File access control method
A technology of file access and control methods, which is applied in the directions of instruments, digital data authentication, electronic digital data processing, etc., to achieve the effect of reducing the attack range, improving security, and protecting security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] A specific implementation of the present invention on the Micorosoft Windows XP operating system is described below.
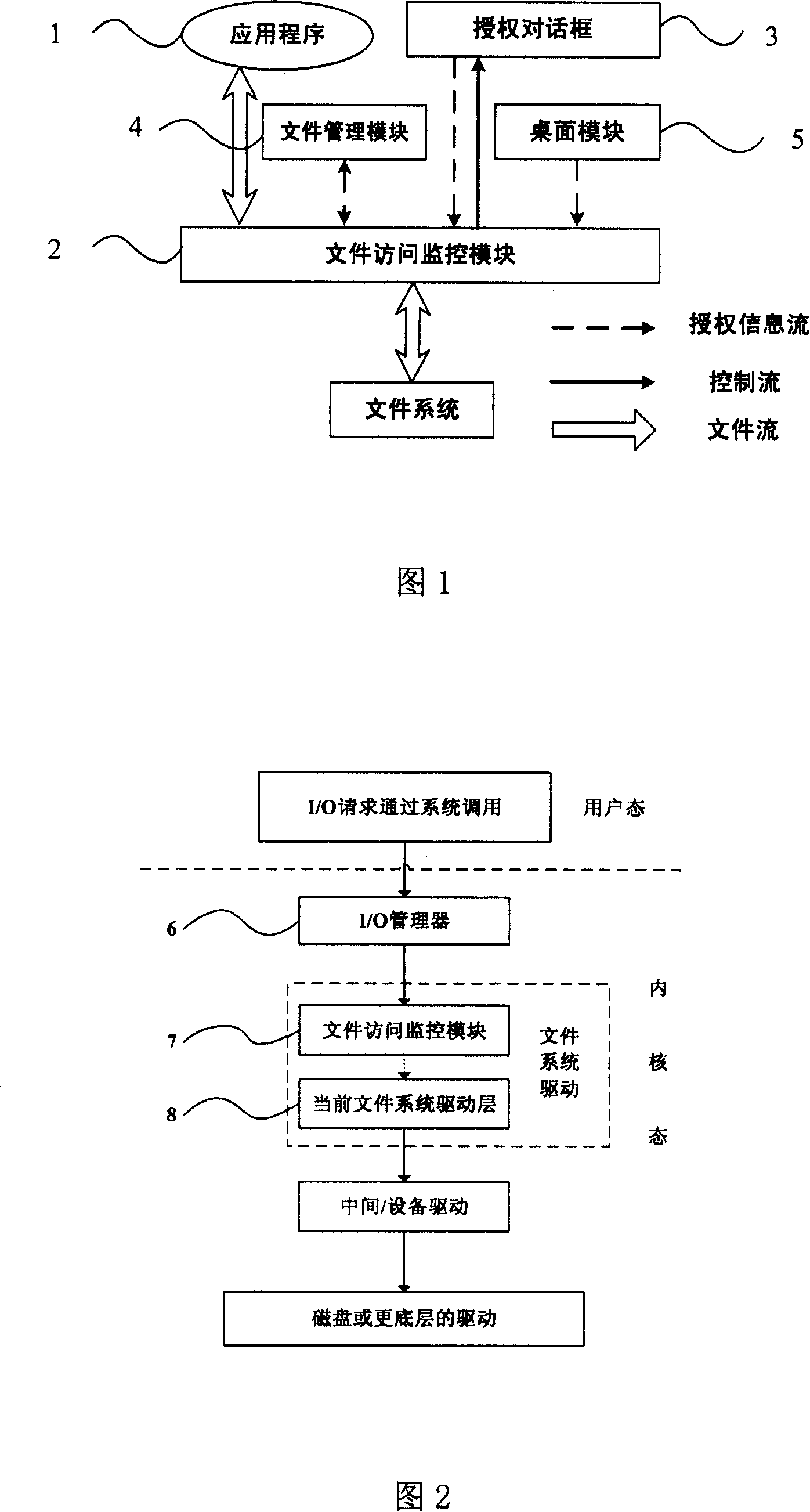
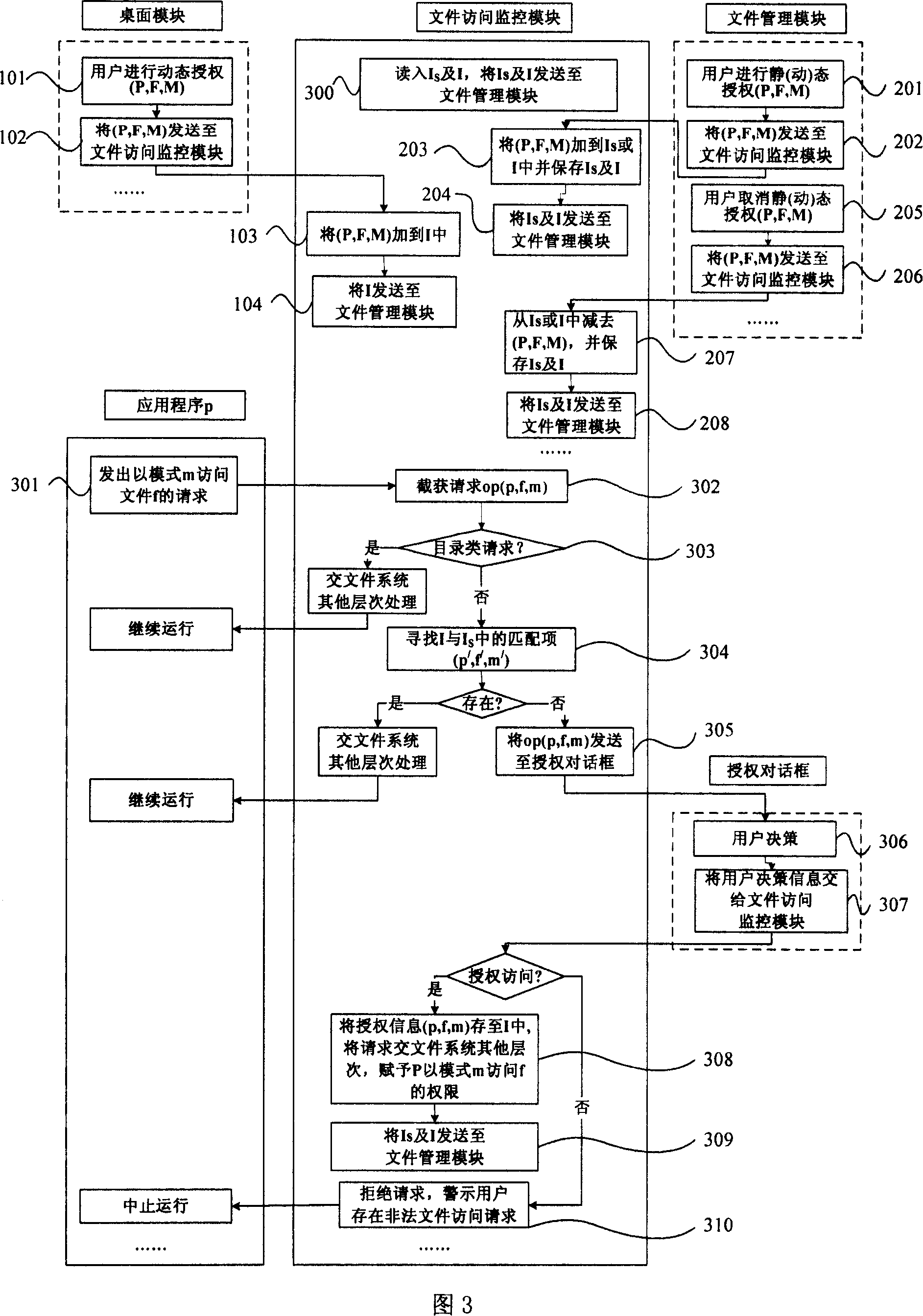
[0020] Fig. 1 is the overall structural diagram of the implementation method of the present invention, comprises 4 main modules, has provided the relation between them in the figure. The file access monitoring module is the core of implementing file access control. The desktop module, file management module, and authorization dialog box are all trusted window programs, that is, the actions of user input devices such as mouse, keyboard, and stylus that they process must be generated by the user, and their communication with the file access monitoring module is safe and reliable. of. Unless otherwise specified, directories are treated as files.
[0021] Use (p, f, m) to indicate that the user authorizes the program p to access the file f in mode m, I indicates the dynamic authorization set, and I s Represents a static authorization collection. Dynamic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com