Group key management method base spherical surface in N dimension
A technology of group key and management method, which is applied in the field of group key management and can solve problems such as increased overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
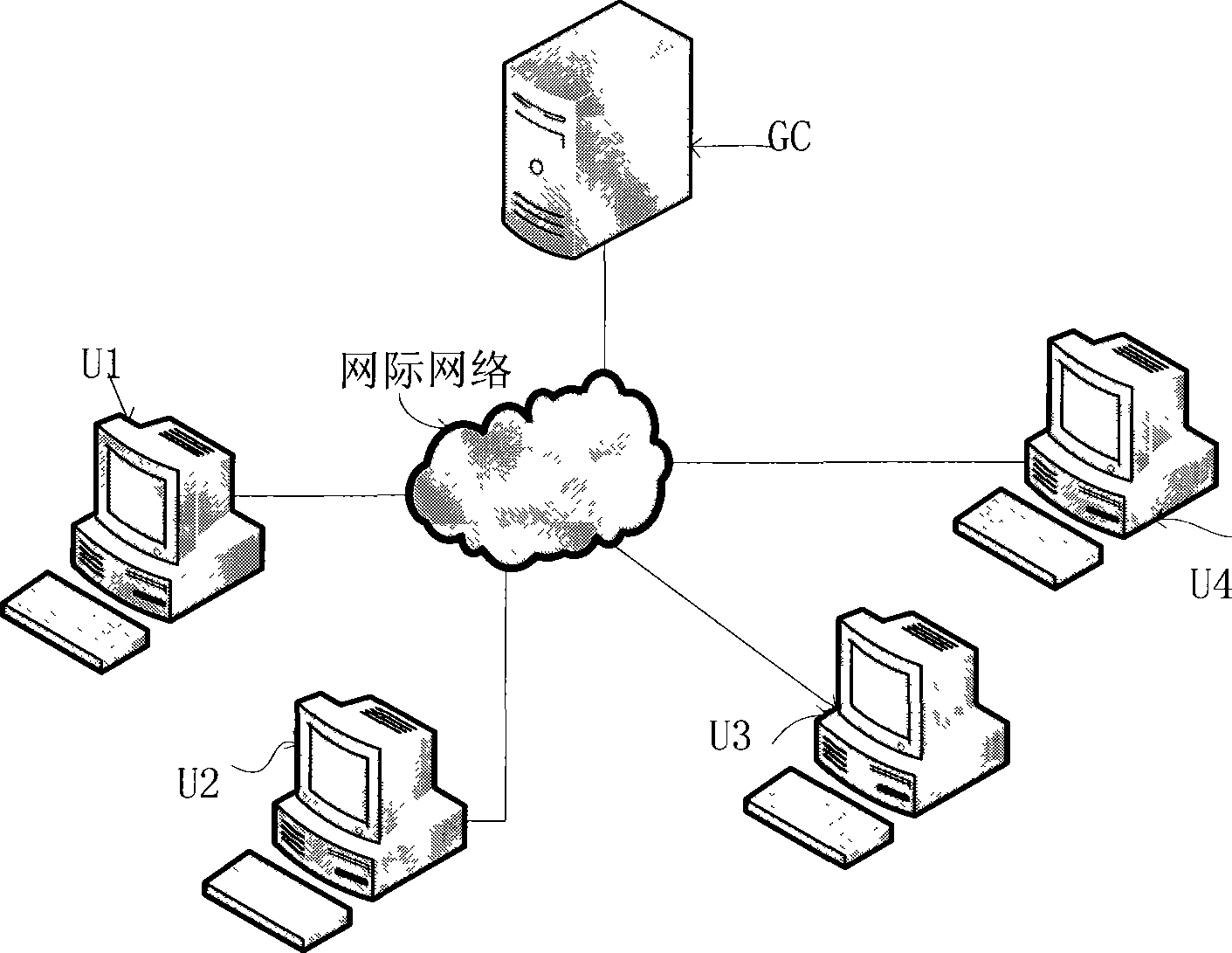
[0098] A typical secure group communication system architecture is as follows: figure 1 As shown, the system includes a group manager (GroupControl, GC) and four group users U1, U2, U3 and U4. The Group Manager (GC), each user is connected through the Internet.
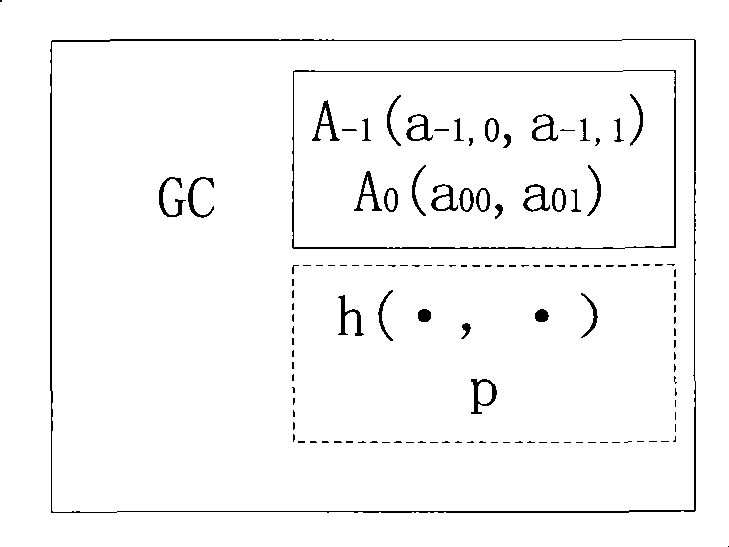
[0099] Such as figure 2 As shown in , after initialization, the group manager (GC) sets relevant parameters, wherein the parameters in the solid line box are kept secret, and the dotted line box are public parameters. The two-dimensional point A in the figure -1 and A 0 is kept secret, the binary hash function h(·,·) and the large prime number p are public, and the entire process of the embodiment is carried out under the finite field GF(p).
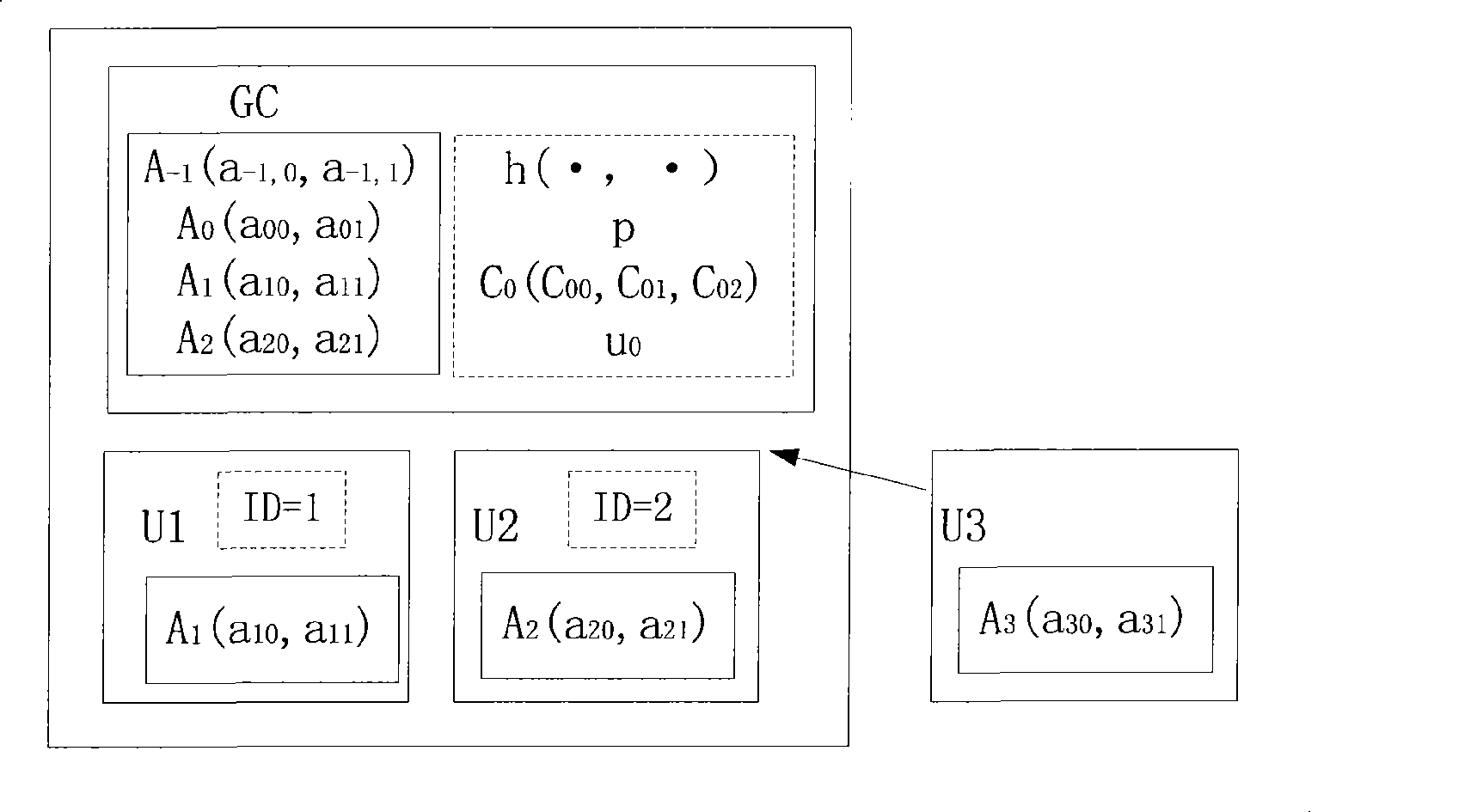
[0100] Such as image 3 As shown, U1 and U2 have formed a group, and now the group is ready to accept U3 to join.
[0101] Among them, U1 is the first user, its joining process: After the group manager (GC) authenticates U1 user, the group manager distributes ID=1 to U1 u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com