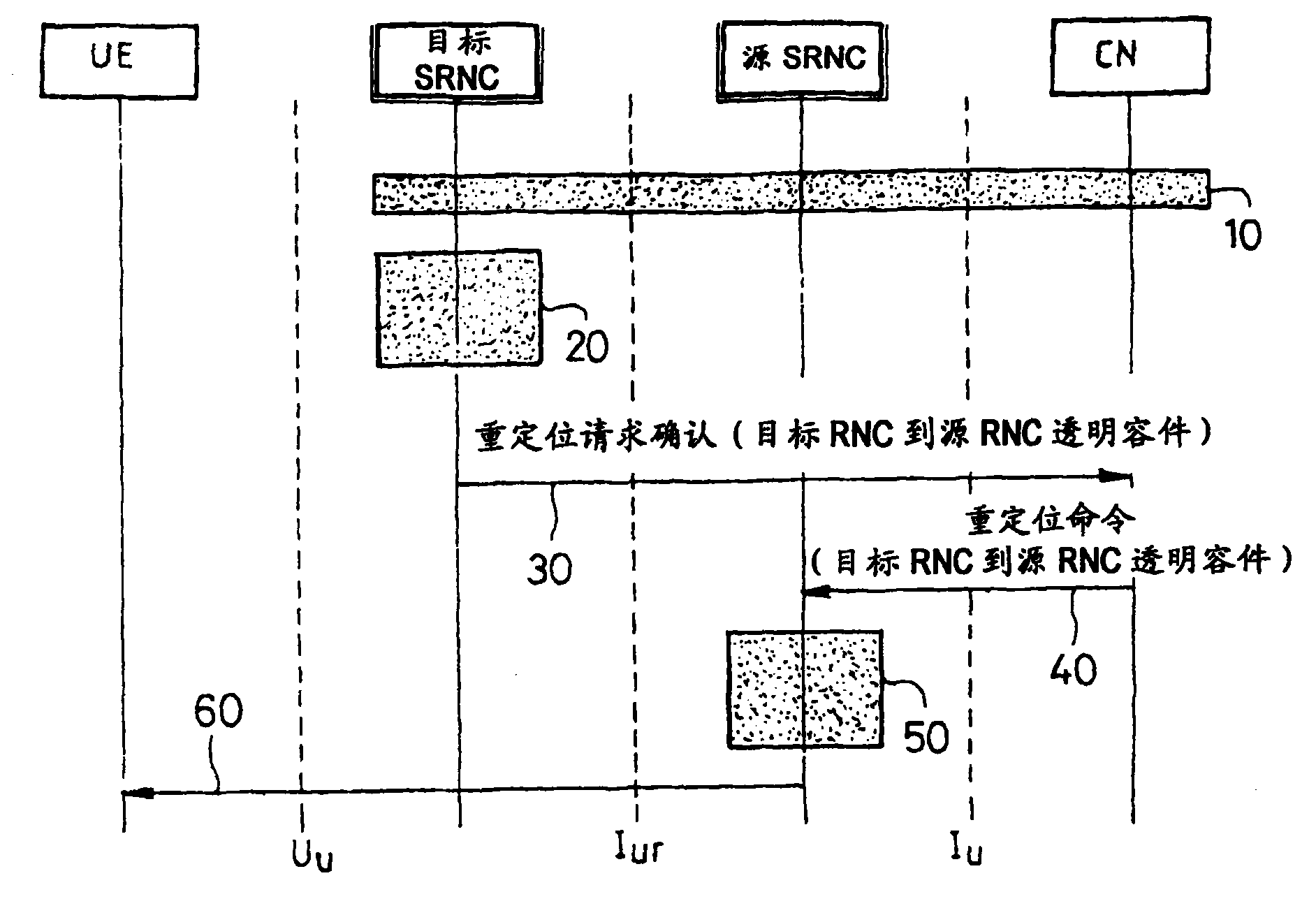
[0105] Figure 4 An example of a method according to the present invention is shown, mainly aimed at and utilizing image 3 Relocation involving UE is shown as an example.
[0106] Step 10' indicates the start of the relocation process.
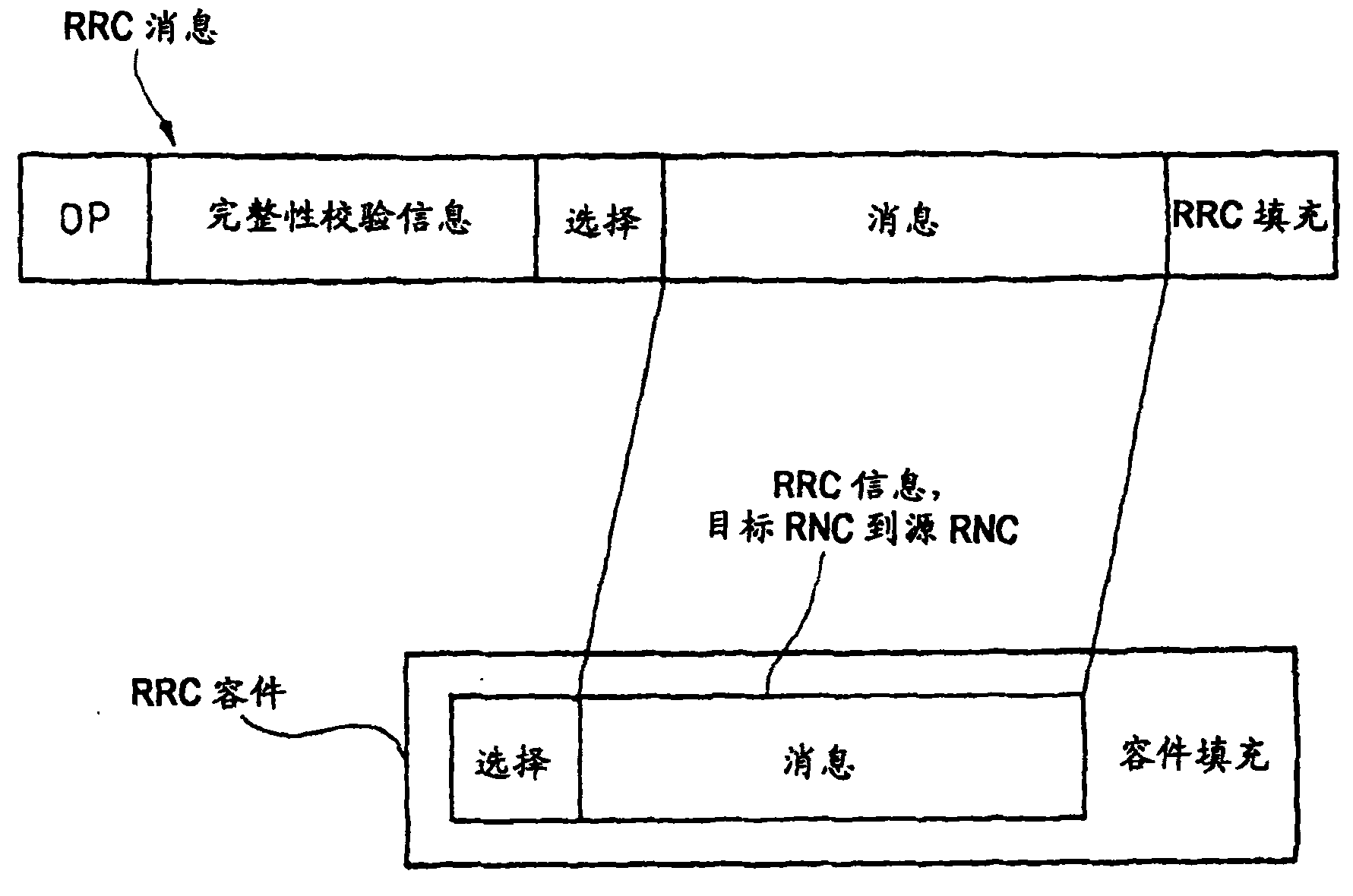
[0107] In step 20', the target SRNC generates RRC information. Apart from figure 2 For the above information generated in step 20, the RRC information unit generated by the target controller also includes additional information and explanatory text.
[0108] In step 20', the target SRNC calculates the MAC-I code. In general, in order to calculate the MAC-I code, the target SRNC can use calculation parameters, such as the calculation parameters sent to it by the source SRNC during the relocation process and / or the calculation parameters selected by the target SRNC, these parameters can be included in step 20 In the integrity protection mode information IE of the RRC information element generated in '. The additional information related to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com