Method and system for realizing boundary service of cross base station controller
A technology of a base station controller and an implementation method, applied in the field of communication, can solve the problems of users in the border area being unable to make calls, and achieve the effect of reducing the capacity load
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0035] Example 1: Calls made across BSC borders
[0036] In this example, the process of initiating a call across the boundary of a BSC will be described, and the process of initiating a service call is implemented in conjunction with the process of soft handover between A3\A7 BSCs.
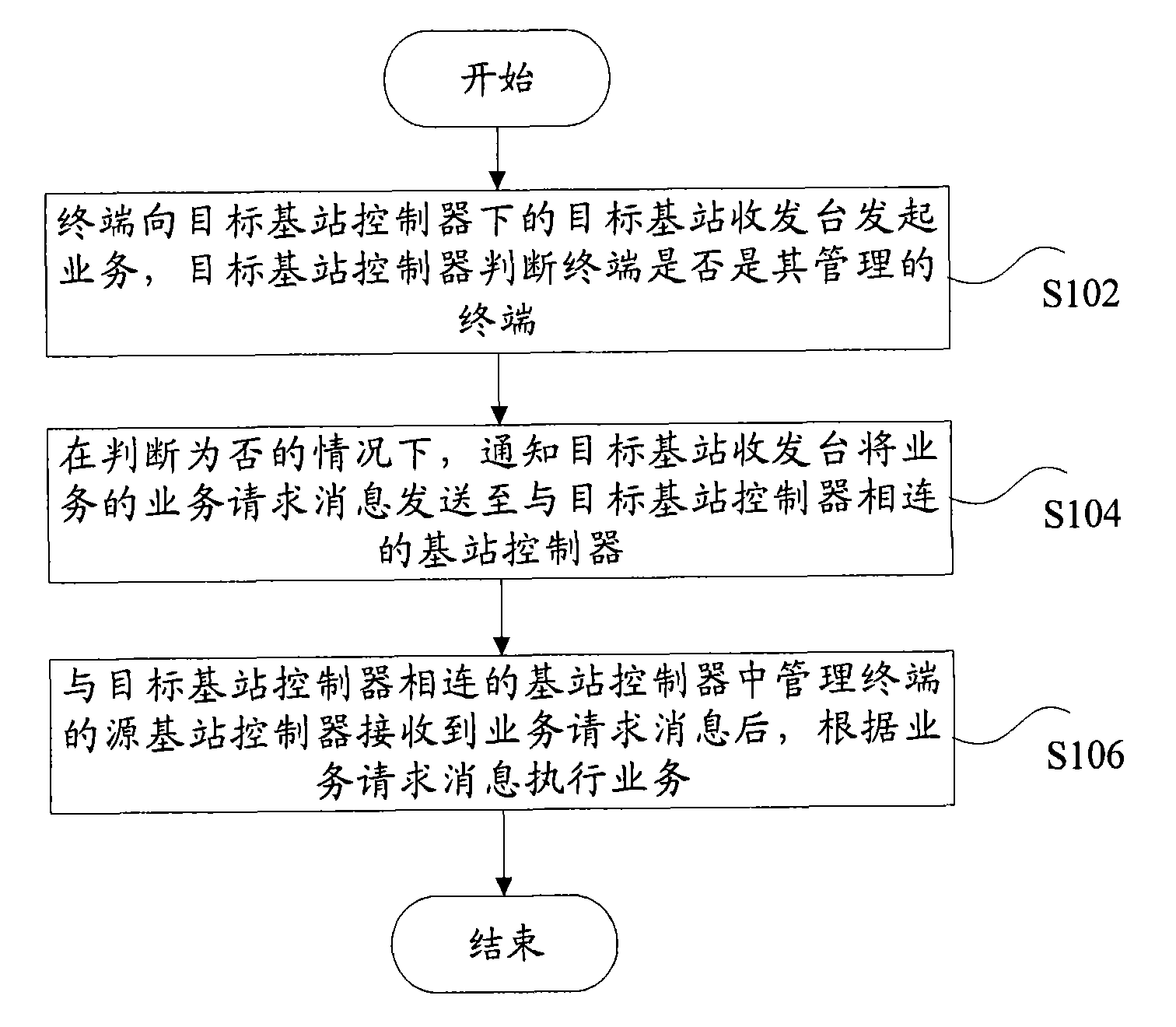
[0037] figure 2 Shows the cross-BSC calling process, which specifically includes the following steps:
[0038] Step 201, the MS terminal initiates a call at the target T_BTS, and the target BTS sends a confirmation message of the base station after receiving the call initiation message, and simultaneously constructs an abisc access message to the target T_BSC;
[0039] Step 202, after the target T_BSC receives the Abisc access message, it judges that it is not a user managed by the BSC, that is, the BSC does not maintain the information for this use, and then sends an A7 access message to all interconnected BSCs;
[0040] Step 203, after the source side S_BSC receives the A7 access message, it...
example 2
[0049] Example 2: Inter-BSC paging call flow
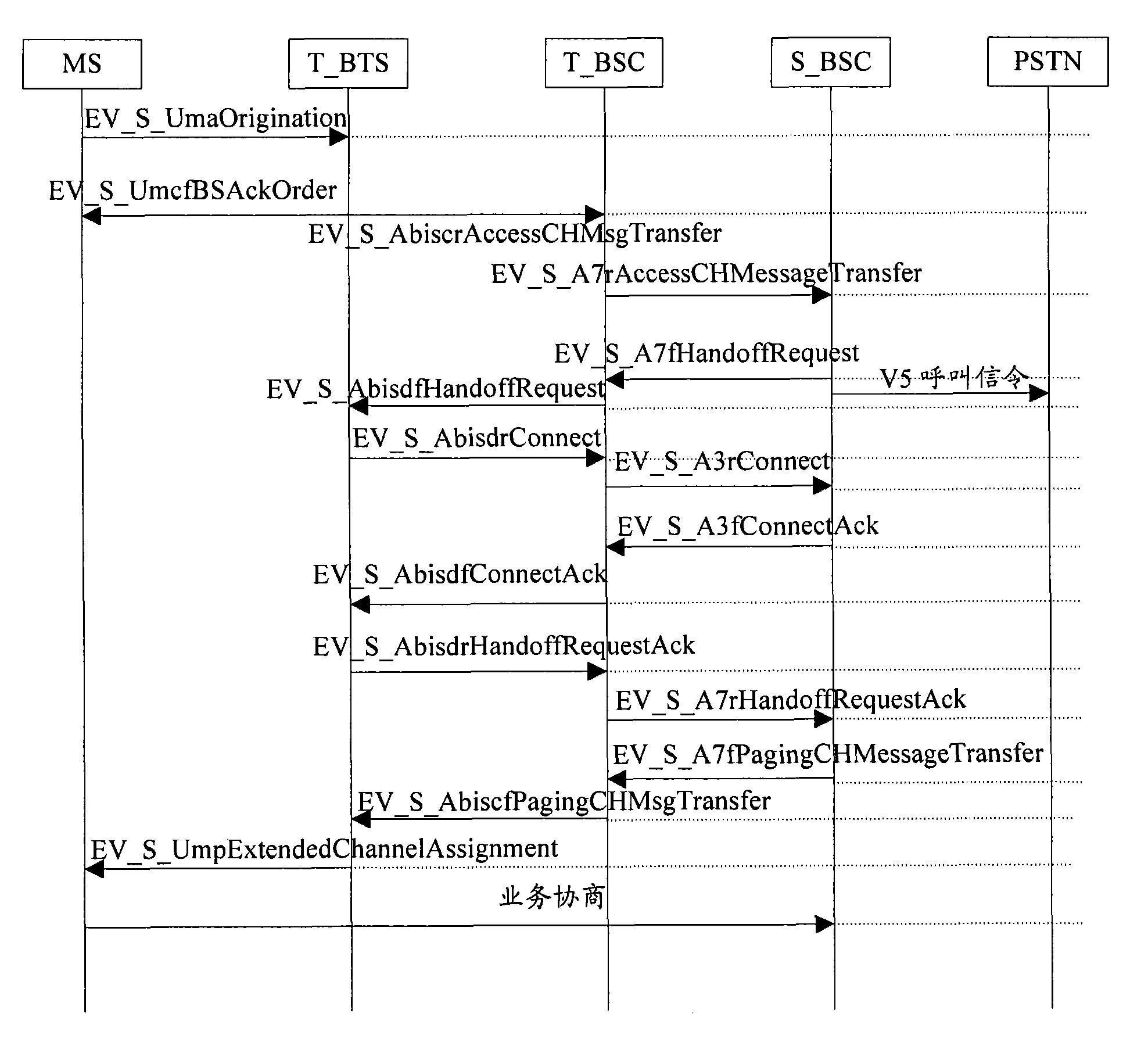
[0050] For the process of inter-BSC paging call processing, please refer to image 3 , the specific steps are as follows:
[0051] Step 301, after the V5 called signaling from the PSTN arrives at the source side S_BSC, the BSC sends the paging signal to the S_BSC according to the latest registration information of the user in the VLR module or the cell location information of the calling record (information that can identify which BSC it belongs to). The request is sealed in A7fPagingCHMessageTransfer and sent to the target T_BSC;
[0052] Step 302, after receiving the A7fPagingCHMessageTransfer, the target T_BSC converts it into an AbiscfPagingCHMsgTransfer message and sends it to T_BTS, and then T_BTS constructs a real air interface paging message and sends it to the terminal MS;
[0053] Step 303, the terminal responds after receiving the paging request message, sends a paging response message to the target T_BTS, the base st...
example 3
[0055] Example 3: Cross-BSC registration process
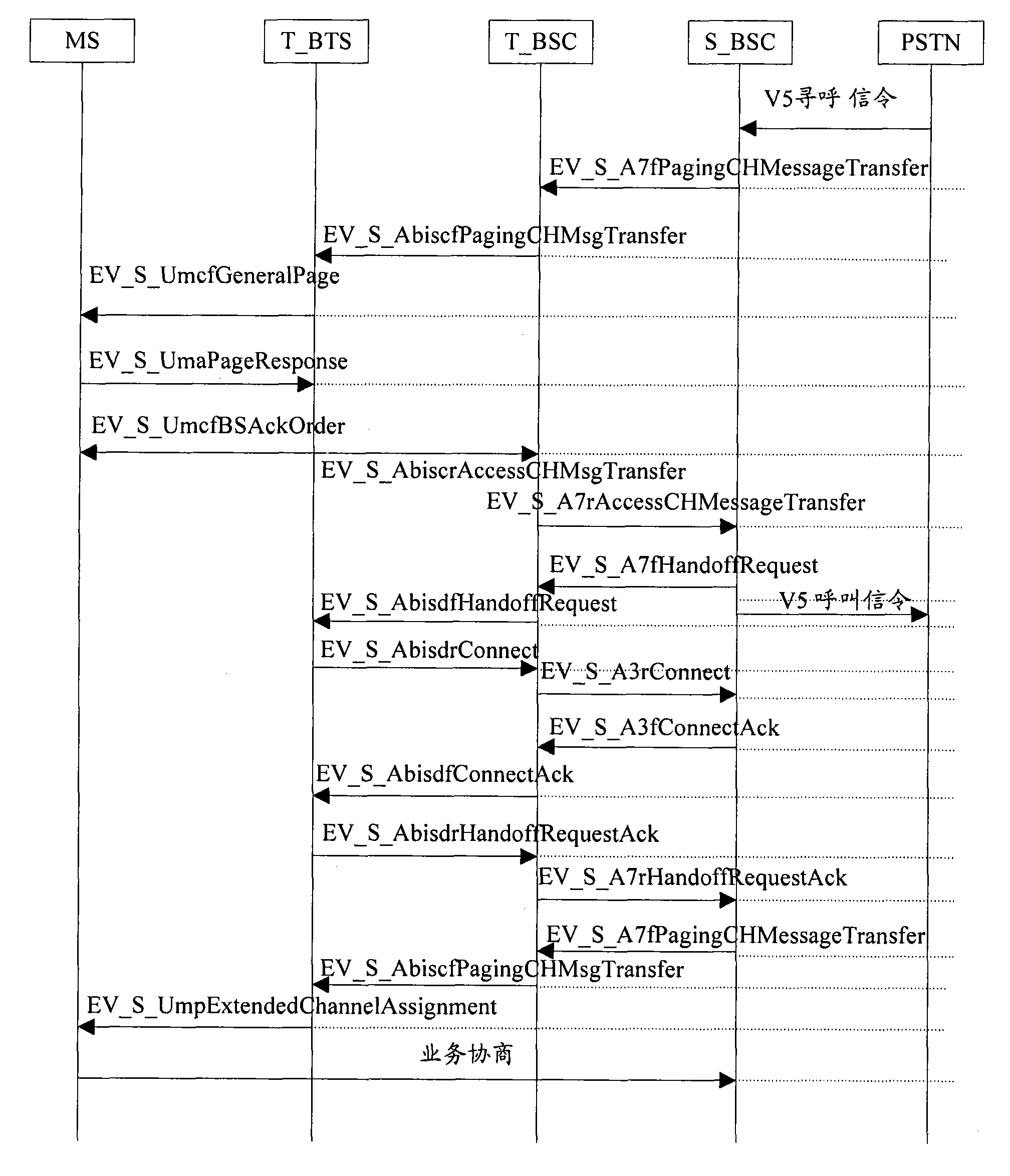
[0056] For the process of cross-BSC registration, please refer to Figure 4 , which specifically includes the following steps:
[0057] Step 401, when the target T_BTS receives the air interface registration message sent by the terminal MS, it sends the abisc access message AbiscrAccessCHMsgTransfer to the T_BSC;
[0058] Step 402, after receiving the abisc access message, the target T_BSC judges that it is not a user of this BSC according to the VLR module of the IMSI in the BSC, that is, the BSC does not maintain the information for this use, and then sends an A7 access message to all interconnected BSCs A7rAccessCHMessageTransfer;
[0059] Step 403, after receiving the A7 access message, the S_BSC on the source side records the information carried in the registration message in the VLR module of the BSC, and updates the cell location information; at the same time, the registration acceptance message is encapsulated in the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com