Data prevention method based on content filtering
A content filtering and data technology, applied in the field of information security, can solve problems such as inability to use enterprise data protection solutions, inconvenient normal operations, and single-function encryption methods, to avoid leakage of core data, prevent leakage of sensitive information, and prevent leakage of sensitive information. The effect of data protection granularity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
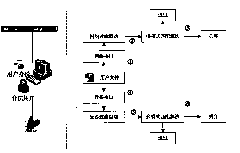
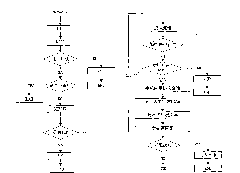
[0015] combine Image 6 , the data protection method based on content filtering in the present invention first adopts the network filtering driving technology to monitor the network data flow, adopts the device filtering driving technology to monitor the peripheral data flow, and monitors the data of the network equipment and the peripheral interface of the terminal computer Capture, and then use the content filtering technology based on multi-pattern matching to perform feature matching on the intercepted network data flow and device data flow. The data flow judged as sensitive information will be blocked from outflow, and the data flow judged as general information will be allowed to outflow. This ensures that sensitive data is leaked. Such as figure 1 , the present invention is based on the data protection method of content filtering, and specific process is as follows:
[0016] ① When the user sends a file through the network interface, monitor the data flow through the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com