Method for information security device for binding network software
A technology of information security and network software, applied in the field of information technology security, can solve the problems of legal online game player loss, insecure identity authentication methods, and easy identity counterfeiting, so as to avoid account theft, improve security, and effectively manage Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
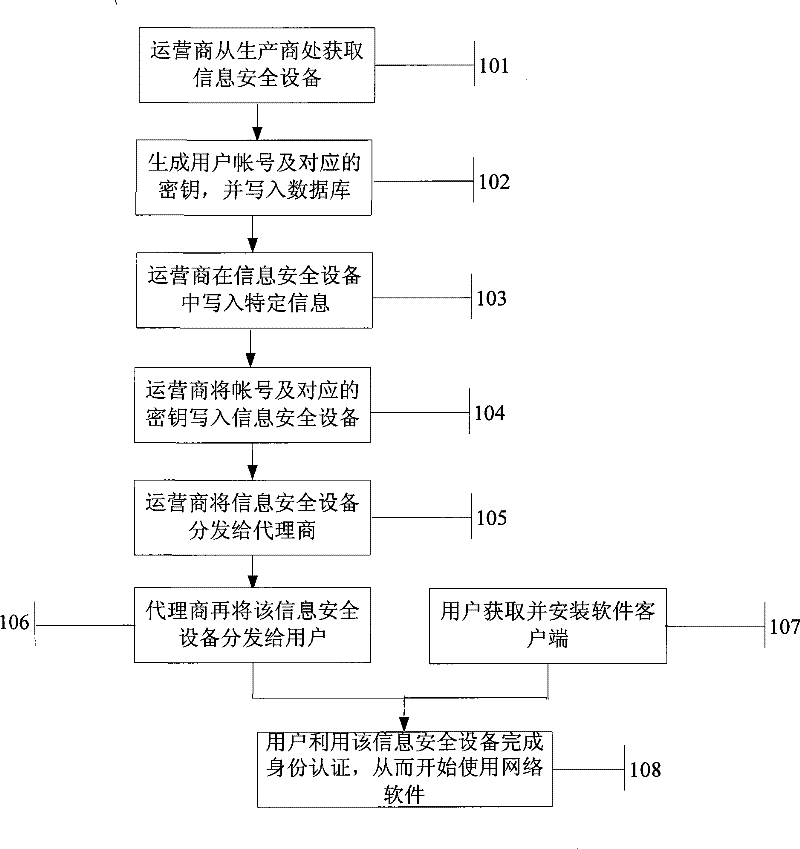
[0031] Such as figure 1 As shown, a method for bundling network software with an information security device includes the following steps.
[0032] Step 101: The operator obtains information security equipment from the manufacturer.
[0033] Operators can purchase information security equipment in bulk from hardware manufacturers.
[0034] Step 102: The operator generates a user account and a corresponding key, and writes it into a database.
[0035] The operator generates the user's account and the corresponding key, and writes it into the database on the server side to complete the binding of the account and key with the software.
[0036] Step 103: The operator writes specific information in the information security device.
[0037] After obtaining the information security device, the operator writes network software feature information and / or operator feature information into it.
[0038] Step 104: The operator writes the account number and the corresponding key into t...
Embodiment 2
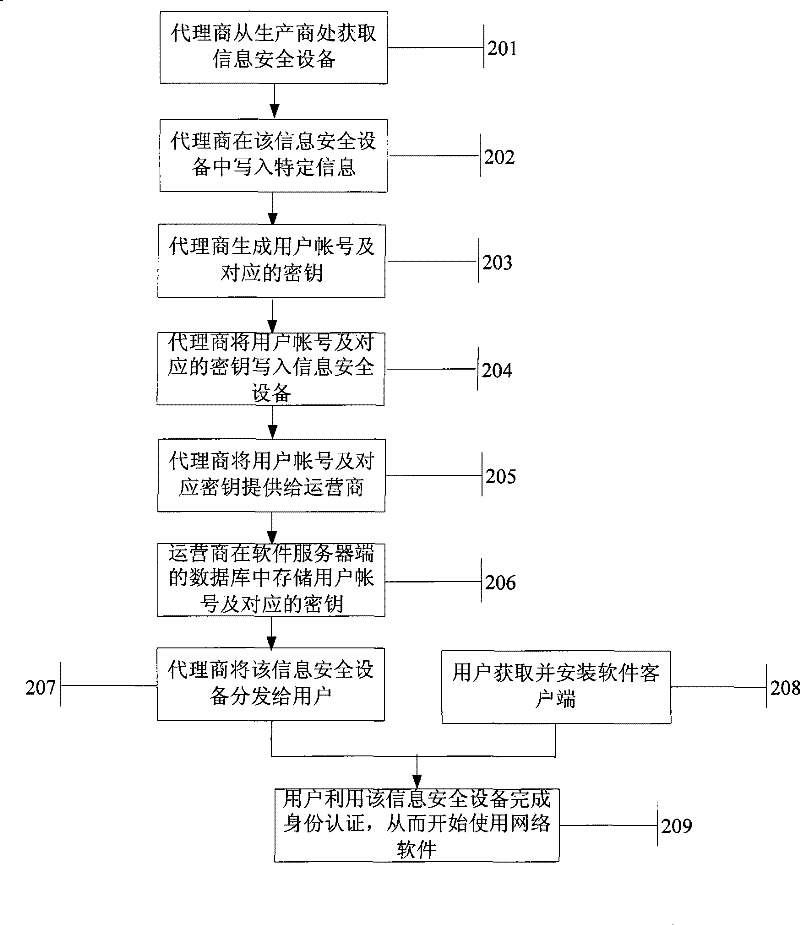
[0049] Such as figure 2As shown, a method for bundling network software with an information security device includes the following steps.
[0050] Step 201: the agent obtains information security equipment from the manufacturer.
[0051] Agents can purchase information security equipment in bulk from hardware manufacturers and pay corresponding fees.
[0052] Step 202: The agent writes specific information in the information security device.
[0053] The agent writes the characteristic information of the network software in the information security device, and may also write the characteristic information of the agent.
[0054] Step 203: Generation of user accounts and corresponding keys.
[0055] The user's account number and the key corresponding to it can be generated at the agency.
[0056] Step 204: Write the account number and the corresponding key into the information security device.
[0057] The agent writes the generated user account and the corresponding key i...
Embodiment 3
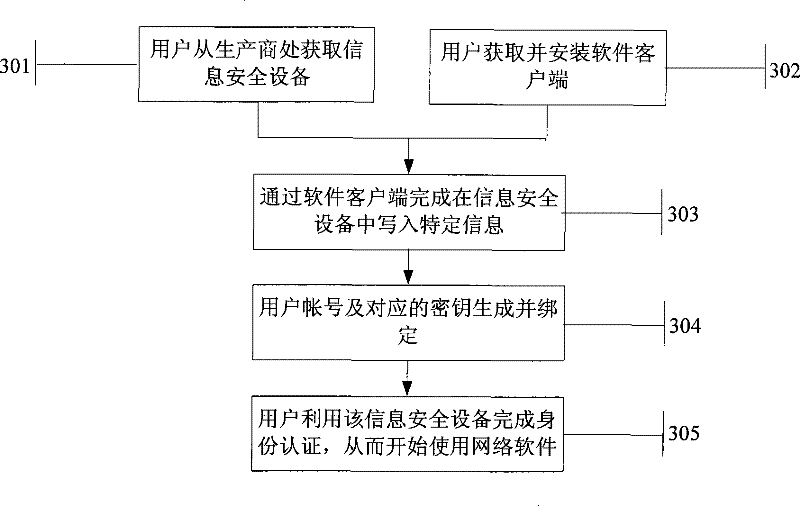
[0069] Such as image 3 As shown, a method for bundling network software with an information security device includes the following steps.
[0070] Step 301: A user obtains an information security device from a manufacturer.
[0071] Users directly purchase information security equipment from hardware manufacturers and pay corresponding fees.
[0072] Step 302: the user acquires and installs the software client.
[0073] Users can obtain the software client program by purchasing an installation CD or downloading it from the Internet, and then install it on their own computers according to the relevant prompts.
[0074] Step 303: the client writes specific information in the information security device.
[0075] Write the network software feature information in the information security device through the software client.
[0076] Step 304: Generate a user account and a corresponding key, and complete the binding.
[0077] The client program accesses the information securit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com