Computer booting anti-counterfeit authentication method based on BIOS
A verification method and computer technology, applied in computer security devices, internal/peripheral computer component protection, computing, etc., can solve problems such as damage to the rights and interests of computer brand manufacturers, many factors affecting the anti-counterfeiting effect, damage to the interests of consumers, etc., and achieve convenient sales. Incentive, easy to promote and use, the effect of protecting interests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
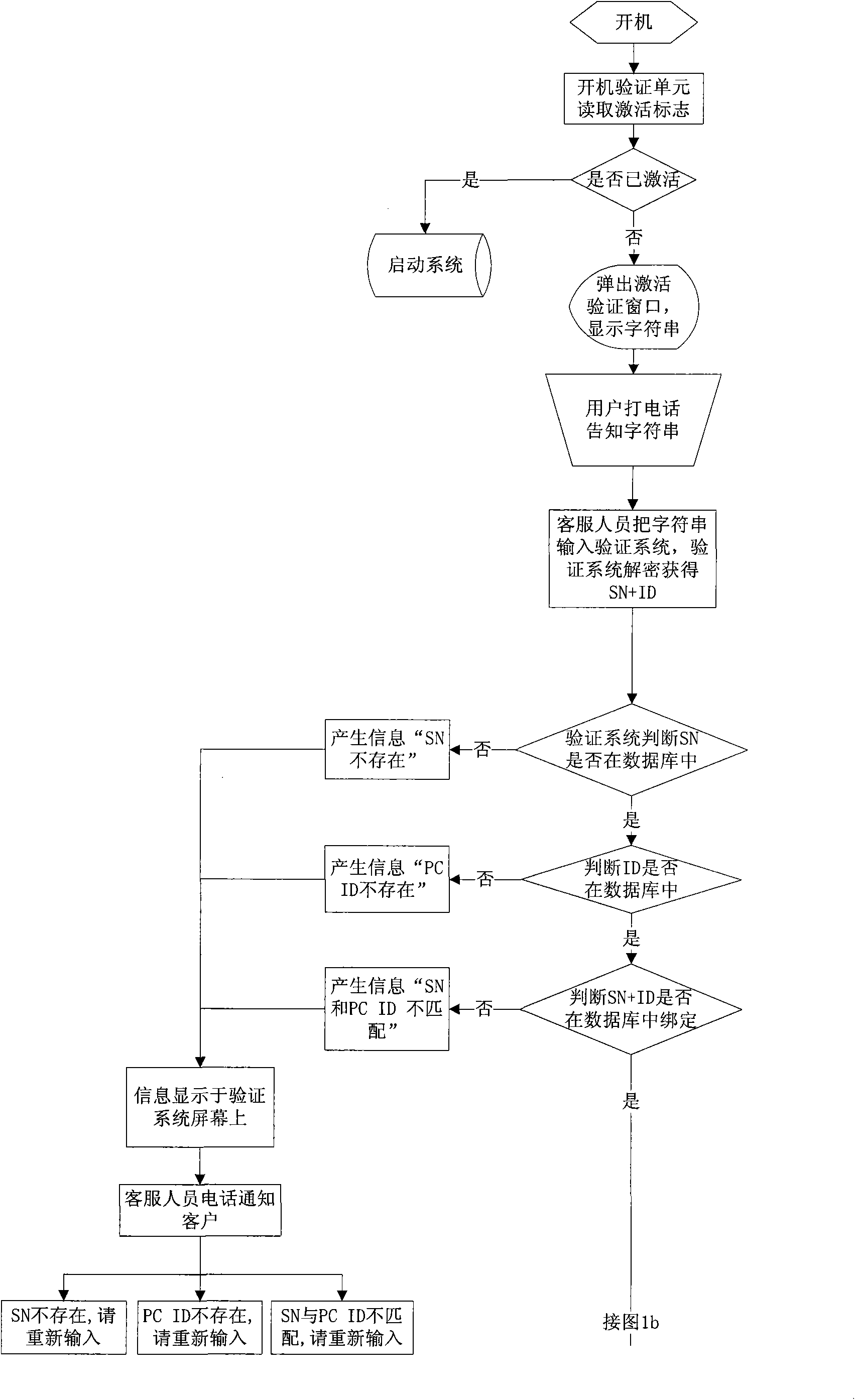
[0031] A user purchases a computer, and a power-on authentication module is implanted in the BIOS of the computer.
[0032] After the user turns on the computer for the first time, the power-on verification module reads the activation flag. At this time, the activation flag is set to be inactive, so the module suspends the operating system startup program, and reads the SN+ID of the computer, and encrypts the SN+ID to form a An activation window pops up after a short string of characters, and the window displays the string, that is, the encrypted SN+ID.
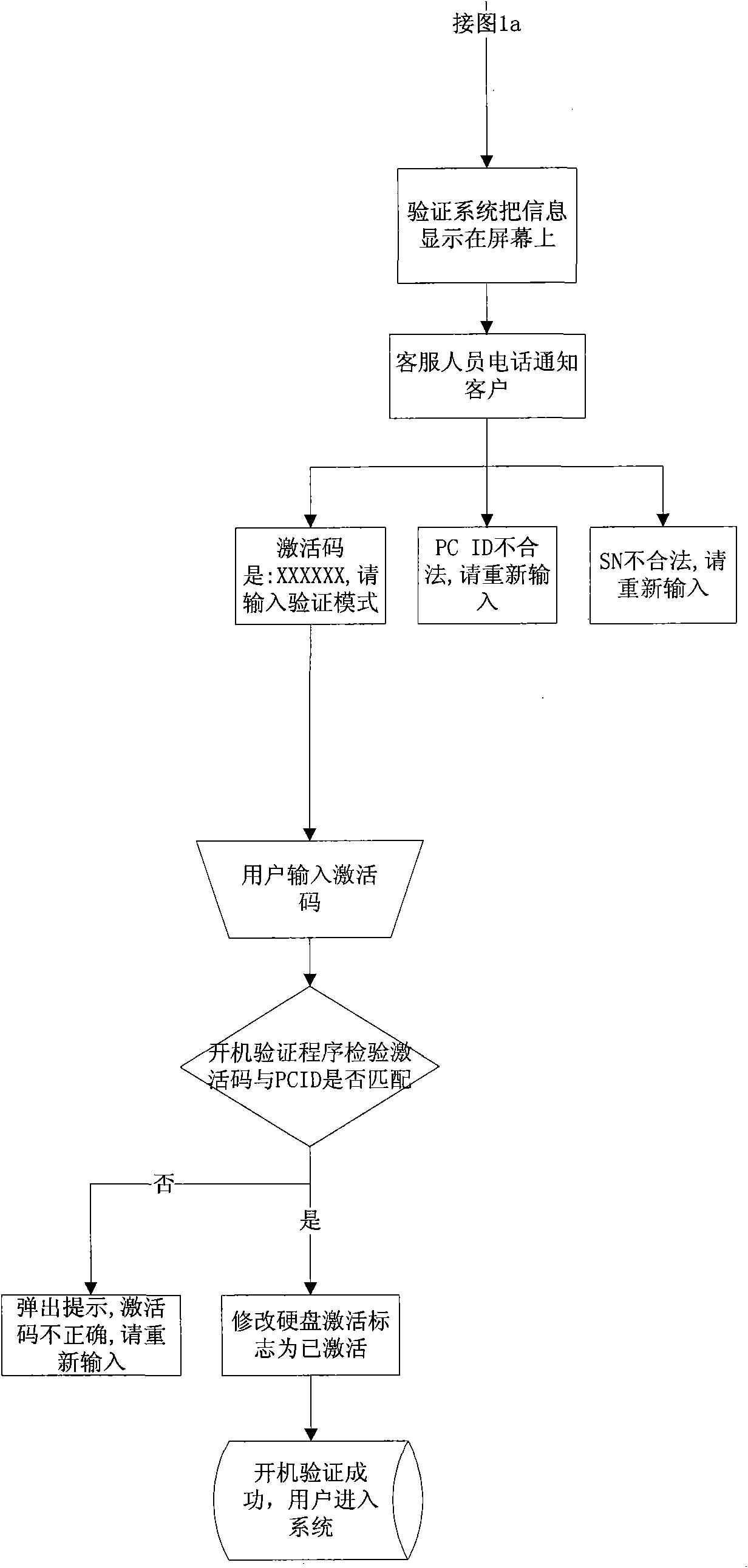
[0033] The user calls the computer manufacturer and informs the customer service of the string. The customer service inputs it into the verification system. After the verification system decrypts it, it judges whether the SN and ID have been stored in the database and whether they match. If not, the user is notified that an error occurred. , if the verification is correct, the verification system will generate an activation c...
Embodiment 2
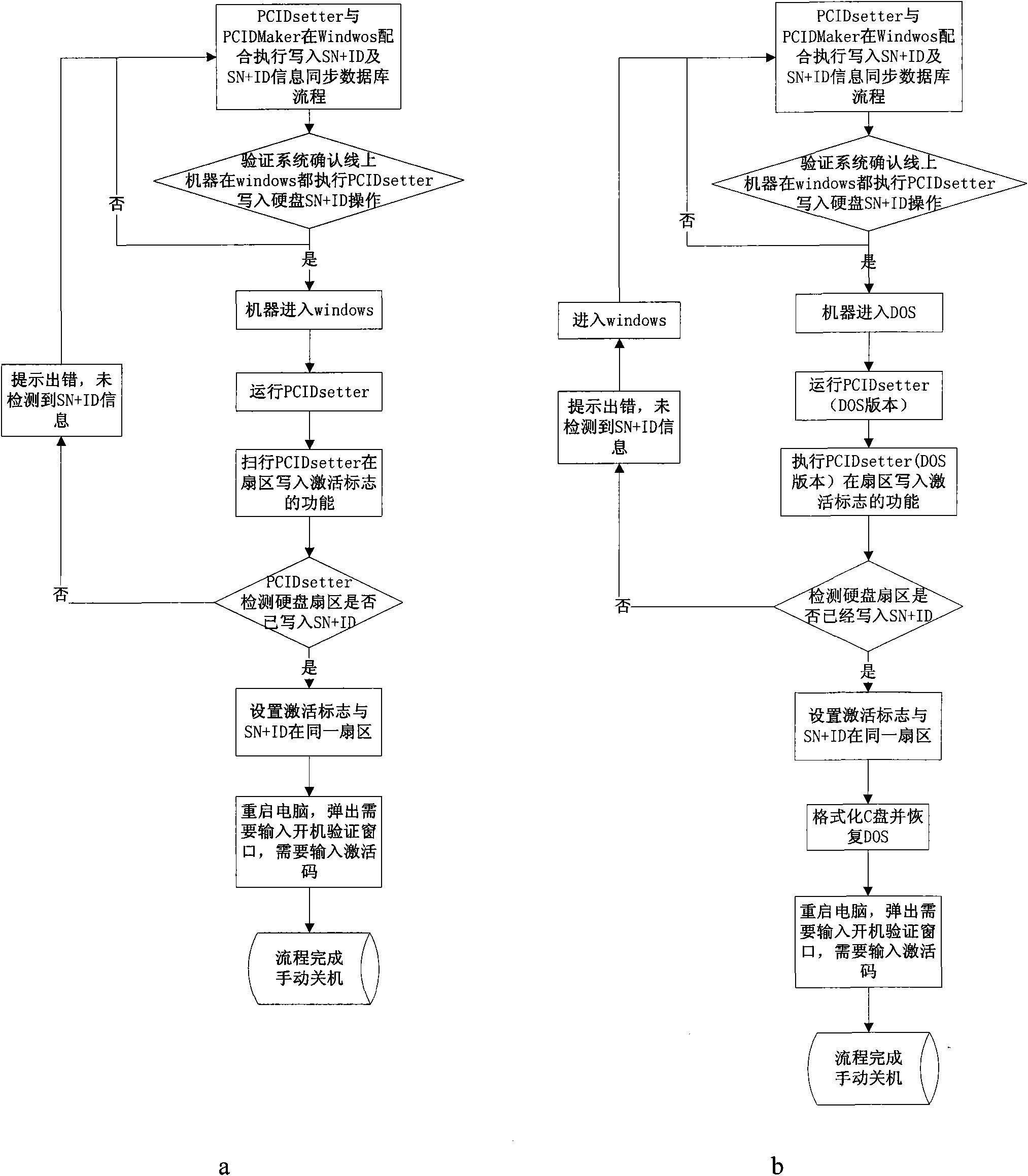
[0039] This embodiment is based on the same situation as Embodiment 1, the difference is that on the computer purchased by the user, a USB device is attached according to the PMP ROM specification of the BIOS, and this USB device plays the role of the power-on verification module described in Embodiment 1 . The device is loaded after the BIOS self-test, and stops the startup program before the operating system in the computer is started.
[0040] The difference between this embodiment and Embodiment 1 is that the user completes the entire verification process by means of a third-party short message platform through a short message. Fig. 3 is a flowchart of this embodiment.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com