Method for detecting network game cheat
An online game and game technology, applied in indoor games, video games, data exchange networks, etc., can solve the problem that plug-ins cannot be avoided, and achieve the effect of preventing cheating and reducing income loss.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0047] The specific implementation method of the present invention will be described below by taking a typical client / server online game as an example.
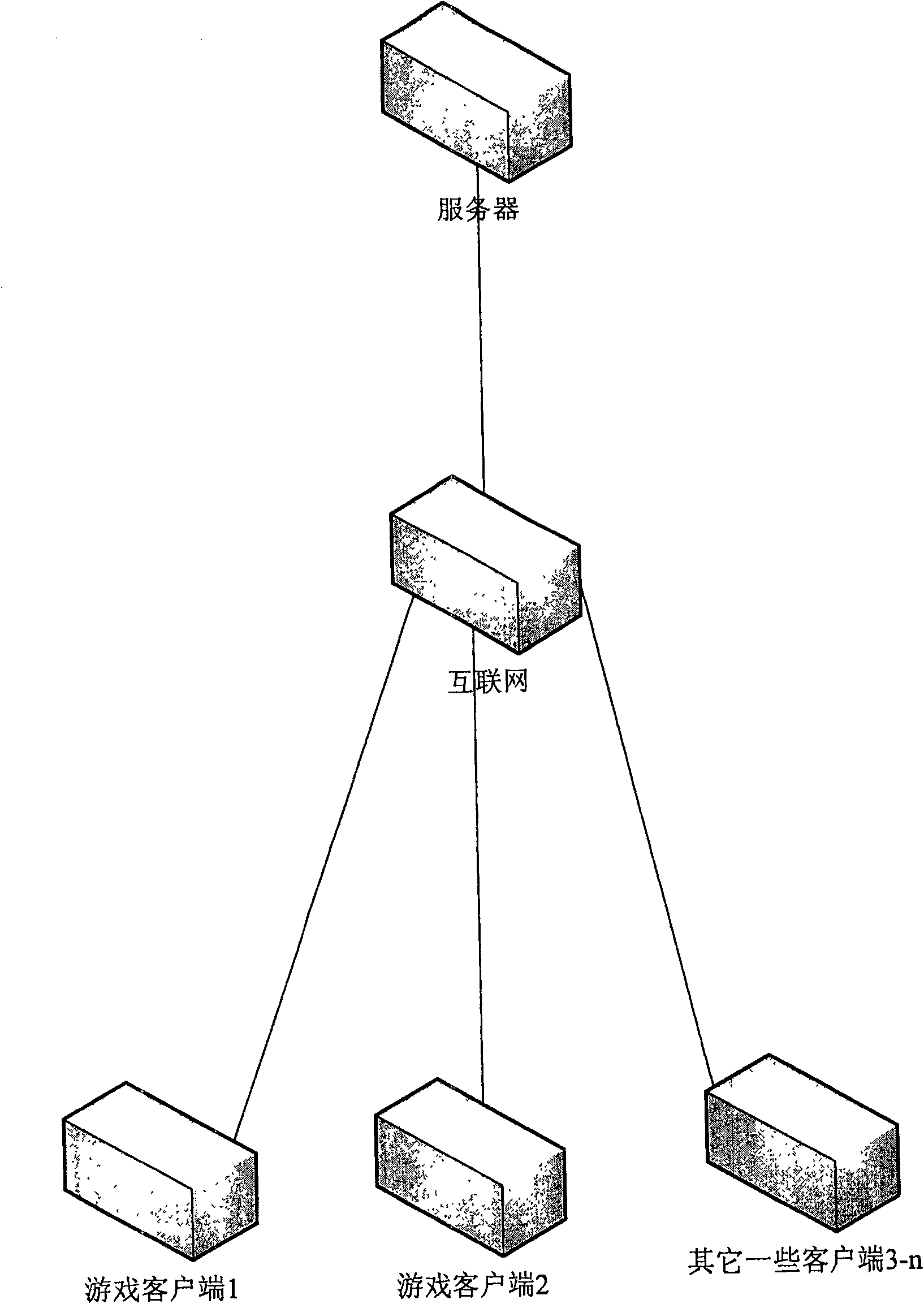
[0048] The computer in the game is composed of server, game client 1, client 2 and some other clients 3-n, such as figure 1 shown.
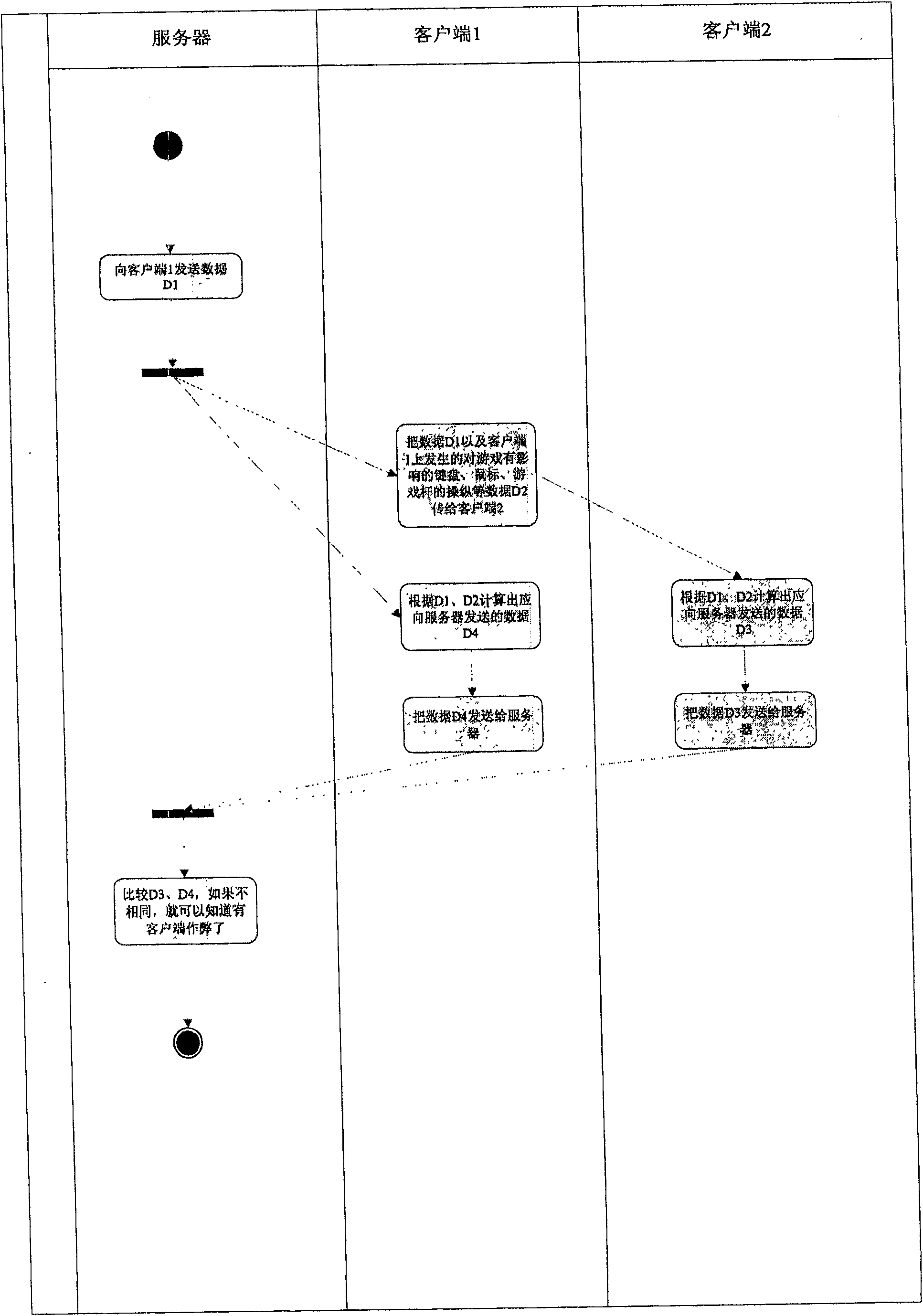
[0049] like figure 2As shown, after client 1 connects to the server, it transmits the data D1 it receives from the server together with the data D2 on client 1 that affects the game such as keyboard, mouse, and joystick operations to client 2. Carry time information in data D1 and D2, for example, D1 contains the time when the server sends D1, and the time when the authenticated client processes D1, D2 contains the time when the authenticated client processes D2, and the authenticated client The time when the client sends data to the server. Therefore, the client 2 can calculate the data D3 that the client 1 should send to the server according to D1 and D2. Since D3 and the data D4 received...
Embodiment 2
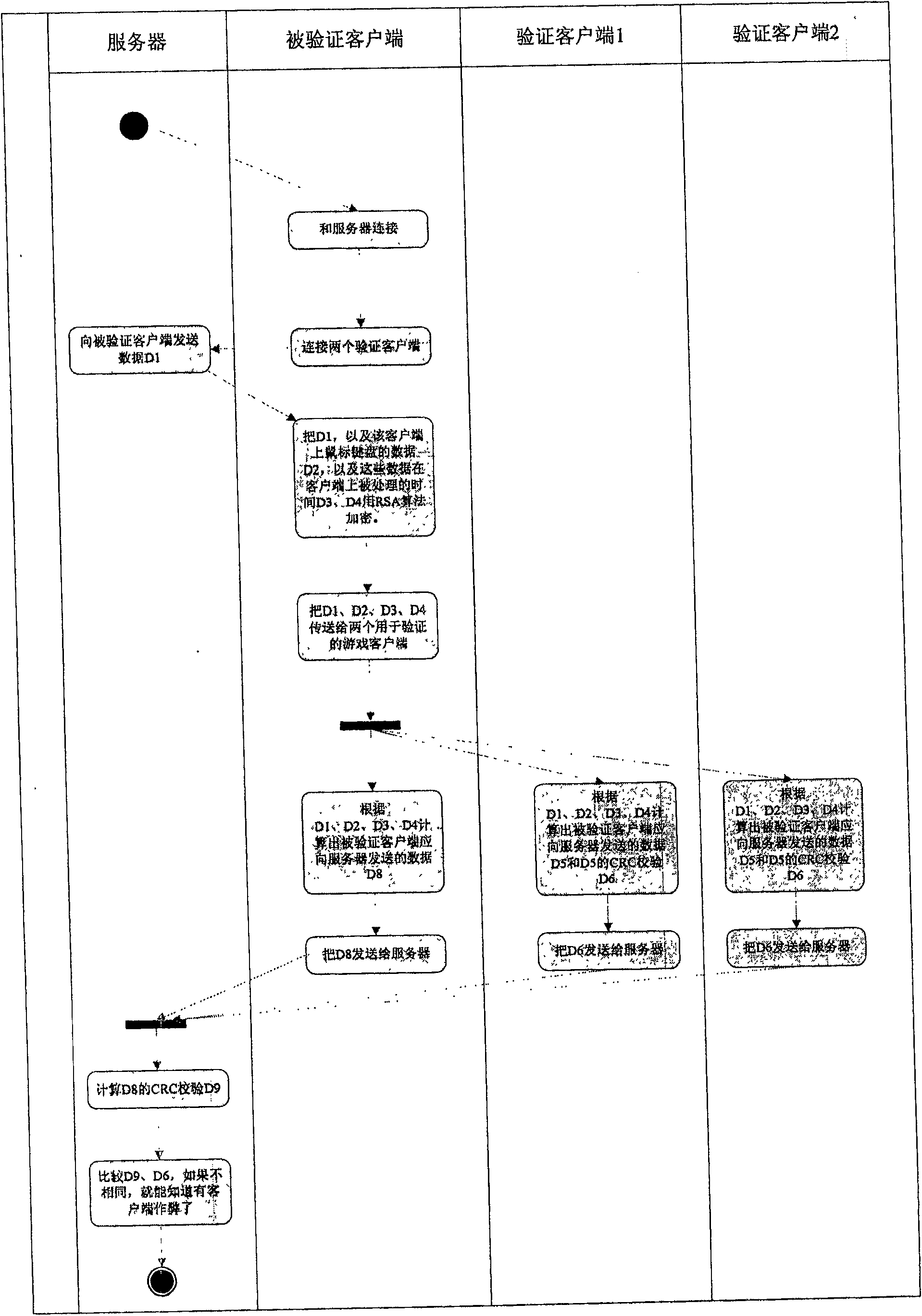
[0055] In this embodiment, in order to prevent the verification client from modifying the data passed to it by the verified client, and then falsely report that the verified client is cheating, the data such as D1 and D2 can be sent to the verified client before the verified client sends the data to the verified client. Use data with RSA (RSA is an asymmetric encryption algorithm. It is widely used in public key encryption standards and electronic commerce. RSA was proposed by Ron Rivest, Adi Shamir and LenAdleman. RSA uses the initial letters of their three names. composed together.) Algorithm encryption. The server sends the decrypted public key to the authentication client. If the verification client reports to the server that the verified client is cheating, the server will require the verification client to transmit the data D1 and D2 sent by the verified client to the verification client to the server. The server calculates the data D3' that the authenticated client sho...
Embodiment 3
[0058] In addition, the present invention allows an authenticated client to connect to two or more authenticated clients at the same time. If the connection between the authenticated client and one or more authentication clients is interrupted, as long as the authenticated client is still connected to at least one authentication client normally, the authentication can continue. If the authenticated client interrupts all connections with the authenticated client for reasons such as evasion of authentication or network failure, the server needs to terminate the authenticated client because there will be no authenticated client to authenticate the authenticated client end connection. If the authenticating client never reports cheating by the authenticated client, it doesn't matter as long as the other authenticating client works fine. In addition, some clients can deliberately transmit wrong data to the verification client. If it does not report cheating, it can be judged that t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com