Method and system for detecting abnegation service aggression
A denial-of-service attack and detection module technology, applied in the field of computer networks, can solve the problems of large space occupation and slow detection speed, and achieve the effect of improving retrieval speed and overcoming the large cost of computing resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
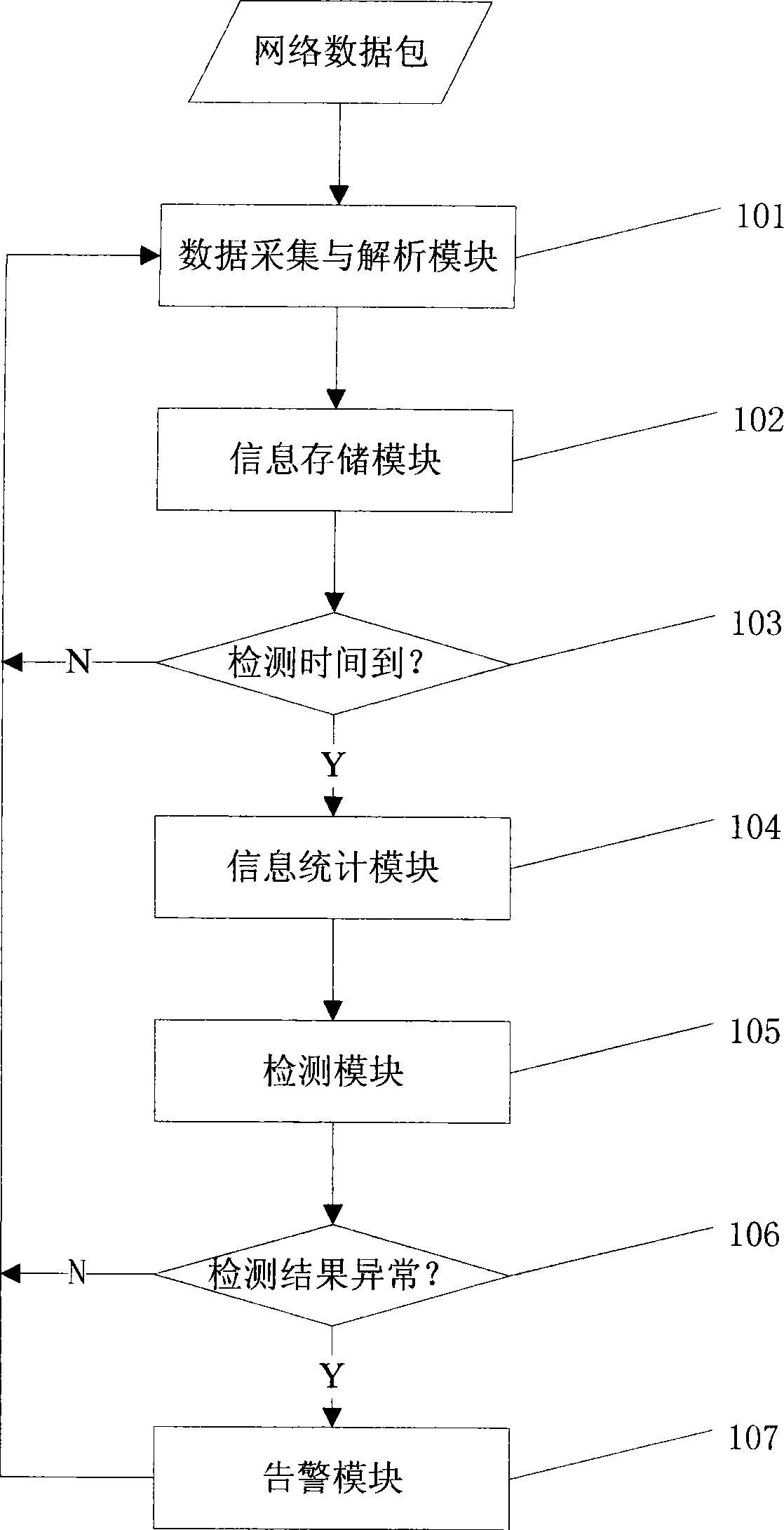
[0025] This embodiment is a basic mode of a method for detecting denial of service attacks. This embodiment can be briefly described as:
[0026] (1) Collect network data and perform space compression storage based on Bloom counting filter;
[0027] (2) periodically counting the data information collected in step (1), and extracting the aggregated information;
[0028] (3) Detect the aggregated information obtained in step (2), and obtain the initiator and / or victim of the denial of service attack.
[0029] The basic idea of realizing this embodiment is: obtain the network data packet and analyze it, extract the source IP, destination IP, source port, destination port in the data packet; classify according to the transport layer protocol type, based on the Bloom counting filter The source IP, the destination IP, the corresponding relationship between the source IP and the destination port, the relationship between the destination IP and the destination port, and the corres...
Embodiment 2
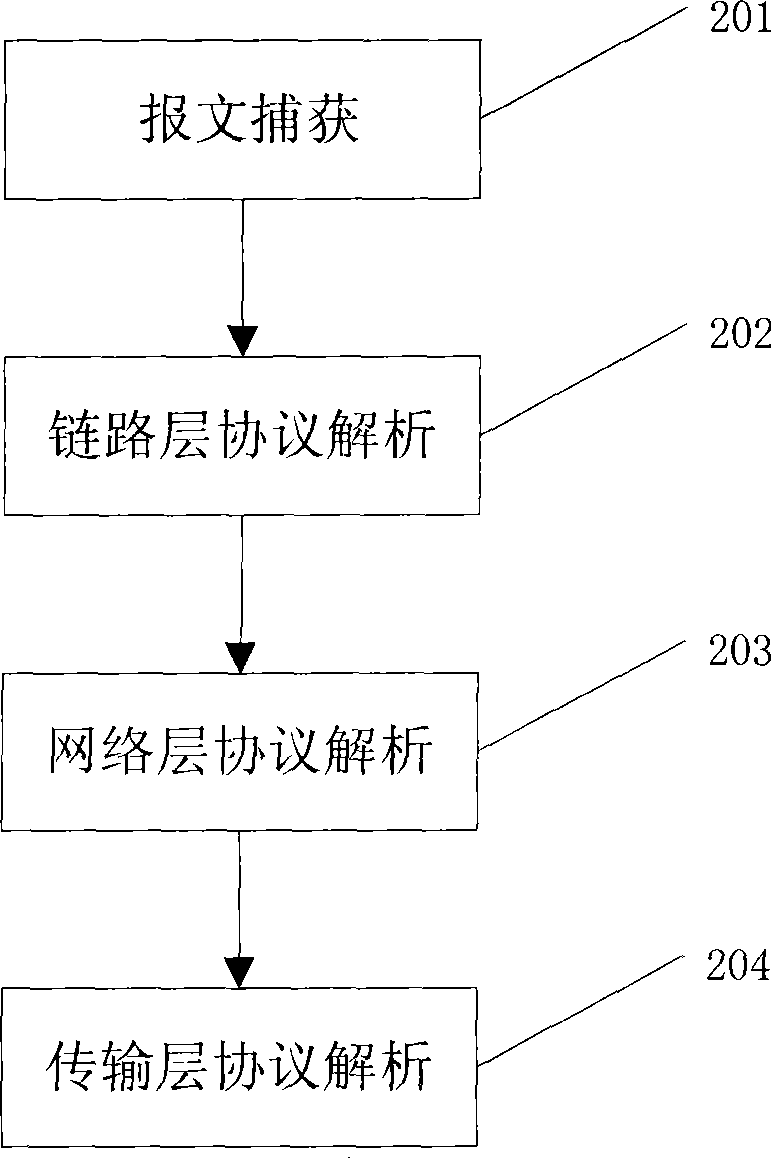
[0040] This embodiment is a preferred solution of the data collection step in the first embodiment. The sub-steps that described data acquisition step comprises, flow process is as figure 2 Shown:
[0041] Step 201: Capture raw data packets directly from the network card.
[0042] Step 202: Perform link layer protocol analysis to provide information for network layer protocol analysis;
[0043] Step 203: Analyze the network layer protocol, provide information for the transport layer protocol analysis, and extract the source IP address and destination IP address corresponding to the original data message.
[0044]Step 204: Analyzing the transport layer protocol, extracting the source and destination ports corresponding to the original data message, and analyzing all the information needed for the detection process.
Embodiment 3
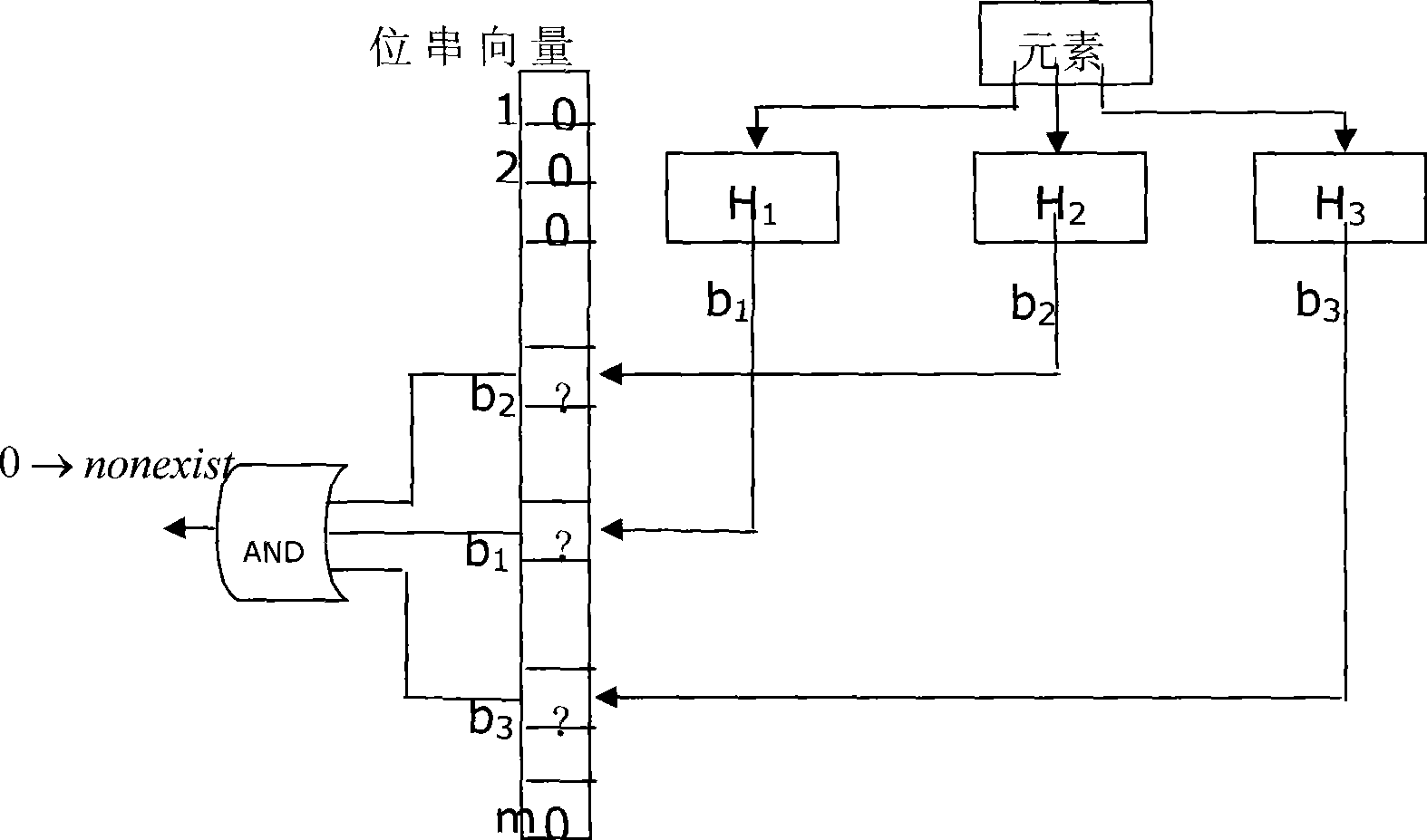
[0046] This embodiment is a preferred solution for the step of classifying and storing in Embodiment 1. The Bloom counting filter is used in the classified storage step of this embodiment, and the Bloom counting filter is a storage method with a data compression function, and stores elements in the form of a set. It maps an element (referred to as an IP address in the present invention) into a set through multiple hash functions to indicate whether the element is in the set; at the same time, it accumulates statistics on the number of collisions in a counting manner, That is, when the mapping value conflicts, the number of visits to the unit is represented by counting in the conflict unit. If the element can be restored, the frequency of occurrence of the element can be obtained, and corresponding to the IP address, the frequency of occurrence of the IP can be obtained.
[0047] In order to correctly restore the IP address, five hash functions are designed in this embodiment,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com