Computer security system and method thereof
A computer security, computer technology, applied in computer security devices, computing, protection of internal/peripheral computer components, etc., can solve problems such as computer data storage leakage, achieve reliable use of computer information security, protect information security requirements, and facilitate Internet search Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
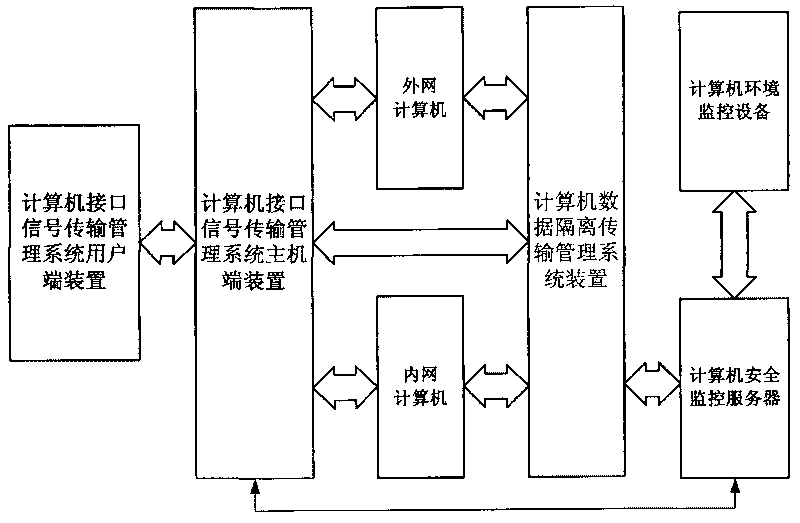
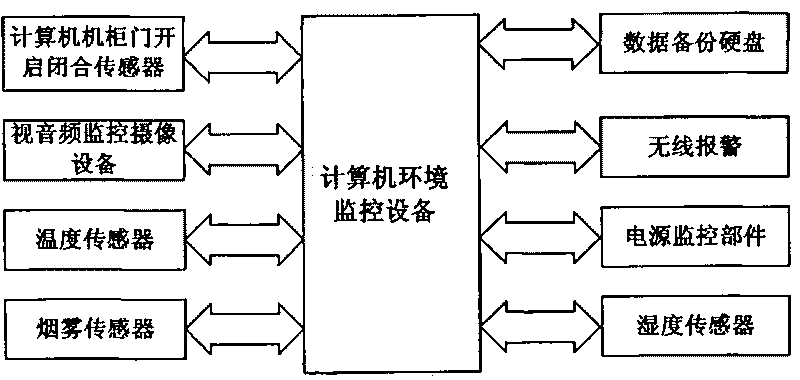
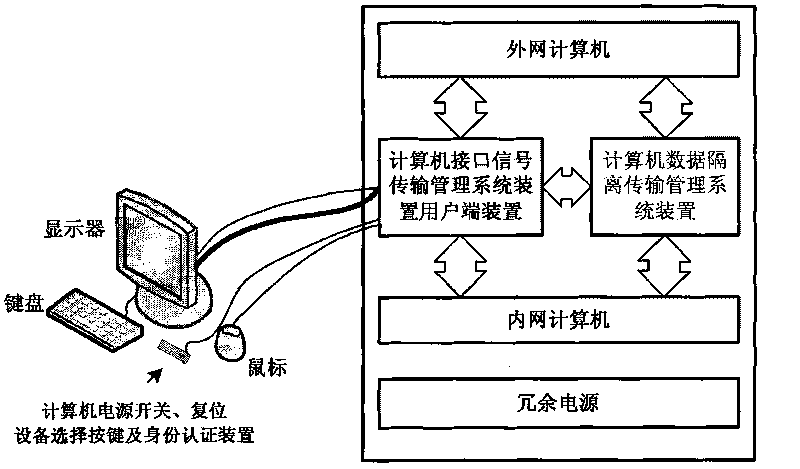
[0043] figure 1 computer information security system, including: computer interface signal transmission management system host device, computer interface signal transmission management system client device, computer data isolation transmission management system device, computer security monitoring server, computer environment monitoring equipment, external network computer, Intranet computer. Among them, the host device of the computer interface signal transmission management system is bidirectionally connected with the client device of the computer interface signal transmission management system, the computer data isolation transmission management system device, the external network computer, the internal network computer, and the computer security monitoring server;
[0044] The computer data isolation transmission management system device is bidirectionally connected with the external network computer, the internal network computer, and the computer security monitoring serv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com