Method and device for detecting SSL enciphered data safety
An encrypted data and security technology, which is applied in the field of detecting the security of SSL encrypted data, can solve the problems of encrypted data analysis and inability to detect intrusion behavior, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
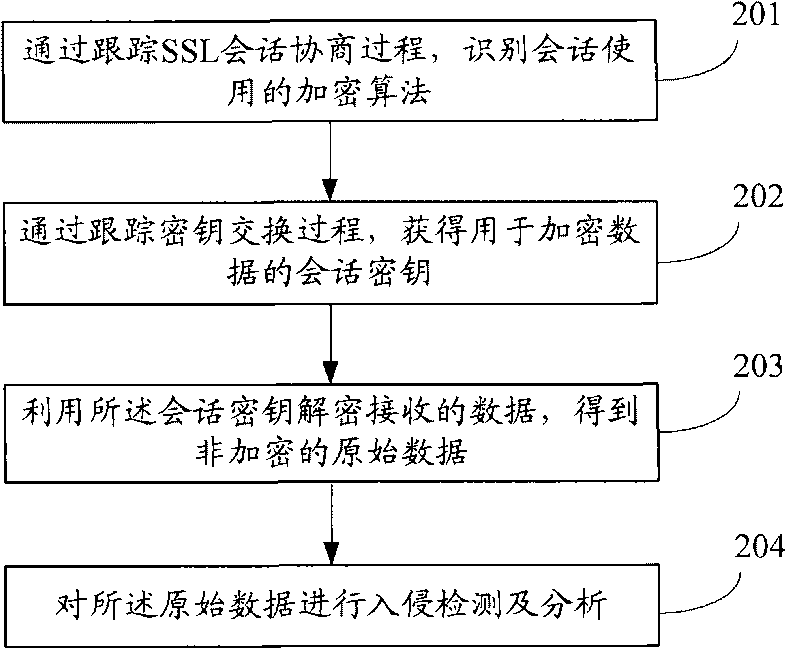
[0051] In order to enable those skilled in the art to better understand the solutions of the embodiments of the present invention, the embodiments of the present invention will be further described in detail below in conjunction with the drawings and implementations.
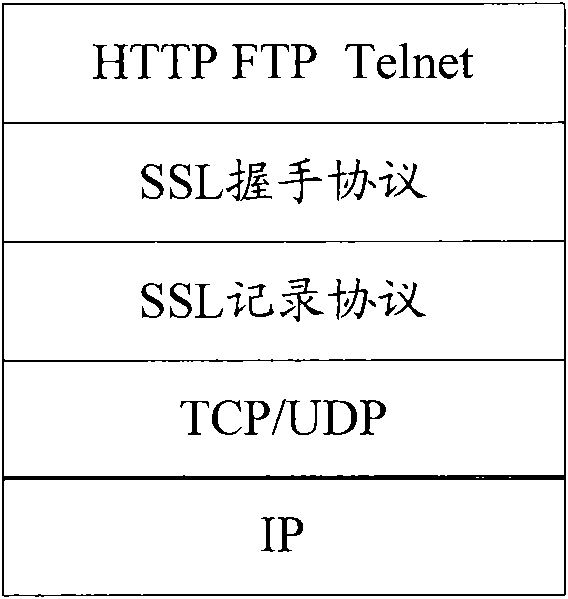
[0052] The following first briefly describes the working process of SSL.
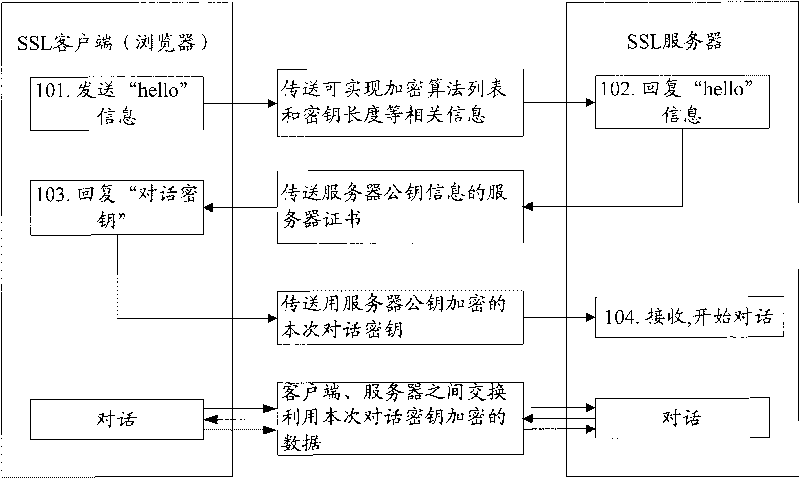
[0053] Such as figure 1 As shown, the SSL workflow is mainly divided into the following two processes:
[0054] 1. Session negotiation process:
[0055] 101. The client sends a start message "Hello" to the server to start a new session connection;
[0056] 102. The server determines whether a new master key needs to be generated according to the client's information. If necessary, the server will include the server certificate used to transmit the server public key information when responding to the client's "Hello" message;
[0057] 2. Key exchange process:
[0058] 103. The client generates a session key based on the received server...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com