Access control method and device for terminal equipment
A terminal equipment and access control technology, applied in the network field, can solve the problems of difficult detection of terminal equipment with malicious connection requests, lack of access control methods, access control, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
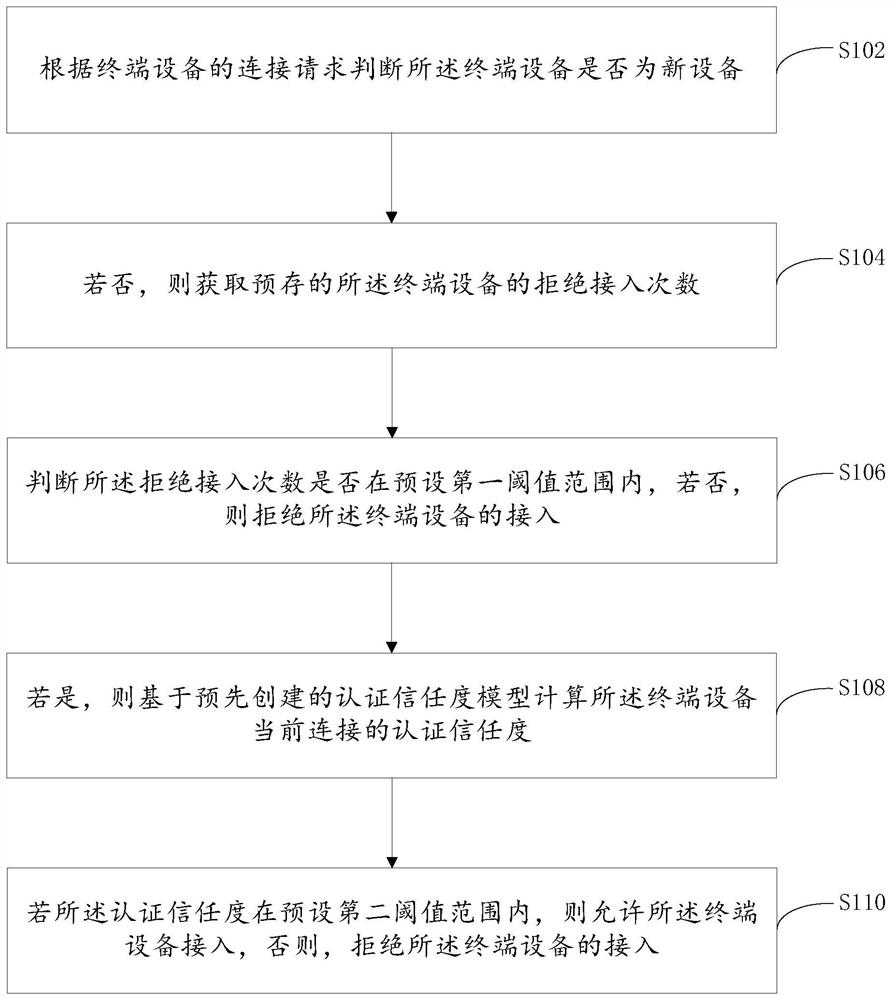
[0056] This embodiment provides an access control method for terminal equipment, which is applied to nodes in a blockchain network, such as figure 1 As shown, the method includes:
[0057] Step S102: Determine whether the terminal device is a new device according to the connection request of the terminal device.
[0058] It should be noted that the terminal device access control method provided in this embodiment is applied to a node in the blockchain network. The node can be a fog computing node, a cloud node, or an edge computing node, etc., preferably a fog computing node. Computing nodes. This embodiment takes fog computing nodes as an example. Each fog computing node is connected through a blockchain network to form a fog computing network. Any node in the fog computing network can receive a connection request from a terminal device, and the terminal device also Can pass WiFi (Wireless-Fidelity, wireless connection), ZigBee (also known as Zigbee, is a wireless network pr...
Embodiment 2
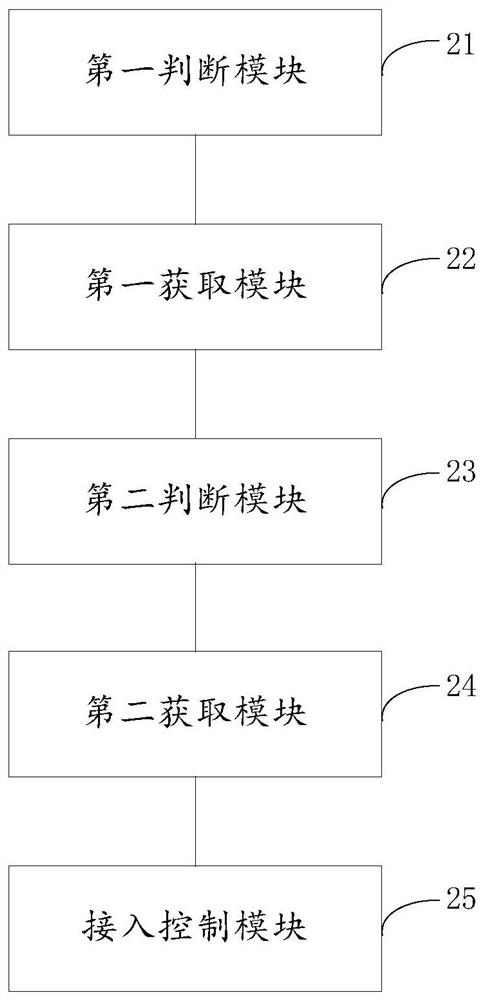
[0111] Such as figure 2 As shown, this embodiment provides an access control device for terminal equipment, which is set on a node in a blockchain network, and the device includes:
[0112] The first judging module 21 is used to judge whether the terminal device is a new device according to the connection request of the terminal device;
[0113] The first acquiring module 22 is connected with the first judging module 21, and is used to acquire the prestored access denial times of the terminal equipment when the judging result of the first judging module 21 is no;
[0114] The second judging module 23 is connected with the first acquiring module 22, and is used to judge whether the number of rejected access times is within the preset first threshold range, and if not, reject the access of the terminal device;
[0115] The second acquisition module 24 is connected to the second judgment module 23, and is used to calculate the authentication trust degree of the current connecti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com