Identification authentication system and method through third-party
A technology for identity authentication and authentication information, applied in the field of identity authentication systems, can solve the problems of cumbersome, error-prone, low security, and achieve the effects of small workload, good security, and various implementation methods.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
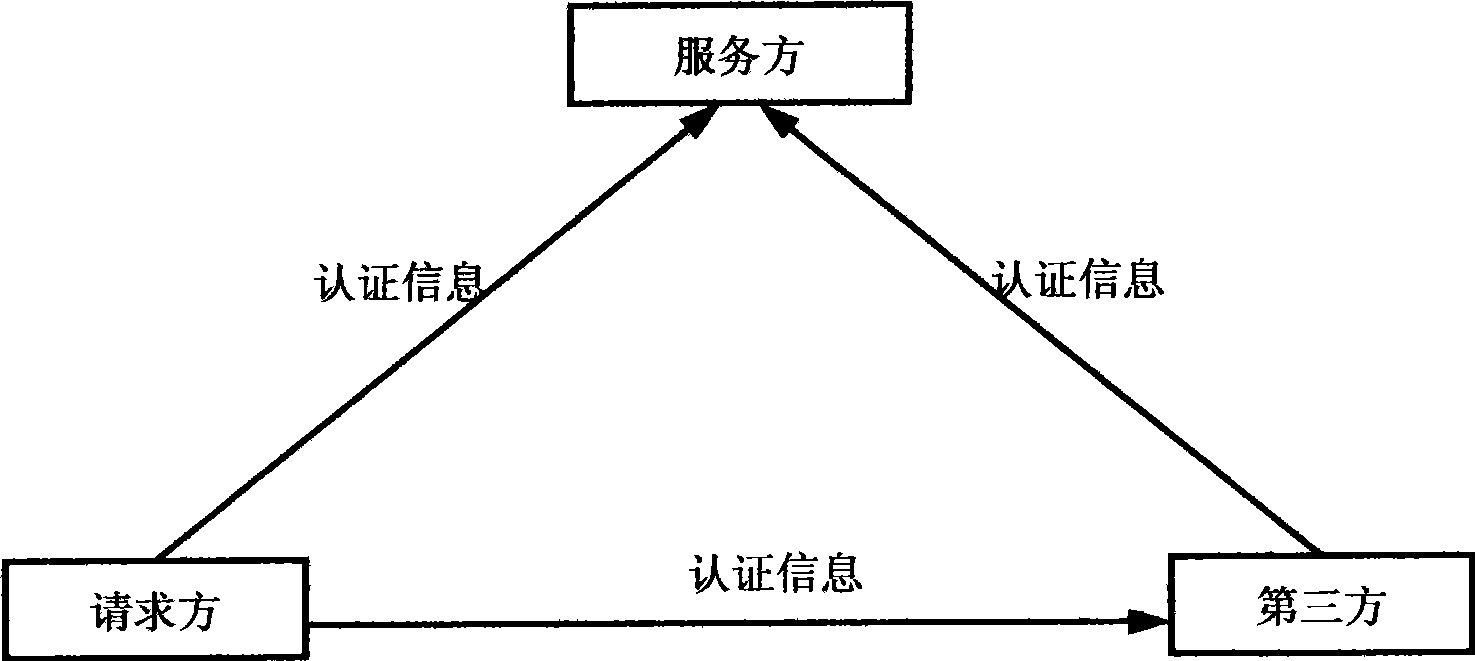
[0047] figure 1 It is the information transfer path diagram of Embodiment 1. For the network structure of this embodiment, please refer to Image 6 .
[0048] The closed transfer information in Embodiment 1 is the same authentication information and the start point and end point of the closed transfer are the same. In this embodiment, the requester is a user network terminal, the server is a network resource, the third party is an authentication service system that provides third-party identity authentication services on the Internet, and the authentication information is a random number.
[0049] Embodiment 1 comprises the following steps:
[0050] 1) The user network terminal passes the identity authentication of the authentication service system;
[0051] 2) The user network terminal requests a service from the network resource;
[0052] 3) The network resource generates a random number and a time stamp;
[0053] 4) The network resource sends the random number, the net...
Embodiment 2
[0067] figure 2 It is the information transmission path diagram of embodiment 2, the network structure of this embodiment please refer to Image 6 .
[0068] The closed transfer information in Embodiment 2 is the same authentication information and the start point and end point of the closed transfer are different. In this embodiment, the requester is a user network terminal, the server is a network resource, the third party is an authentication service system that provides third-party identity authentication services on the Internet, and the authentication information is a random sequence.
[0069] Embodiment 2 comprises the following steps:
[0070] 1) The user network terminal passes the identity authentication of the authentication service system;
[0071] 2) The user network terminal generates a random sequence;
[0072] 3) The user network terminal sends the user name and random sequence to the network resource and requests authentication, and at the same time, the ...
Embodiment 3
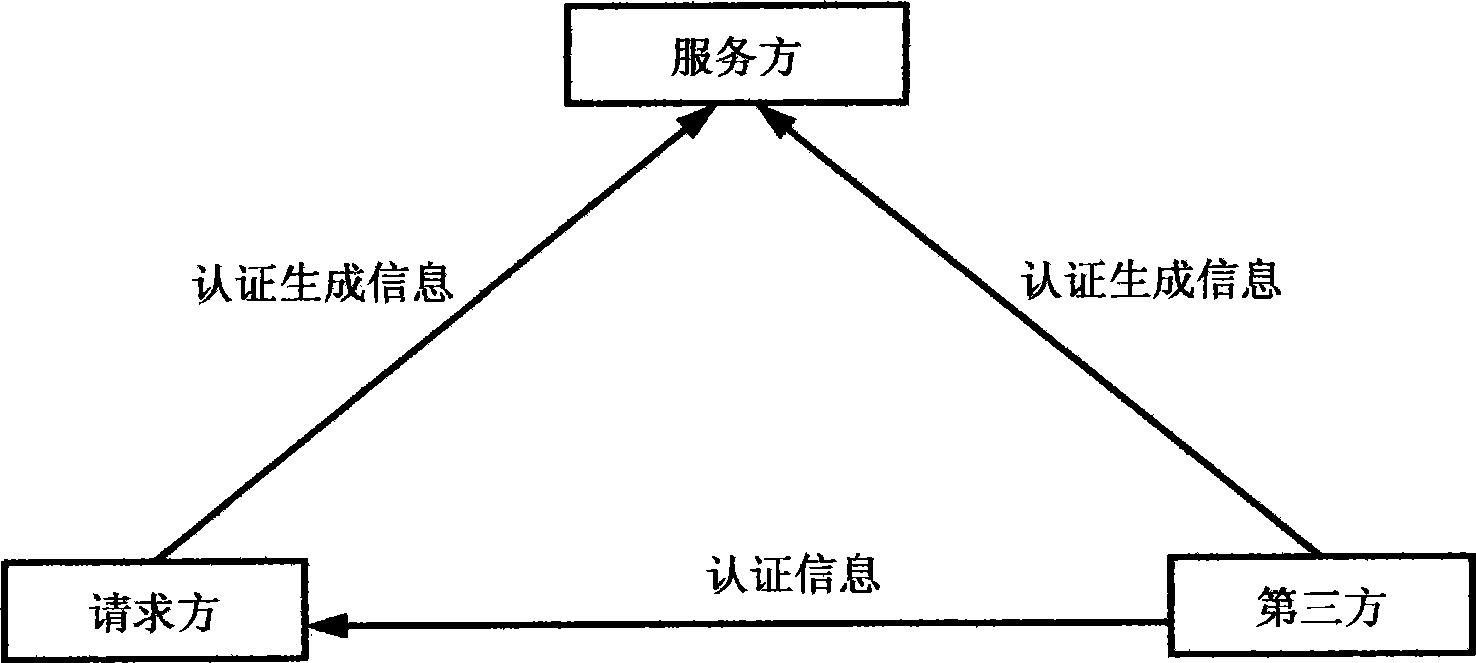
[0084] image 3 It is the information transmission path diagram of embodiment 3, the network structure of this embodiment please refer to Image 6 .
[0085] In Embodiment 3, the closed transfer information includes authentication generation information generated based on the authentication information, and the start point and end point of the closed transfer are different. In this embodiment, the requester is a user network terminal, the server is a network resource, the third party is an authentication service system that provides third-party identity authentication services on the Internet, and the authentication information is a random sequence, or a mathematical algorithm, or an algorithm Parameters, the user network terminal generates the information that needs to be sent by its own side in the closed transmission according to the authentication information and the information agreed with the authentication service system.
[0086] Embodiment 3 comprises the following ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com