Dynamic accesses control method based on trust model
A dynamic access control and trust model technology, applied to electrical components, user identity/authority verification, transmission systems, etc., can solve the problem of difficulty in centrally maintaining certificate revocation lists, difficulty in applying to large-scale user groups, and weakening of individual self-trust, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
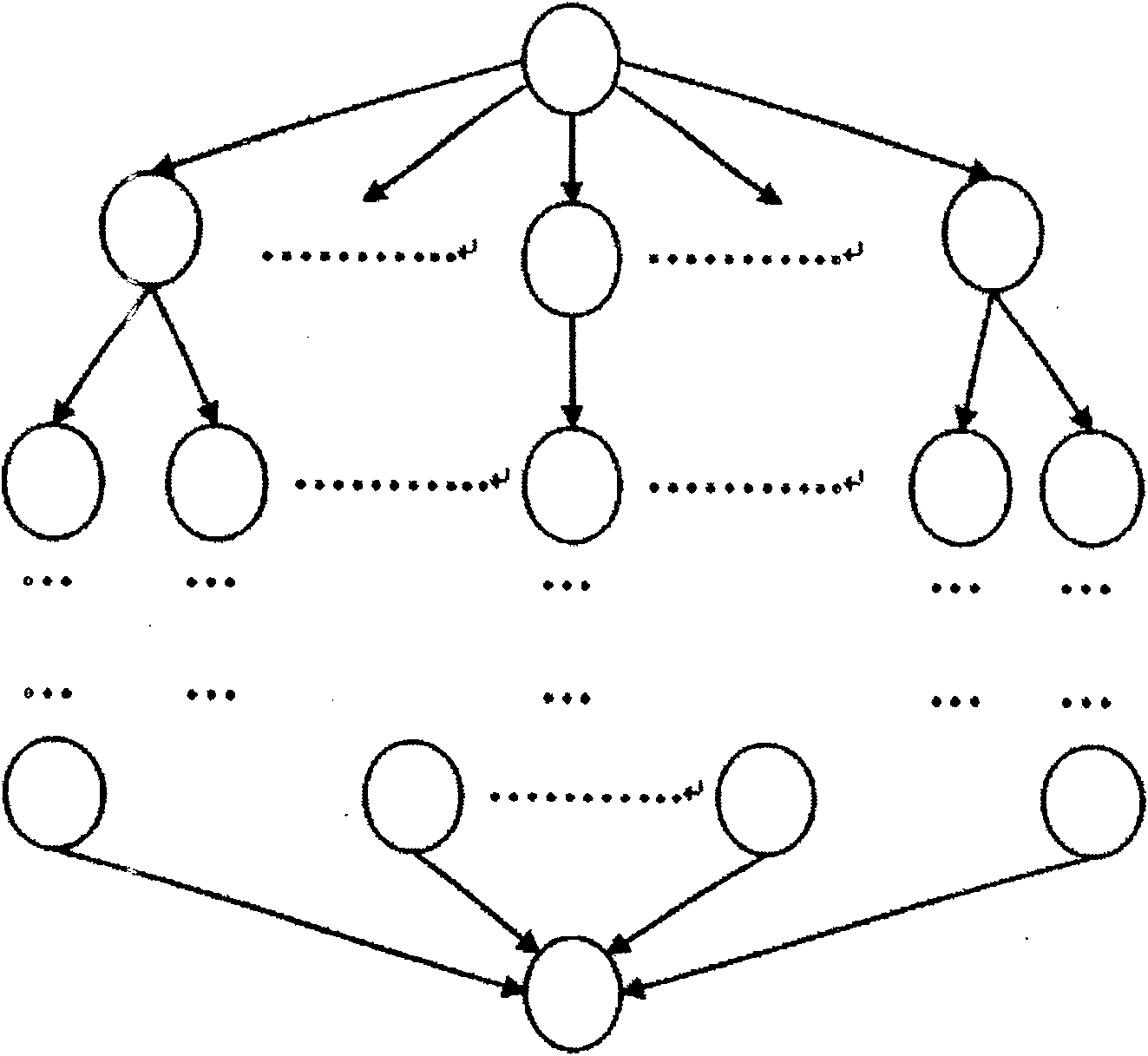
[0077] 1. Grid users request access to resources
[0078] If the customer is not registered, he should first generate a local certificate to be issued locally, and then submit the certificate to the certification authority CA (Certification authority) to request authorization. The certification center judges whether the customer has permission to access grid resources. Use its private key to sign the local certificate sent from the client and return it to the user. After receiving the issued certificate, the client registers with the autonomous domain server and sends its own digital certificate. The autonomous domain server verifies the digital certificate , after passing, the customer ID and password will be saved in the autonomous domain service database, and the customer will become a grid user;
[0079] When a grid user submits a task, he first logs in to the autonomous domain server, and then single-signs on. The purpose is to prevent the user from logging in to other au...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com