Method and system for realizing interlocking of phone and card
A machine card, the only technology, applied in the field of machine card interlocking, can solve the problems of SIM card damage, PIN failure, PIN code stolen interlock function, etc., to achieve the effect of protecting rights and high confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
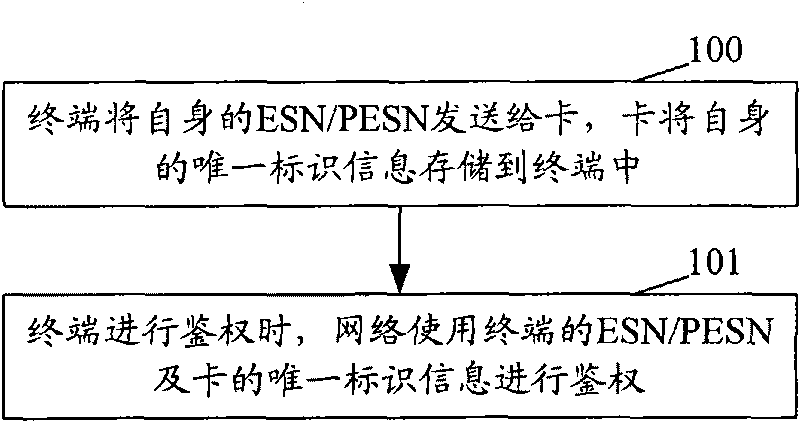
[0047]In order for a terminal (or called a mobile station) to access the network normally, it needs to provide information such as International Mobile Subscriber Identity (IMSI, International mobile subscriber identity), Electronic Serial Number (ESN, ElectronicSerial Number) and so on. When a terminal initiates a call, is called, sends a short message, or registers with the network to access the system, the terminal needs to be authenticated. Authentication refers to the process of exchanging information between the mobile station and the network to verify the legitimacy of the mobile station. An authentication algorithm should be used for authentication. This article uses the authentication CAVE algorithm of a CDMA mobile phone as an example to illustrate. In the CAVE authentication algorithm, this paper only involves several important parameters related to the present invention, the ESN (PESN) of the terminal, the IMSI of the card, and the RUIMID (or EUIMID) of the card, n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com