A Watermark Embedding and Authentication Method for Digital Image
A technology of digital image and watermark embedding, applied in image coding, image data processing, image data processing and other directions, can solve the problems of watermark robustness to be further improved, feature vector computational complexity reduced, etc., to achieve good invisibility and authentication. Reliable and robust results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be further described below in conjunction with the accompanying drawings.
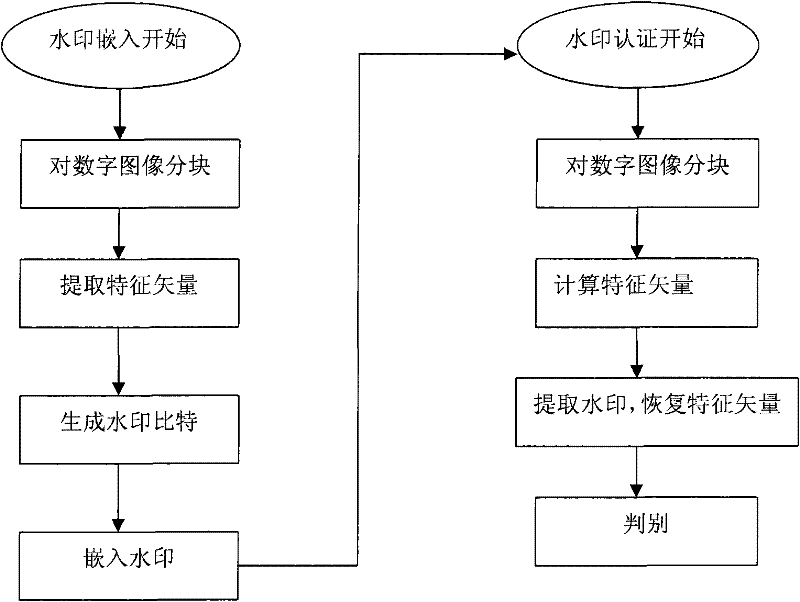
[0024] The processing flow of the present invention is as attached figure 1 As shown, it includes two steps of watermark embedding and watermark authentication, and the watermark embedding includes the following sub-steps:
[0025] (1) Divide the digital image into two non-overlapping regions by block—the feature region and the watermark region;
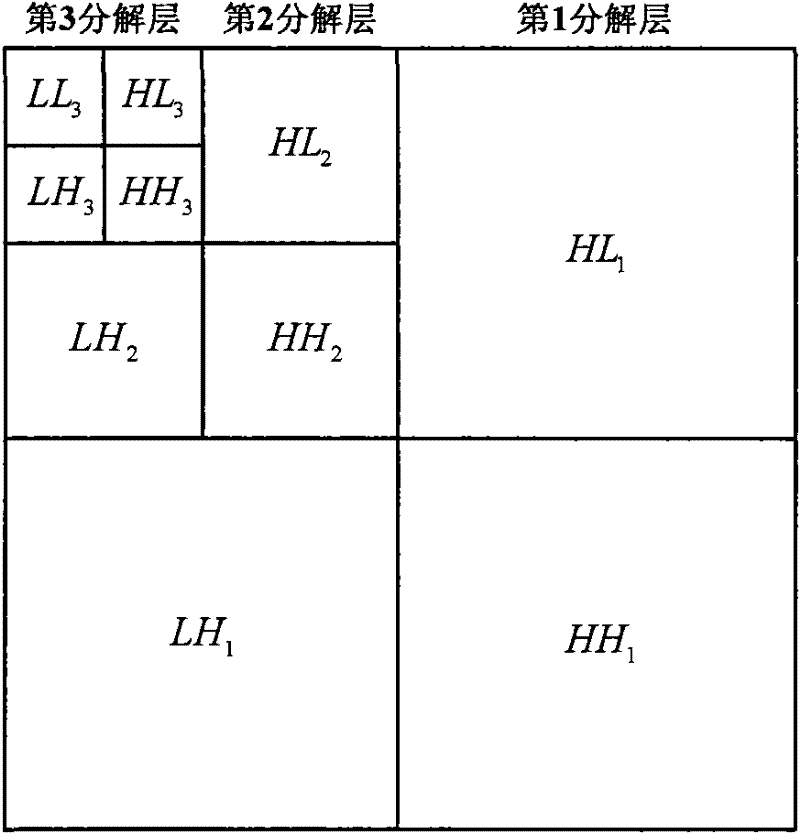
[0026] (2) extract the feature vector in the DWT-DCT double transform domain of feature area;
[0027] (3) the eigenvector quantization of the real number that step (2) obtains is watermark bit;
[0028] (4) Embedding the watermark into the watermark area;
[0029] The watermark authentication includes the following sub-steps:
[0030] (5) Divide the digital image into two non-overlapping regions using a partition method consistent with step (1);
[0031] (6) Calculate the feature vector of the feature area;
[0032] (7...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com