A motion bit code and its use method
A technology of moving bit code and bit code, which is applied in the field of moving bit code and its application, can solve the problems of needing hardware, password exposure, lack of security, etc., and achieve the effect of no hardware cost, high security, and easy promotion
Inactive Publication Date: 2008-09-17
刘建生
View PDF0 Cites 2 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
[0003] 1. It is easy to promote but lacks security, mainly in the way of static password plus additional code, relying on anti-virus software protection, because the hacker program is generated first, and the anti-virus software is upgraded later, there is a time difference;
[0004] 2. There are security but lack of easy promotion, such as password table card, using mobile phone to transmit one-time password, password generator and other solutions that require accessories. Such solutions are either troublesome to use, or require hardware, and are costly. What's more troublesome is that these attachments will be lost and the password will be exposed
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
specific Embodiment approach
[0022] Service-Terminal:
[0023]
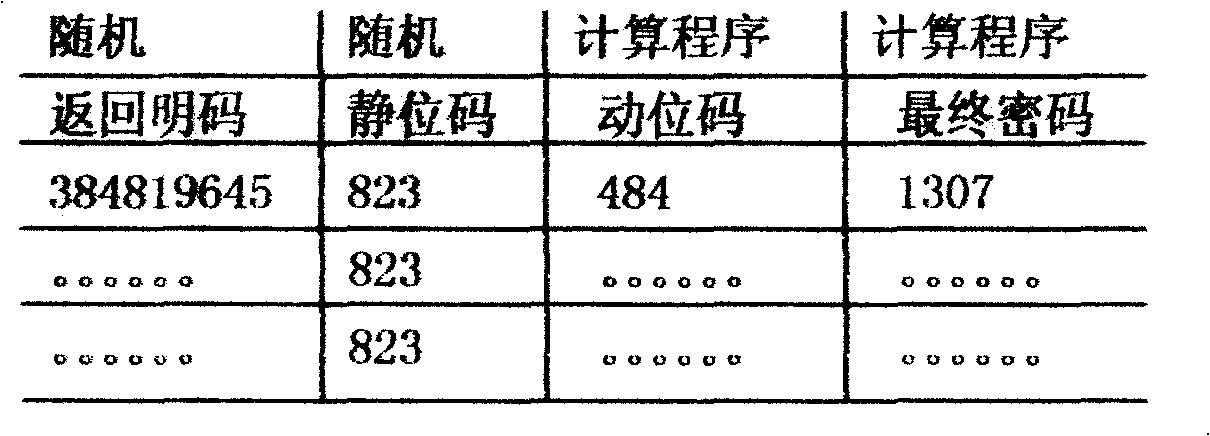
[0024] The above is to calculate the static bit code as a static calculation code, bind the static bit code with the returned plain code, and bind the final password with the user account to realize the authentication of the account number and the final password submitted by the user. .
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
The present invention relates to a static calculating code, a returning plain code, a static bit code, a dynamic bit code, a final key, a website server and a terminal device. The invention provides a dynamic bit code and a using method. The user terminal uses the static bit code and compares the effective code in the returning plain code for rearrangement to obtain a novel dynamic bit code. The dynamic bit code and the static calculating code are executed with calculation with same regulation to the server terminal. The calculated result is taken as the final code and is transmitted to the server terminal to check for checking the identity of the user terminal. The server terminal is established with an identification system which comprises a static calculating code, a return plain code, a static bit code, a dynamic bit code and a final key. The invention prevents that the illegal user steals the key. The invention is suitable for all ciphering product, logging-on system, wireless network checking system, bond system and other systems.
Description
technical field [0001] Static calculation codes, return plain codes, static codes, dynamic codes, final passwords, website servers, and terminal devices in the field of encryption and decryption. Background technique [0002] Due to the existence of hackers, a variety of technical solutions for protecting login website passwords have emerged, and these solutions are divided into two categories: [0003] 1. It is easy to promote but lacks security, mainly in the way of static password plus additional code, relying on anti-virus software protection, because the hacker program is generated first, and the anti-virus software is upgraded later, there is a time difference; [0004] 2. There are security but lack of easy-to-promote categories, such as password table cards, using mobile phones to transmit one-time passwords, password generators and other solutions that require accessories. Such solutions are either troublesome to use, or require hardware, and are costly. What's mor...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Applications(China)
IPC IPC(8): H04L9/32H04L9/08
Inventor 刘建生
Owner 刘建生
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com