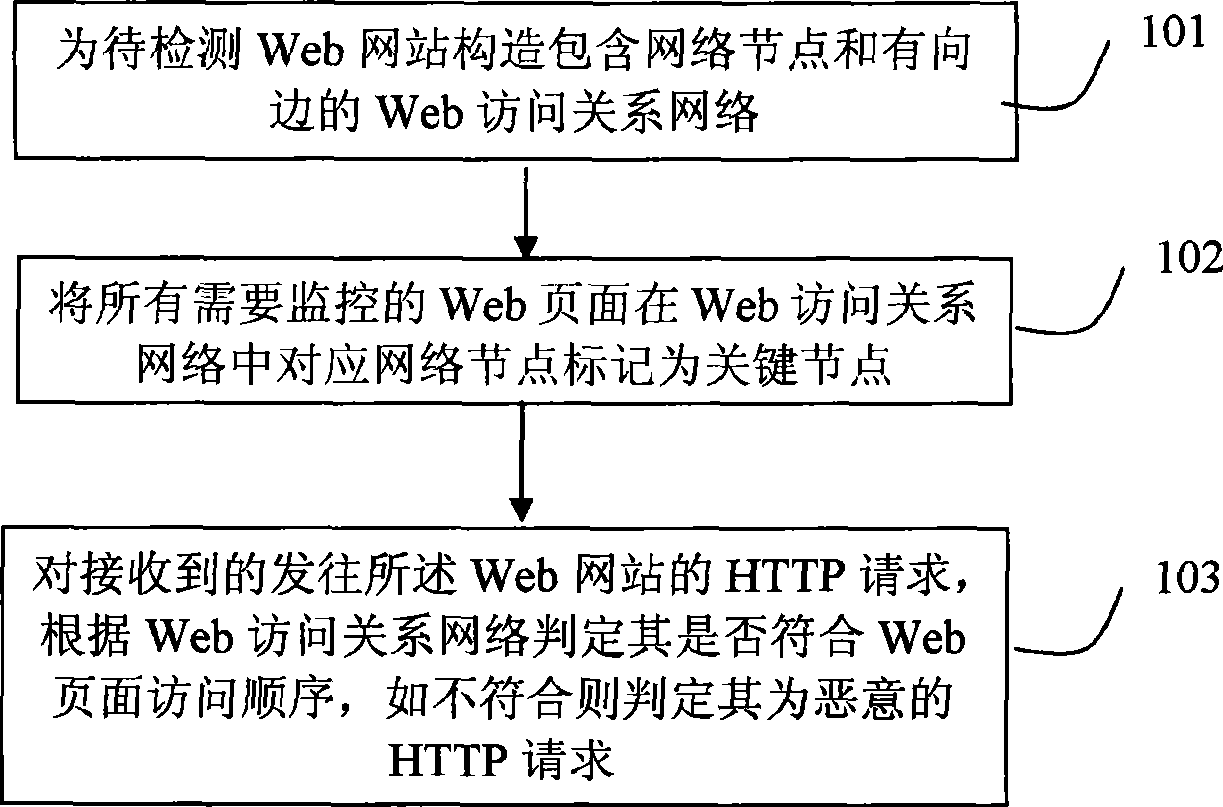
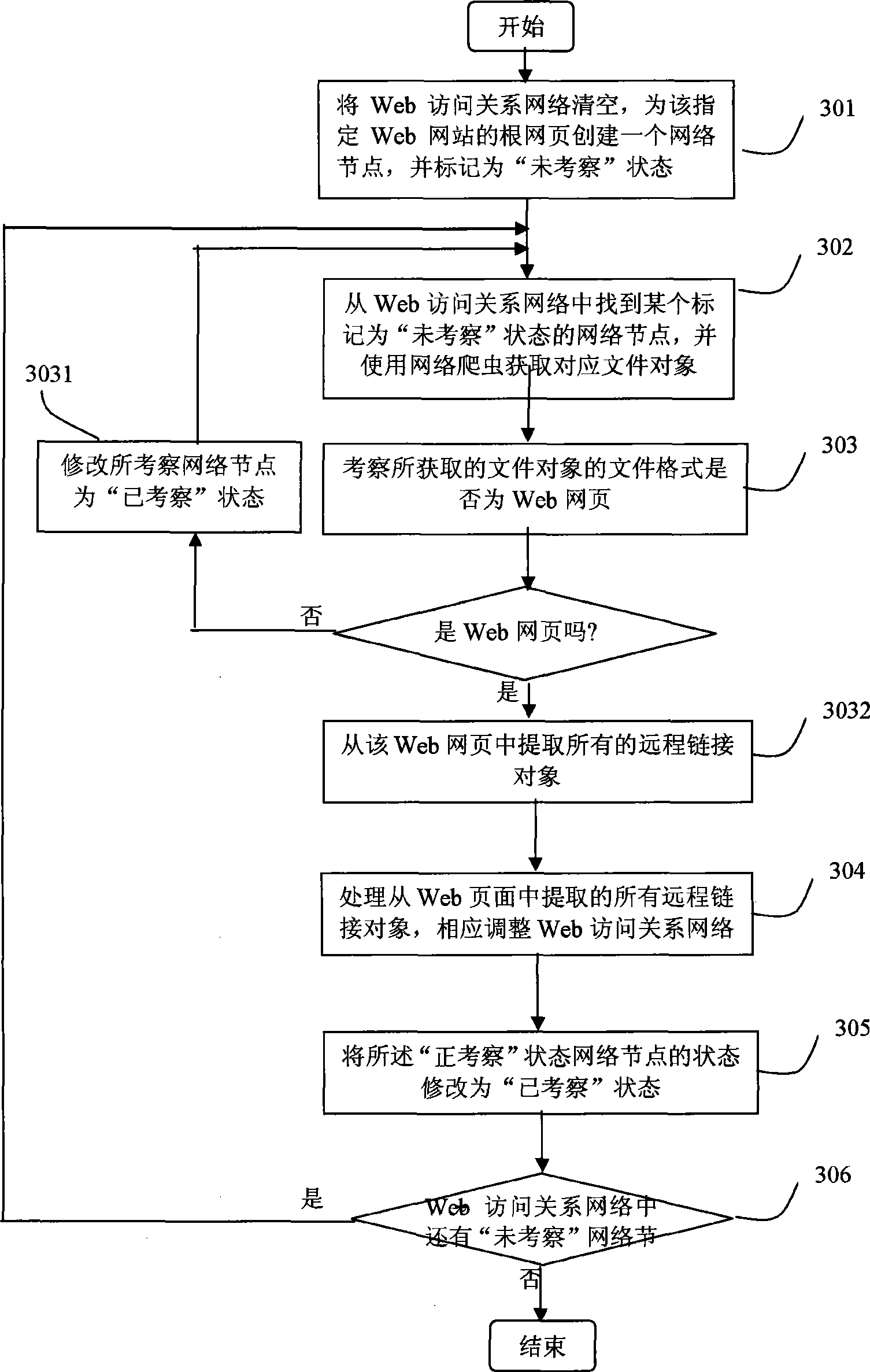
Method and device for detecting malicious HTTP request
A malicious, yet-to-be-detected technology, used in security communication devices, digital transmission systems, electrical components, etc., to solve problems such as intrusion detection algorithms being difficult to detect.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0087] Assume that the malicious HTTP request detection unit receives the following http request:
[0088] GET / login.asp HTTP / 1.1\r\n
[0089] Host:www.test.com\r\n
[0090] ser-Agent: Mozilla / 5.0(xxxx)\r\n
[0091] Accept: text / html; image / jpg, * / *\r\n
[0092] Accept-Language: zh-cn, zh\r\n
[0093] Accept-Charset: gb2312, utf-8\r\n
[0094] Referer: http: / / www.test.com∧r\n
[0095] The URI value of the HTTP request is " / login.asp", and the Referer value is "http: / / www.test.com / ". First, search based on the URI value Figure 7 It is found that the network node corresponding to / login.asp exists, but it is not a key node. Therefore, it is directly judged as "no abnormal HTTP request".
example 2
[0097] Assuming that the hacker wants to attack the web application system whose website is www.test.com, he sets up a website by himself, the website is www.abc.com, and the root web page of the website contains the following line of HTML code: "".
[0098] If a web user (victim) of www.test.com has successfully completed user authentication through the login web page login.asp on the web application system, but it does not want to execute the function corresponding to the hyperlink / actionl.asp. But unfortunately, he opened the hacker website www.abc.com without logging out from the www.test.com web application system. At this time, its web client will interpret and execute the above HTML maliciously inserted by the hacker code, the result is that the victim’s web client will send an HTTP request as shown in Table 2 to the web application system www.test.com, and the Cookies field of the HTTP request automatically carries the victim’s login www.test. com Web application syst...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com