Method for obtaining length variable interactivity identifying code based on Ajax
A verification code and verification code picture technology, which is applied in the field of network security protection using verification codes, can solve problems such as unsatisfactory security, achieve the effects of increasing anti-cracking capabilities, ensuring security, and solving user information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
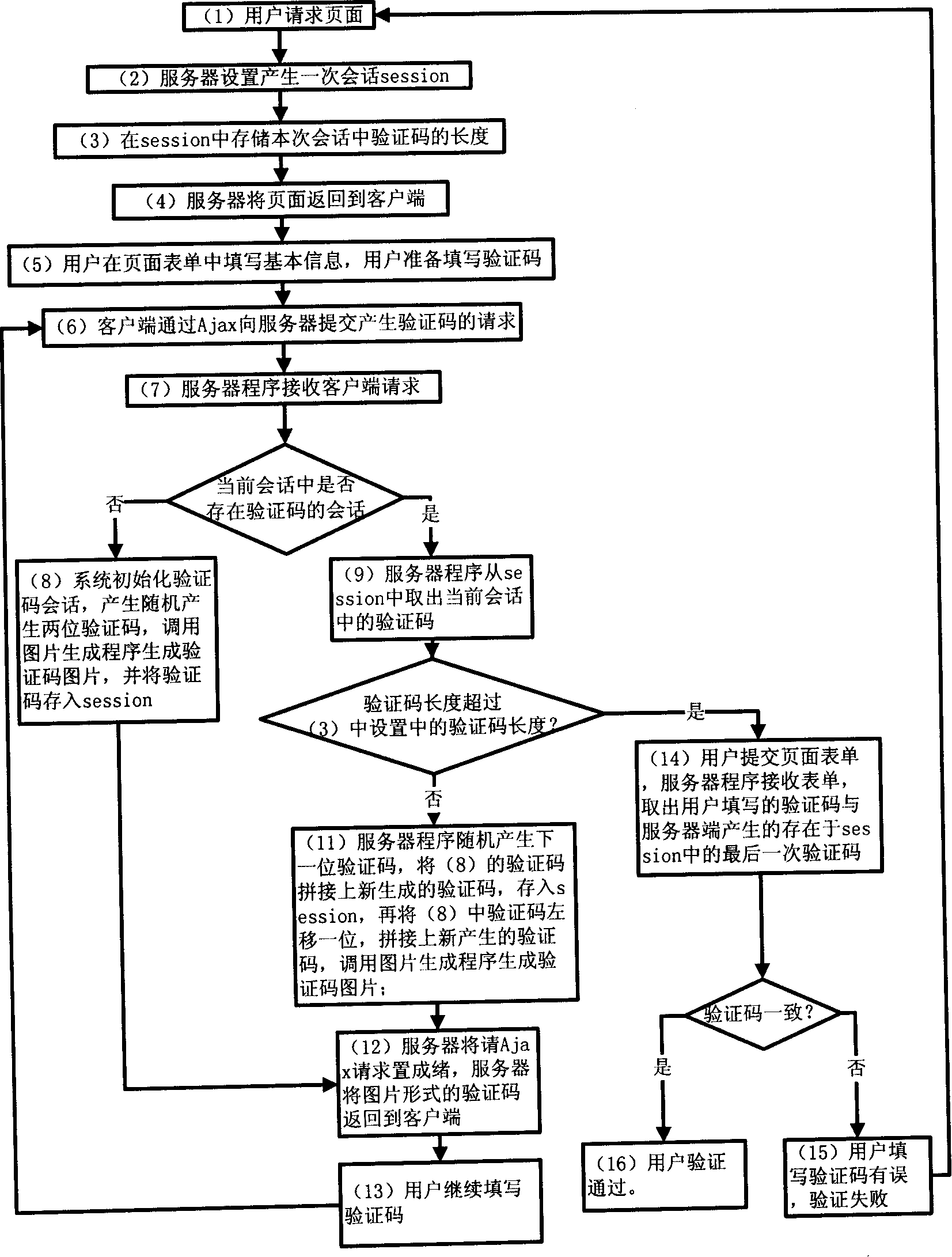
[0021] The present invention is described in more detail below in conjunction with accompanying drawing example:
[0022] In conjunction with accompanying drawing, concrete implementation steps of the present invention are:
[0023] (1) The user requests a page that needs to fill in the verification code;
[0024] (2) Server settings generate a session session;
[0025] (3) Store the length of the verification code in this session in the session, generally 4 to 6 digits;
[0026] (4) The server returns the page to the client;
[0027] (5) The user fills in the basic information in the page form, and the user prepares to fill in the verification code;
[0028] (6) The client submits a request to generate a verification code to the server through Ajax;
[0029] (7) The server program receives the client request, and judges whether there is a session of the verification code in the current session, if there is no session, turn to (8), otherwise turn to (9);
[0030] (8) The ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com