Method and apparatus for authentication of client server communication
a client server and authentication technology, applied in the field of network communication, can solve the problems of insufficient to enable an intruder to forge a message, restricted financial data, and other users not being permitted to access that data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
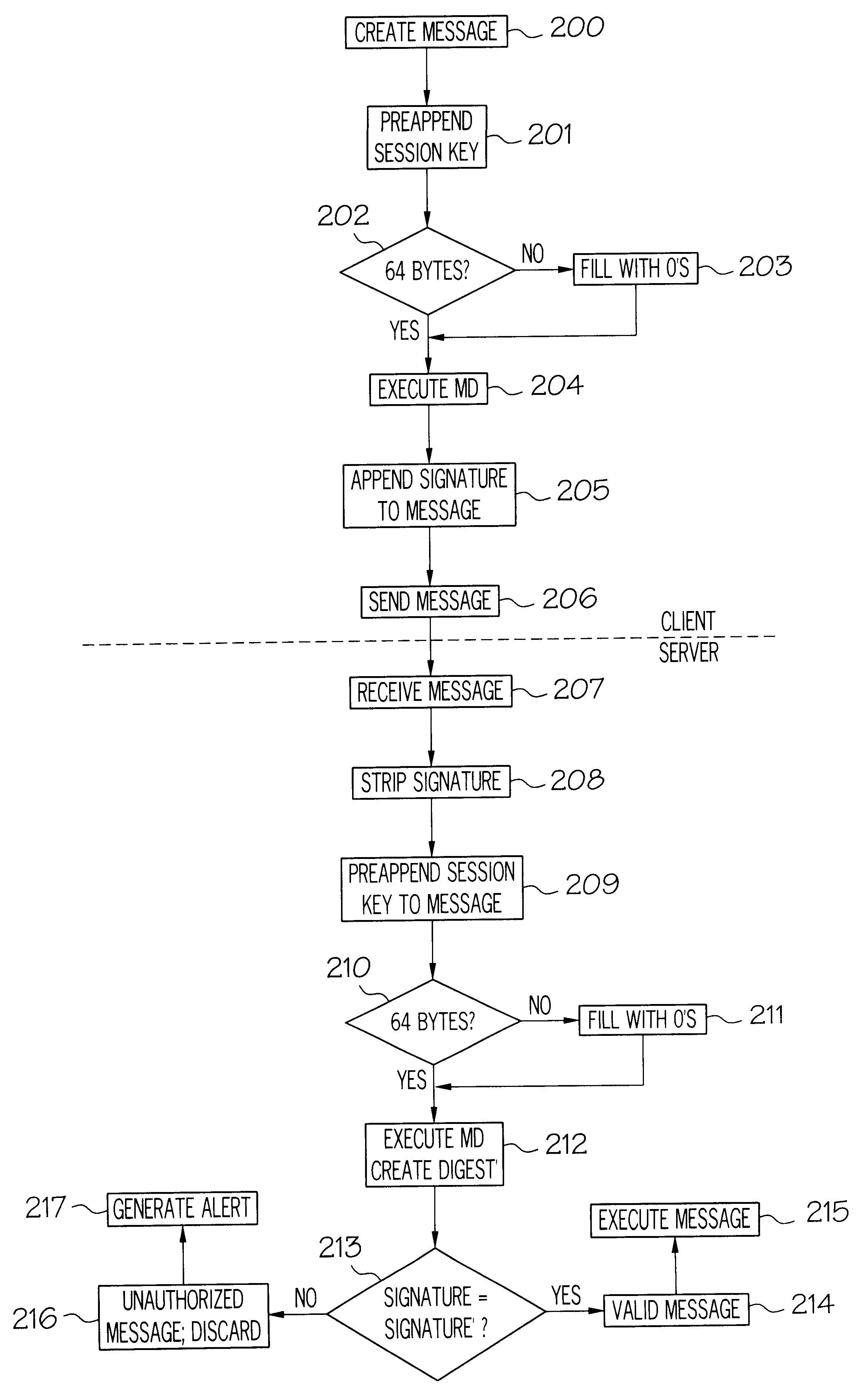
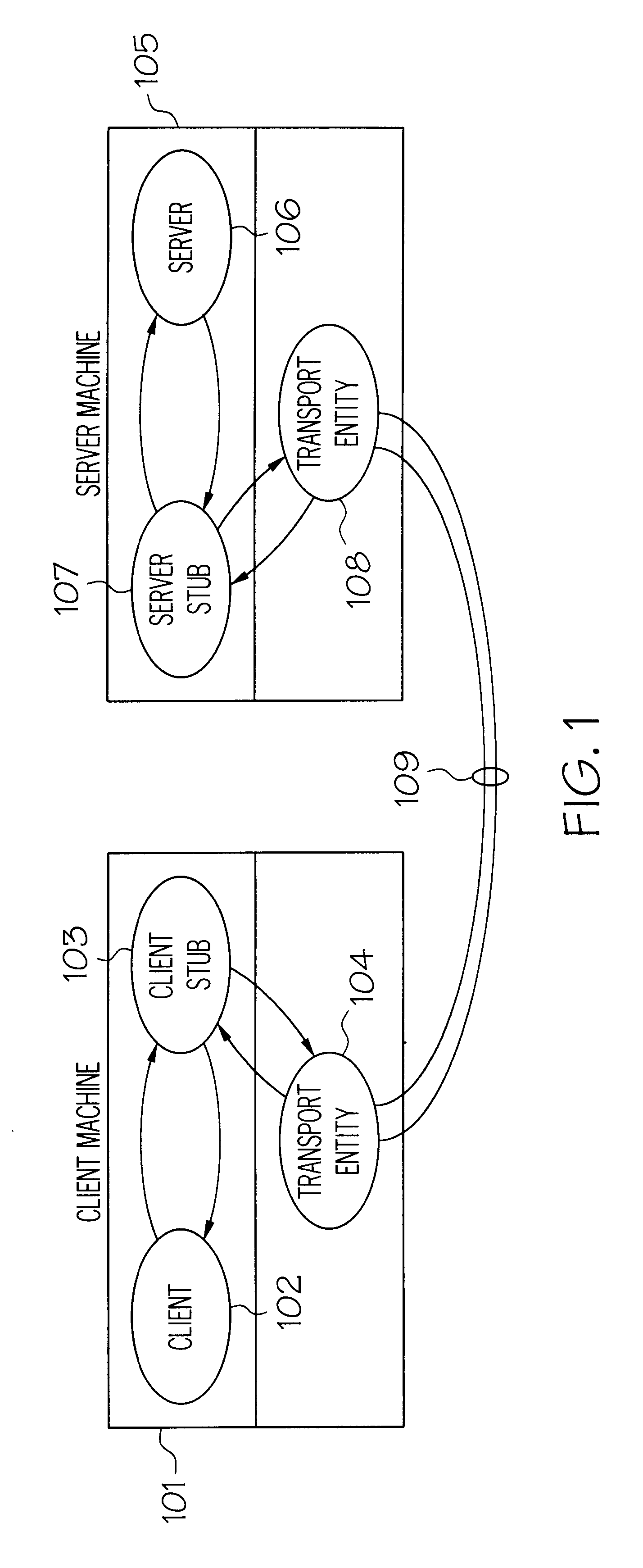
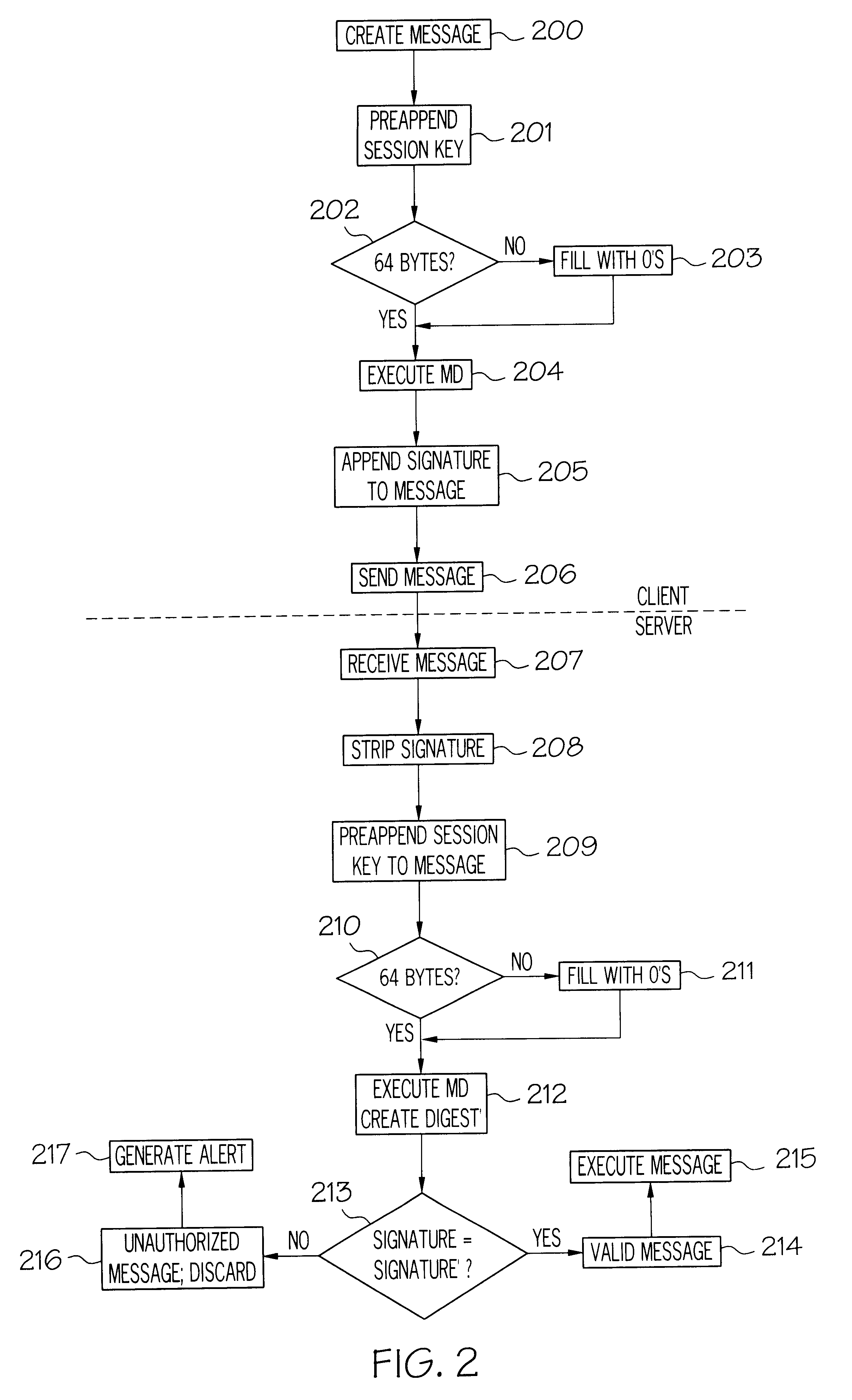
A method and apparatus for message authentication is described. In the following description, numerous specific details, such as message type, message length, etc., are provided in detail in order to provide a more thorough description of the present invention. It will be apparent, however, that the present invention may be practiced without these specific details. In other instances, well-known features are not described in detail so as not to unnecessarily obscure the present invention.
The present invention provides a signature with each message that identifies and authenticates the sender. In addition, the invention tracks state information about the session and uses its cumulative effect to help protect and authenticate senders.
The signature scheme of the invention takes advantage of an operation known as "message digesting". Message digesting is a scheme to provide data integrity and detect errors. There are a number of message digesting algorithms available for use, some of wh...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com