Integrated risk computing method and system of computer information system
A technology of comprehensive risk and information system, applied in the field of comprehensive risk calculation method and system of computer information system, which can solve the problems of ignorance and uncertainty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0040] Embodiment 1. utilize the present invention to carry out the specific method and step of risk assessment, such as image 3 shown.
[0041] 1. Step 301 establishes risk level standards:
[0042] The 7-point grade standard for hypothetical definition risk is shown in Table 1.
[0043] Table 1: Risk Level Criteria
[0044] grade factor
Grade symbol
No describe
0 d 1 Ignorable. The occurrence of a risk event has little impact on the system
0.1
d 2 small. Influential but small. Once a risk event occurs, the
10% more value loss.
0.3
d 3 slightly obvious. Can feel the changes caused by the system, but not very strict
Heavy. Once a risk event occurs, at most 30% of the value loss will be caused
lose.
0.5
d 4 medium. can cause damage to the reputation of the system, or
A decrease in trust in the source or service requiring the payment of significant resources to re...
Embodiment 2
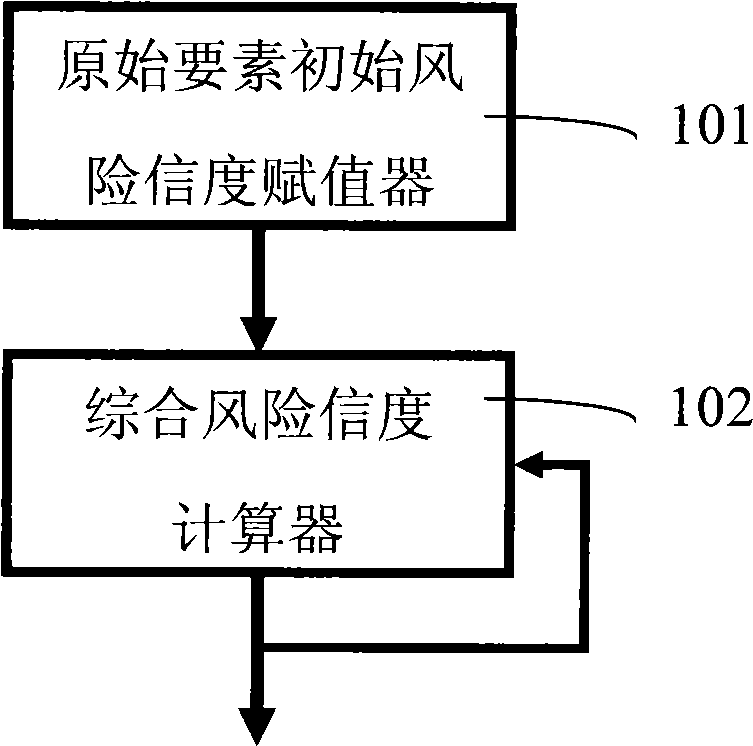
[0061] Embodiment 2. The implementation of the initial risk credit evaluator of the original element (such as Figure 4 ). The evaluator assigns the reliability of the original evaluation elements relative to the established risk level standard based on the evaluation of the original evaluation elements. It includes the following devices:
[0062] 1) The input device 401, which inputs the initial risk assessment value s of the original assessment element and the risk level standard vector D.
[0063] 2) The initial risk reliability calculation unit 402 calculates an initial risk reliability vector of an original assessment element according to the initial risk assessment value of the original assessment element.
[0064] 2) The output means 403, which outputs an initial risk reliability vector of the original evaluation element.
[0065] Assume that the 7-point risk level standard {d 1 , d 2 ,...,d 7}={0, 0.1, 0.3, 0.5, 0.7, 0.9, 1}, if the CVE score s=7.6 of an element,...
Embodiment 3
[0070] Embodiment 3, the implementation of comprehensive risk credibility calculator (such as Figure 5 ). The calculator calculates the comprehensive risk reliability of the evaluation object based on the risk reliability matrix of all evaluation elements and the weight vector of the evaluation elements. It includes the following devices:
[0071] 1) The risk reliability matrix input device 501, which inputs the risk reliability matrix R of the evaluation elements. When the assessment element is the original assessment element, the risk credibility matrix R is the initial risk credibility matrix output by the initial risk credibility evaluator.
[0072] 2) The weight vector input means 502 of evaluation elements, which inputs the weights of all evaluation elements of an evaluation object.
[0073] 3) The comprehensive risk computer device 503 completes the calculation of the comprehensive risk reliability of the evaluation object.
[0074] 4) The risk reliability vector o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com