Method, system and device for P2P service access
A service access and service technology, applied in the field of communication, can solve problems such as inability to meet information security, increase operator operating costs, and reduce user satisfaction, so as to reduce bandwidth and cost requirements, reduce DPI processing burden, and reduce data traffic Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
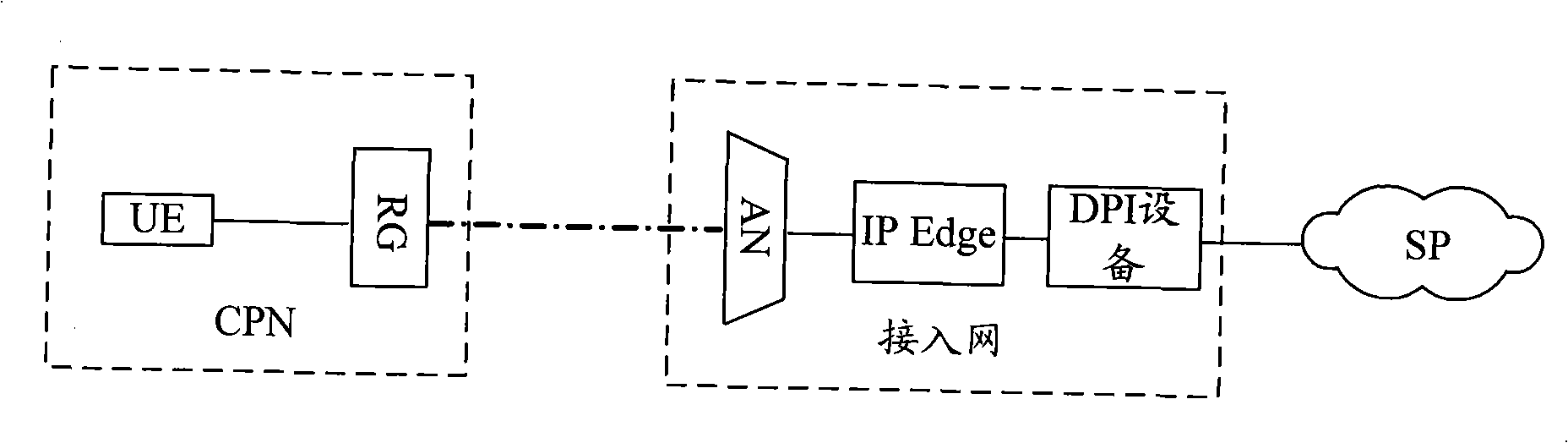
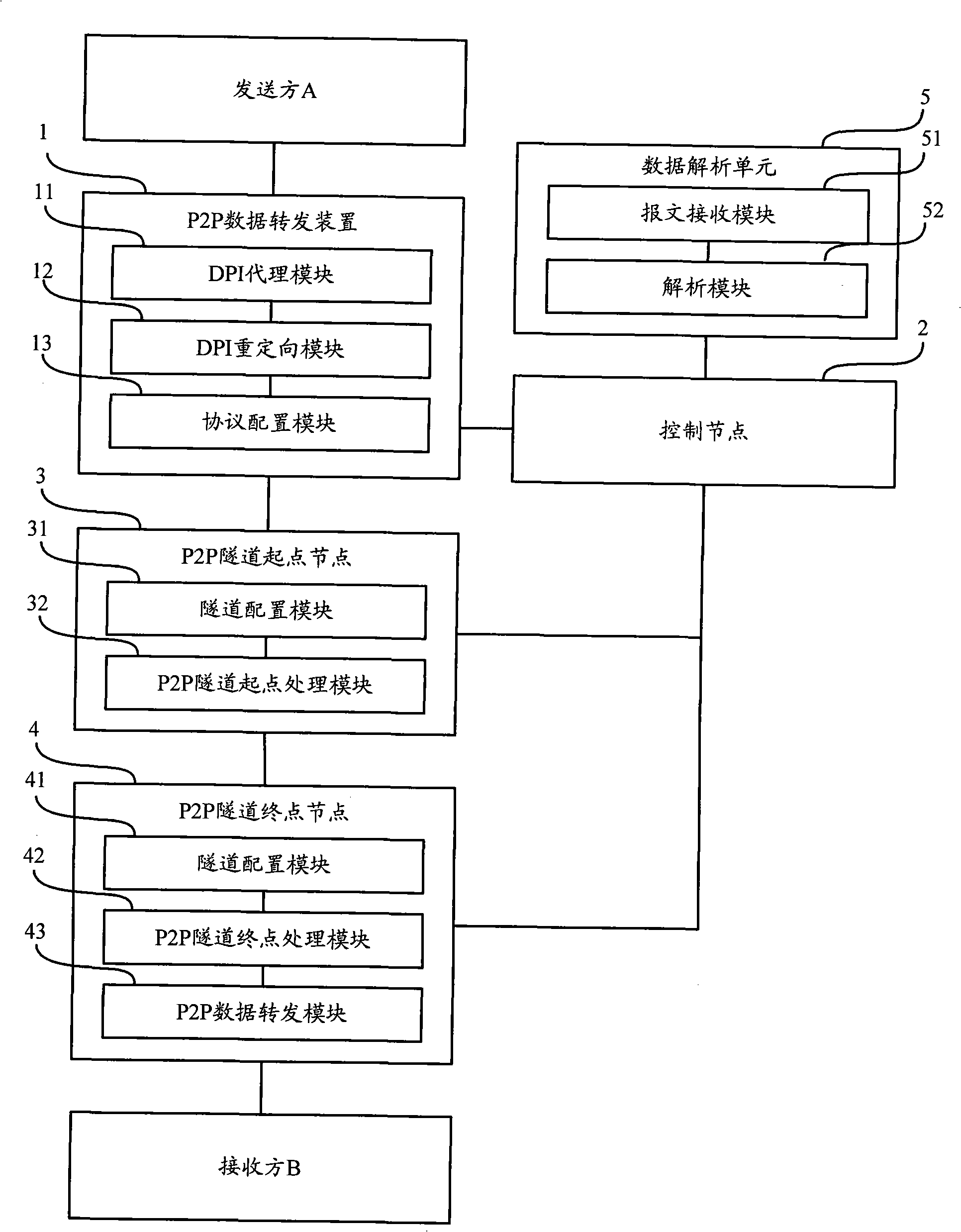
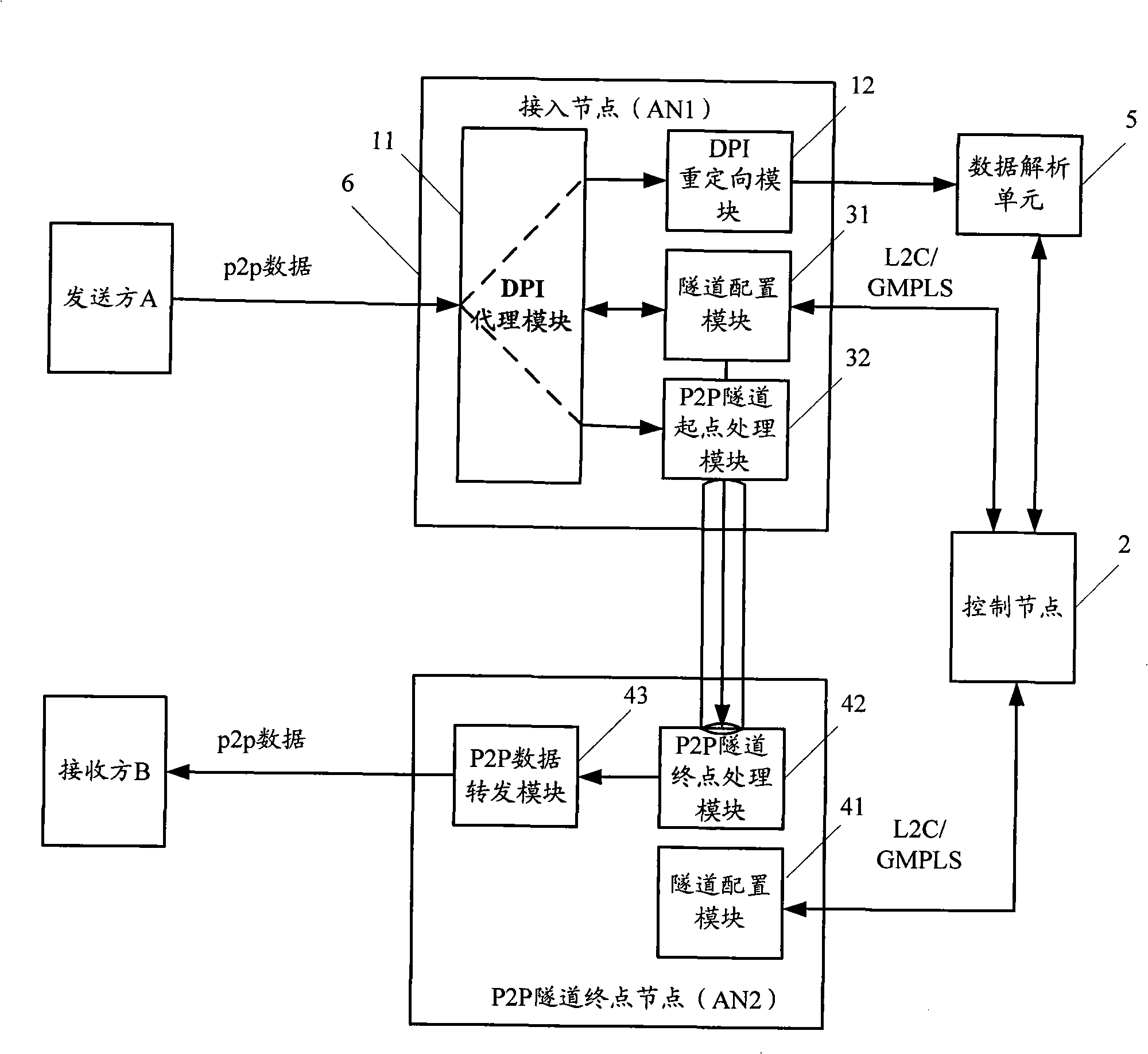
[0074] Such as Figure 4 As shown, it is the second embodiment of the present invention, a flow chart of a P2P service access method for DPI analysis to terminate P2P transmission. For the convenience of description, in this embodiment, the access node 6 is called AN1, and AN2 is called AN2 , AN1 and AN2 are collectively referred to as P2P tunnel path nodes.
[0075] Specifically include the following steps:
[0076] P2P tunnel establishment phase:
[0077] Step S401, sender A sends a P2P data packet to AN1.
[0078] In step S402, the DPI proxy module 11 of AN1 recognizes that the packet from sender A is a P2P data packet through flow classification and / or DPI filtering.
[0079] Step S403 , redirecting the P2P data message to the data parsing unit 5 .
[0080] Step S404, the data analysis unit 5 performs DPI analysis on the P2P data or signaling message, identifies the application service type and content of the corresponding flow or analyzes the P2P signaling, and finds ou...
Embodiment 3
[0104] Such as Figure 5 As shown, it is a flowchart of a P2P service access method for signaling to terminate P2P transmission in Embodiment 3 of the present invention. For the convenience of description, in this embodiment, the access node 6 is called AN1, and AN2 is called AN2 , AN1 and AN2 are collectively referred to as P2P tunnel path nodes.
[0105] Specifically include the following steps:
[0106] P2P tunnel establishment phase:
[0107] Step S501, sender A's P2P data message is uploaded to AN1.
[0108] In step S502, the DPI proxy module 11 of AN1 recognizes that the packet from sender A is a P2P data packet through flow classification and / or DPI filtering.
[0109] Step S503 , redirecting the P2P data packet to the data parsing unit 5 .
[0110] Step S504, the data parsing unit 5 parses the P2P signaling message.
[0111] Step S505 , according to the DPI-related policy, send the P2P tunnel and policy configuration command to the control node 2 .
[0112] Step ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com