Bug wormhole attack method aiming at safe, high-efficiency distance vector routing protocol
A distance vector, routing protocol technology, applied in wireless network protocols, access restrictions, electrical components, etc., can solve the problem that intermediate nodes cannot be reversed, and cannot tamper with routing table entry serial numbers and distance metric values.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
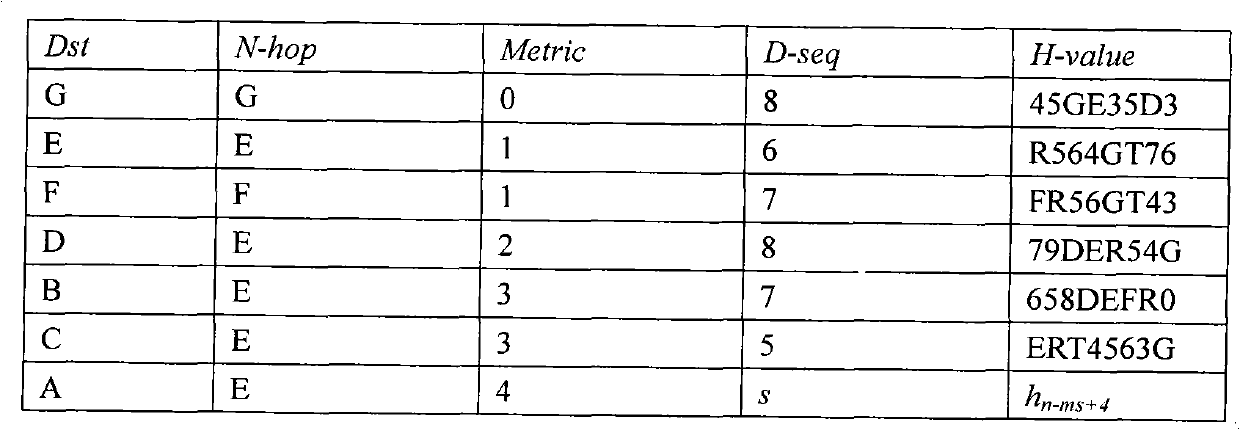
[0032] 1. Routing table information format
[0033] For routing table information format, see figure 1
[0034] (1) Initial routing table settings
[0035] a.dest is set to itself, that is, the entry with itself as the destination.
[0036] b.nex_hop is set to itself like dest.
[0037] c.metric is set to 0, indicating that this routing entry is its own information, which is used to broadcast to the entire network.
[0038] d.seq_num is set to 0, and it will be added after each periodic update.
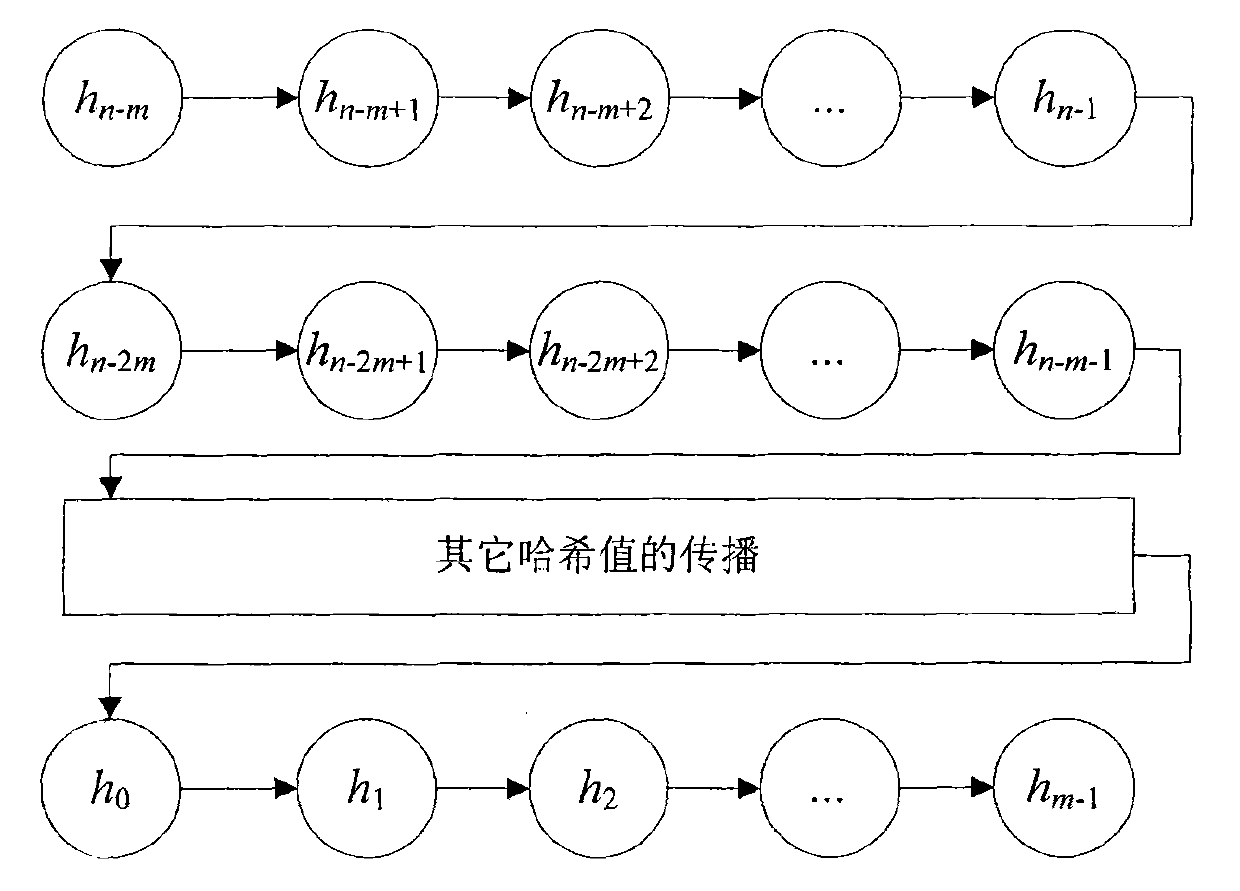
[0039] (2) Setting of the hash value in the routing table entry
[0040] a. The hash value in each entry of the routing table is generated by the node dest.
[0041] b. The hash value hash_num in the routing table entry is determined by the seq_num and metric of the distance from the destination dest.
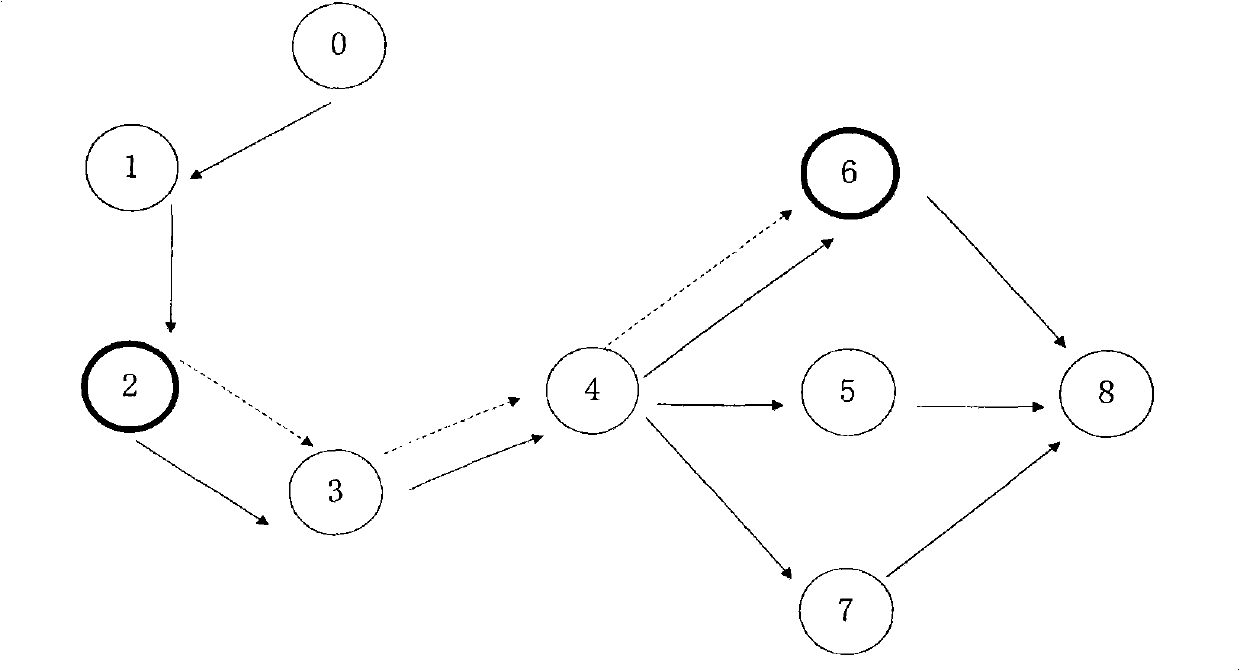
[0042] The choice of two attack effects
[0043] After the network is stable, the routing table of each node contains the routing table entry information of all nodes in the ne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com