Cross-certification method based on seed key management
A cross-certification, key management center technology, applied in the field of public key cryptography and authentication, can solve the problems of complex and complex social application requirements, difficult to support, etc., achieve a concise architecture, ensure authenticity and security, and trust relationship. clear effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
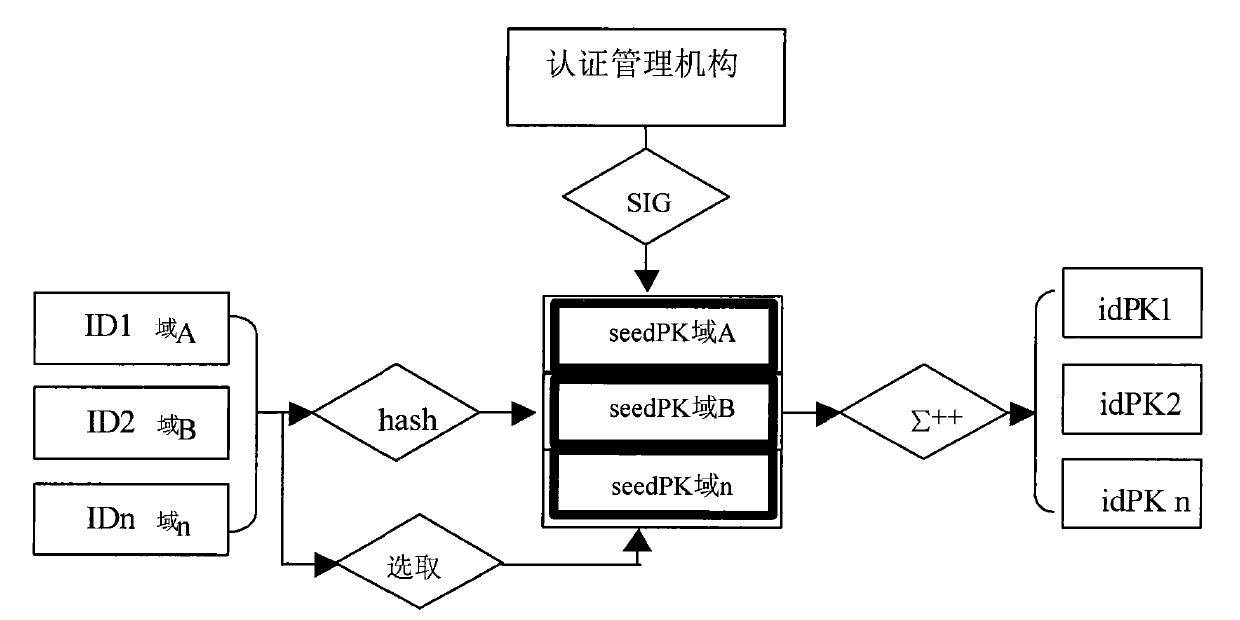
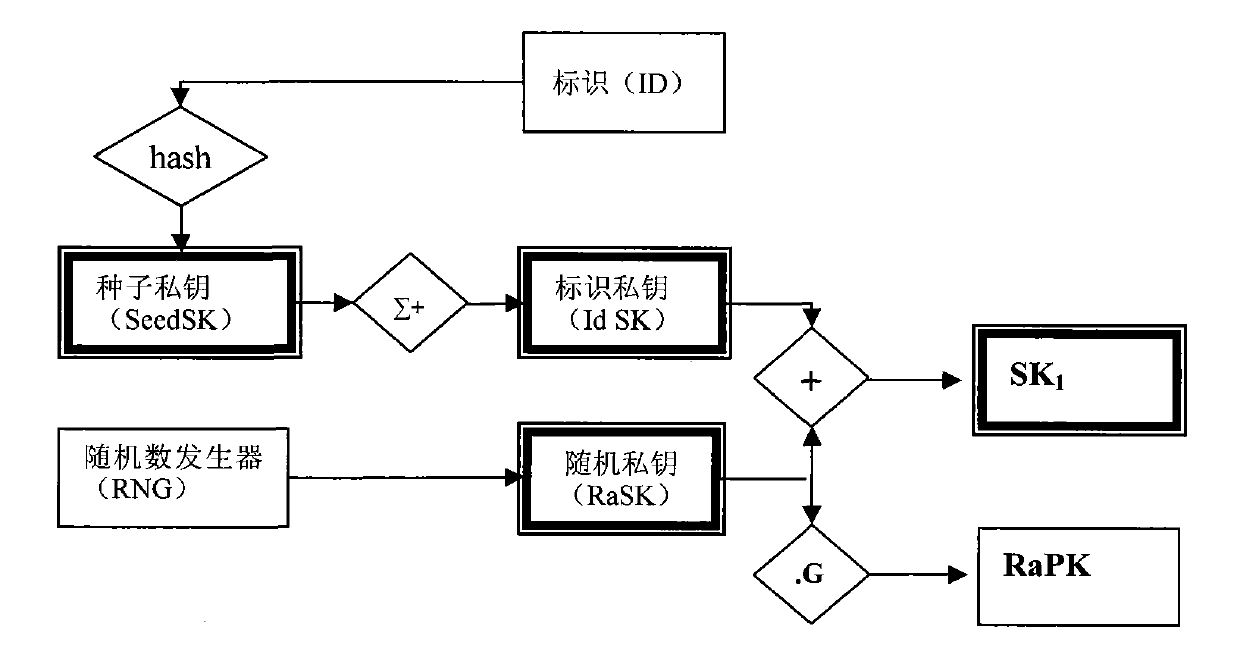
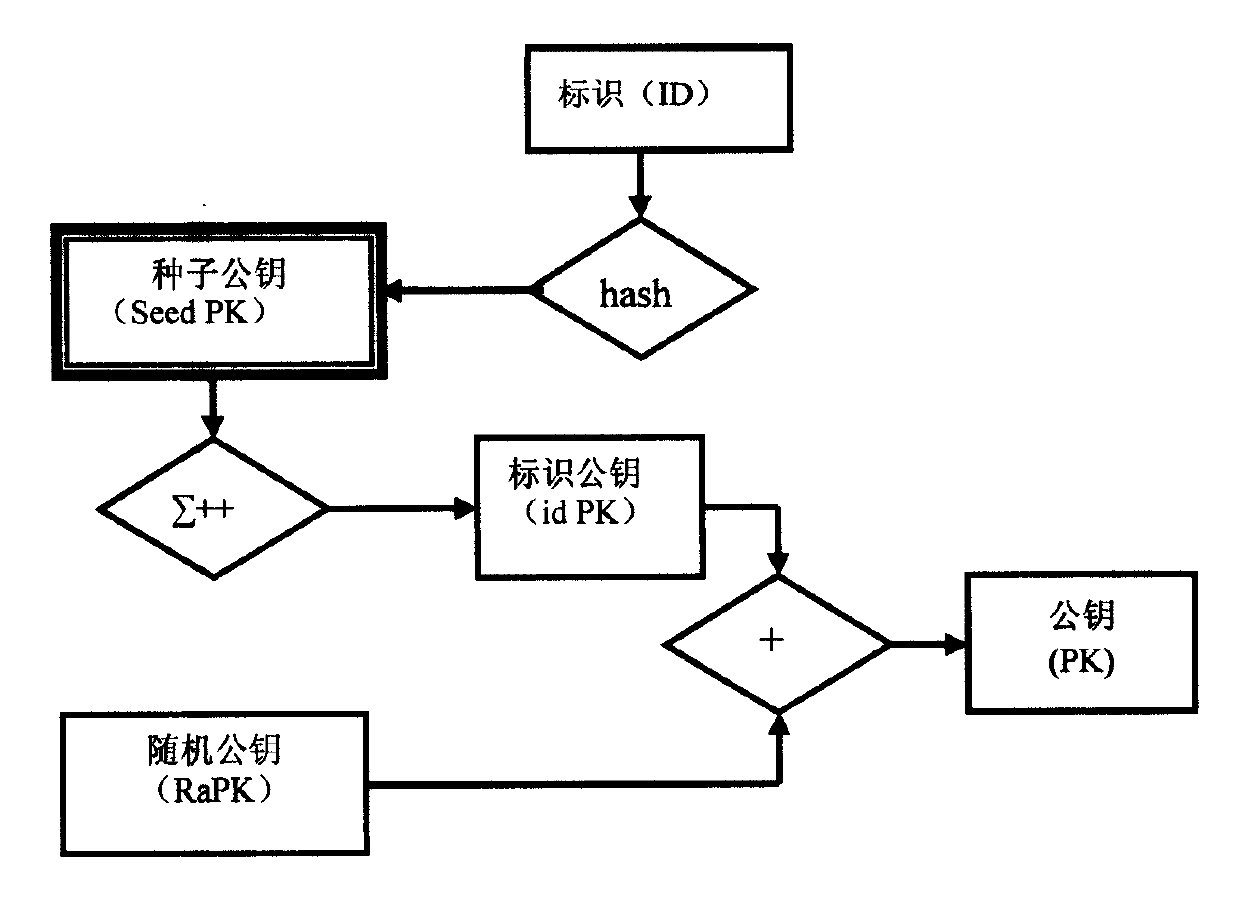
[0043] The cross-authentication method proposed by the present invention is formed by increasing the management of the seed public key on the basis of the CPK and TF-CPK systems. In view of the fact that the user's public key in the TF-CPK system is composed of two independent public keys—the identification public key and the random public key, the modification of the TF-CPK in the present invention is limited to the generation of the random public key and the two-factor composite public key part.
[0044] The following levels are set here:
[0045] 1) Certification management organization (cross-certification management department), which is equivalent to the root CA in the PKI hierarchical certification system;
[0046] 2) The trust domain management department (key management center) is specifically responsible for the management of the trust domain, and can also establish bilateral and multilateral cross-certification relationships with other key management centers by its...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com