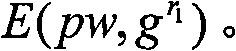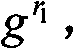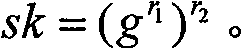Customer authentication method, system, server and customer node
A user authentication and user node technology, applied in the field of network information security, can solve problems such as complex design and increased maintenance costs, and achieve the effects of enhanced security, easy maintenance, and two-way authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0054] An embodiment of the present invention provides a user authentication method, the method comprising:
[0055] The server receives the identity information submitted by the user, generates a user password, and sends registration information including the user password and valid period to the user; the user generates login information parameters, and sends login information to the server; Click Generate User Session Key Parameters, and send the user session key parameters to the user; the user generates the user session key according to the received user session key parameters; the server and the user authenticate according to the session keys generated respectively.
[0056] Wherein, the algebraic curve may be an elliptic curve, a hyperelliptic curve or a conic curve. As shown in Figure 1, in the embodiment of the present invention, the user U is used as the user who accesses the resources, the server S is used as the trusted server providing resources, and the algebraic...
Embodiment 2
[0081] As shown in Figure 2, the embodiment of the present invention provides a method for the user to change the login password after mutual authentication has been passed between the user and the server. The specific steps of the method are as follows:
[0082] Step 201: The user U sends the identity ID, the old password pw and the valid period i to the server S through the secure channel established after mutual authentication with the server S;
[0083] Step 202: After the server receives the ID, the old password pw and the validity period i, check the equation pw=[h(K||ID||i)] k Whether it is established, if it is established, then the server S selects a new valid period i' and pw'=[h(K||ID||i')] k , and send (pw', i') to user U through a secure channel, so that the user gets new passwords pw' and i'.
[0084] In the method for a user to change a login password provided by the embodiment of the present invention, the server generates a new valid period and a new password...
Embodiment 3
[0086] As shown in Figure 3, an embodiment of the present invention provides a system for user authentication, including:
[0087] The server is used to receive the identity information submitted by the user node, select a valid period, generate a user password according to the identity information and the valid period, and send registration information including the user password and the valid period to the user node; and after receiving the login information of the user node, Generate server session key according to identity information, login information parameters and valid period, generate user session key parameter according to generation point of algebraic curve, send user session key parameter to user node; authenticate according to server session key and user node , after the authentication is passed, the user is authorized to access the resource.
[0088] The user node is used to submit identity information to the server. After receiving the registration information,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com