Secure authentication of electronic prescriptions
一种电子处方、全部的技术,应用在应用密码术领域,能够解决黑客攻击、医生或者患者隐私侵害、第三方破坏等问题
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
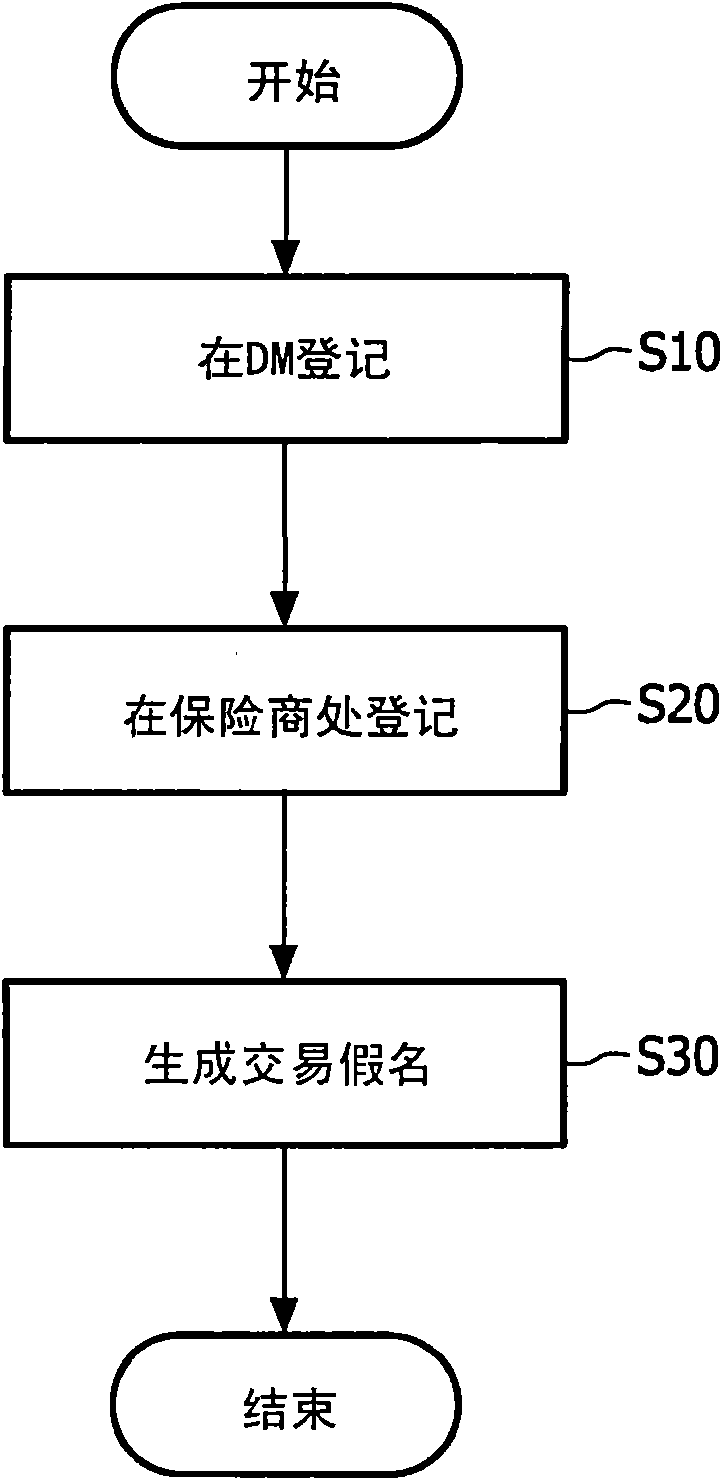
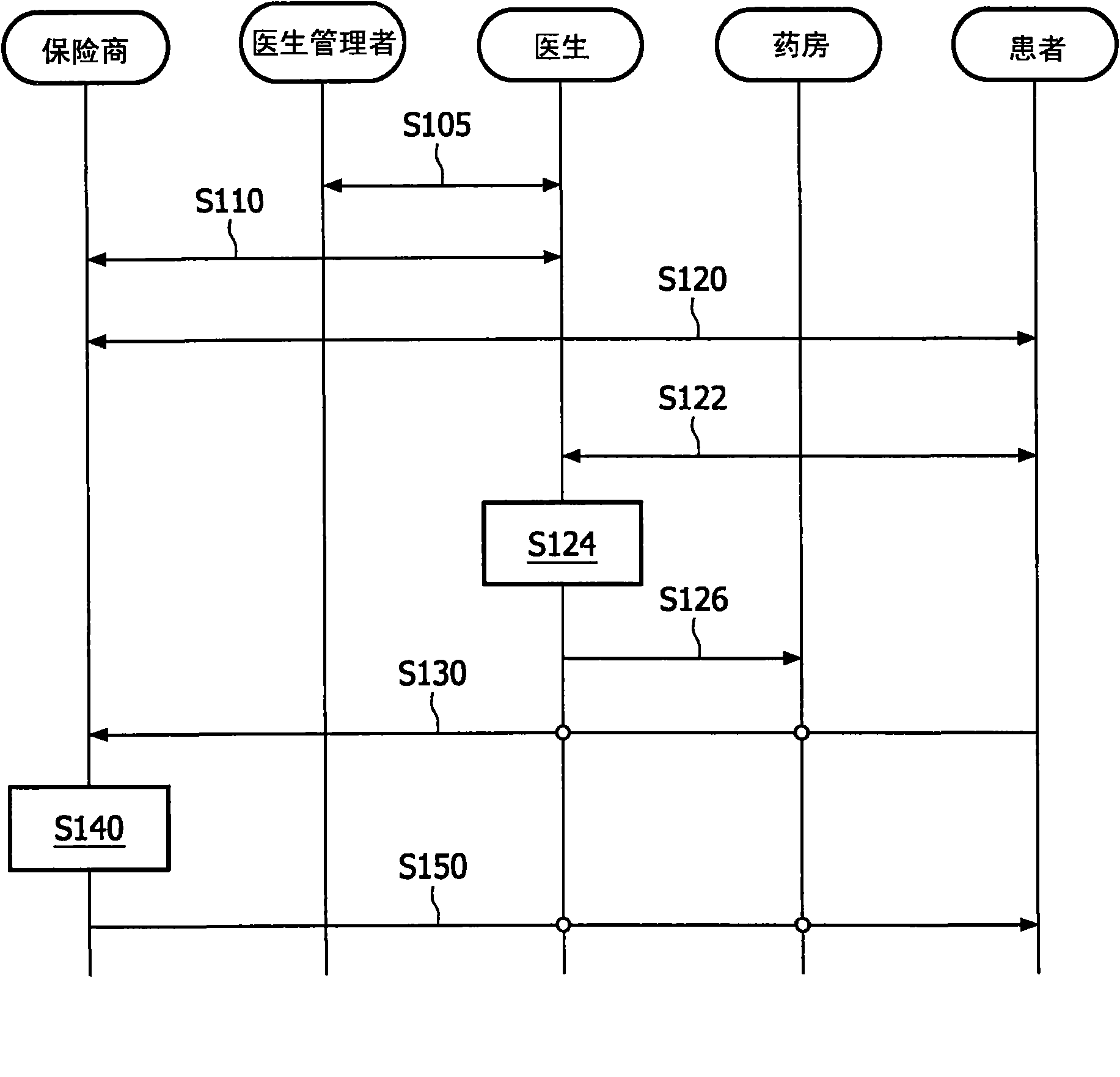
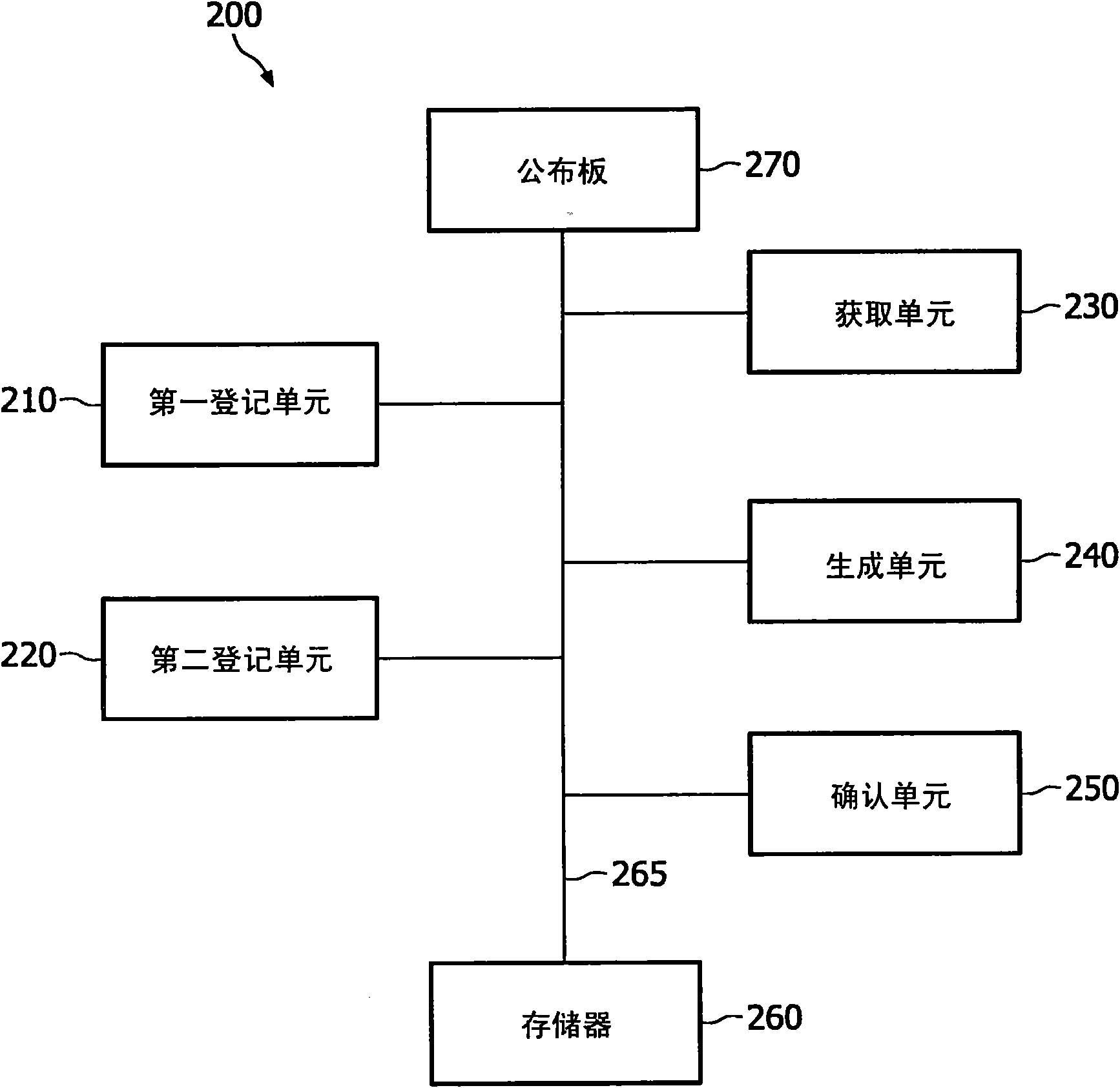
[0024] figure 1 is a flowchart illustrating an embodiment of a method for generating transaction pseudonyms according to the present invention. First, a participant such as a pseudonym user registers at a first privacy management official (for example, a doctor manager (DM)), so that the participant's identity can be uniquely defined and determined by the first pseudonym (S10), and then the participant registers at Registration at a second privacy management officer (for example, an insurance company) to uniquely determine the participant's identity (S20) by mapping the registration key shared between the second privacy management officer and the participant to the first pseudonym; and A transaction pseudonym for the participant is generated based on the first pseudonym, the registration key, and the transaction number linked to the transaction (S30).
[0025] In step S10 of the process according to the method of the invention, a first pseudonym is generated based on the publ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com