Network access and profile control
a network access and profile control technology, applied in the field of network access and profile control, can solve the problems of many different network connections, computer connections to unknown or unwanted networks, and connection to such networks, and achieve the effect of slowing down the computer's ability to conn
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
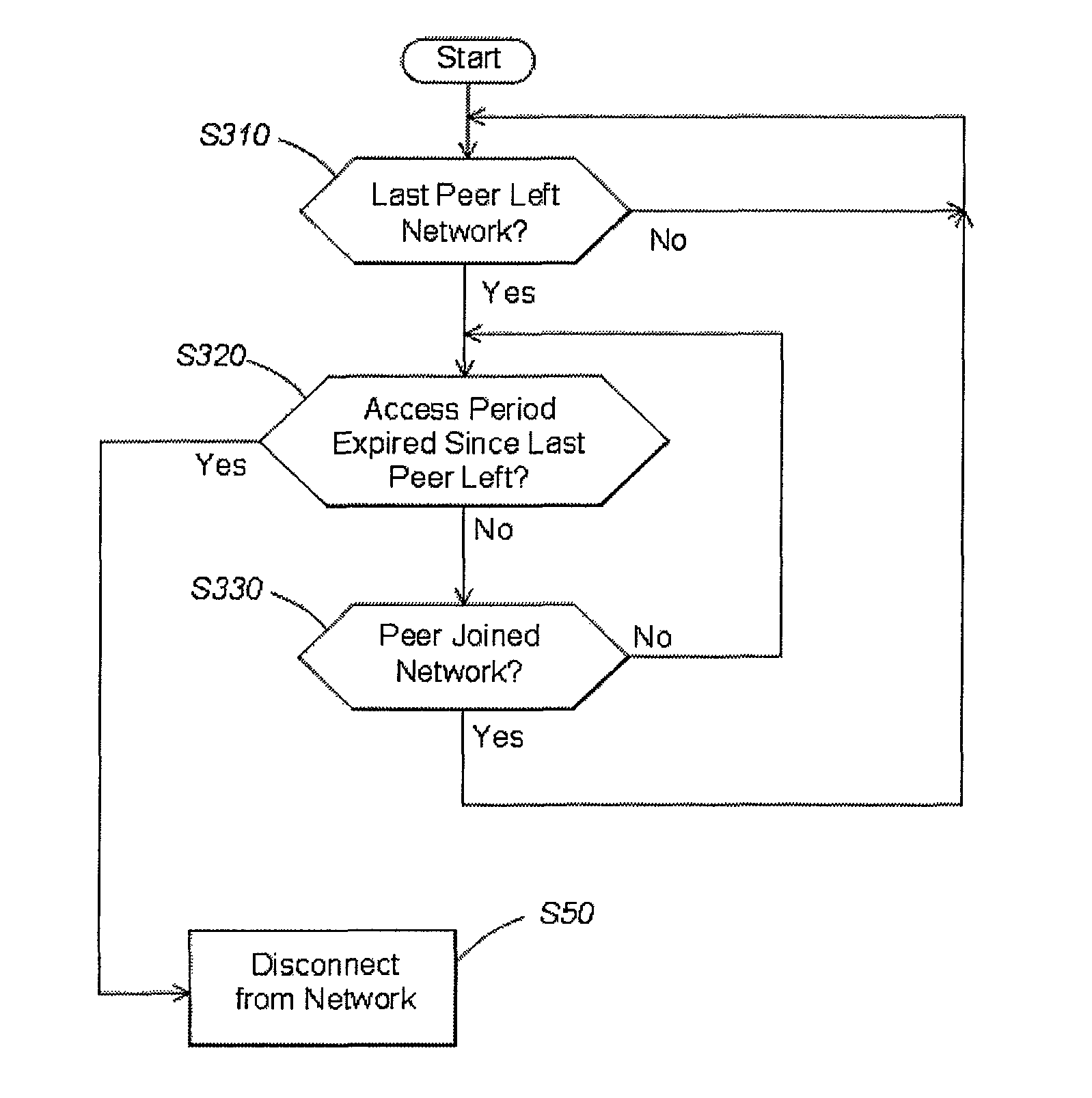
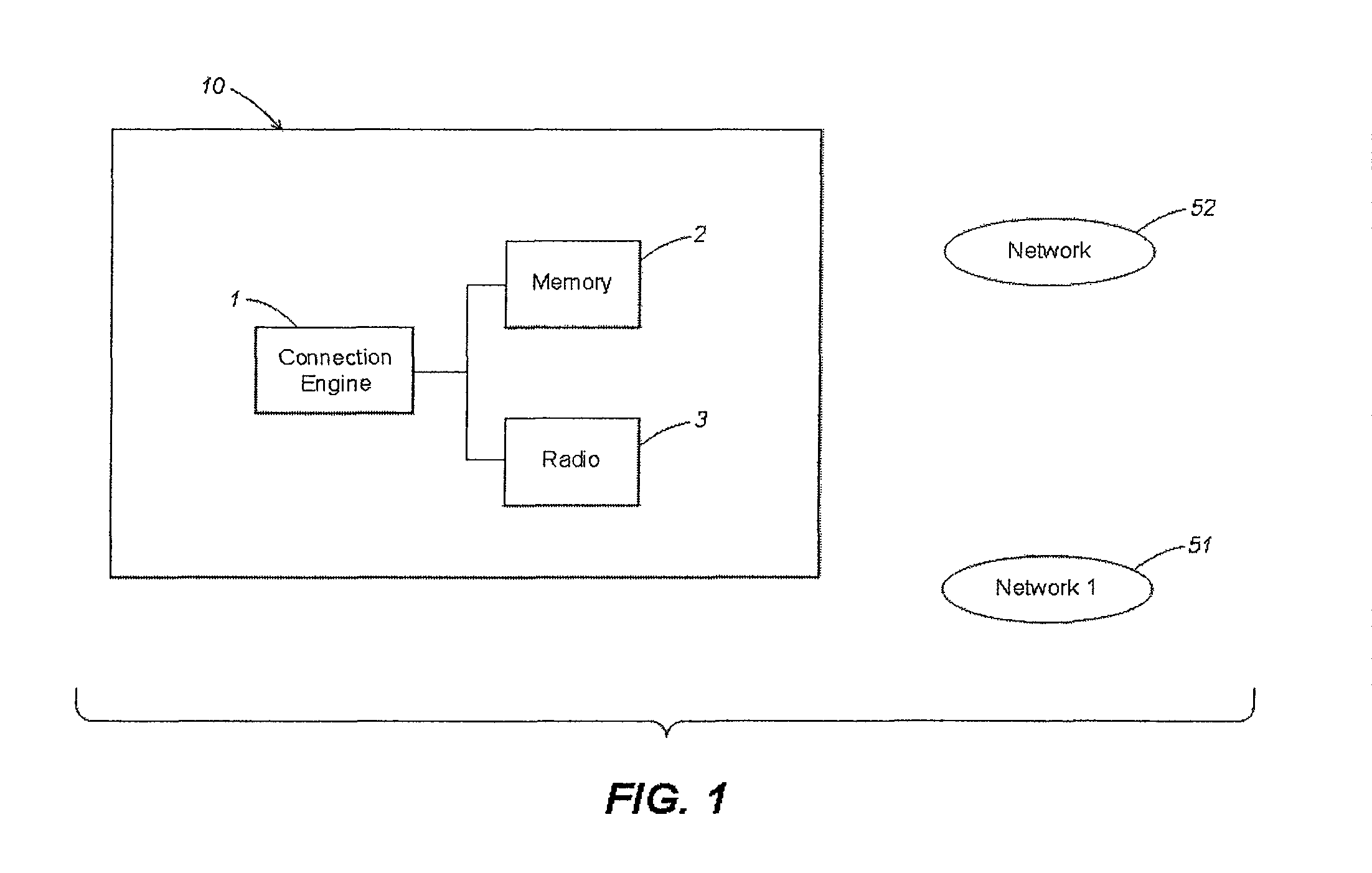
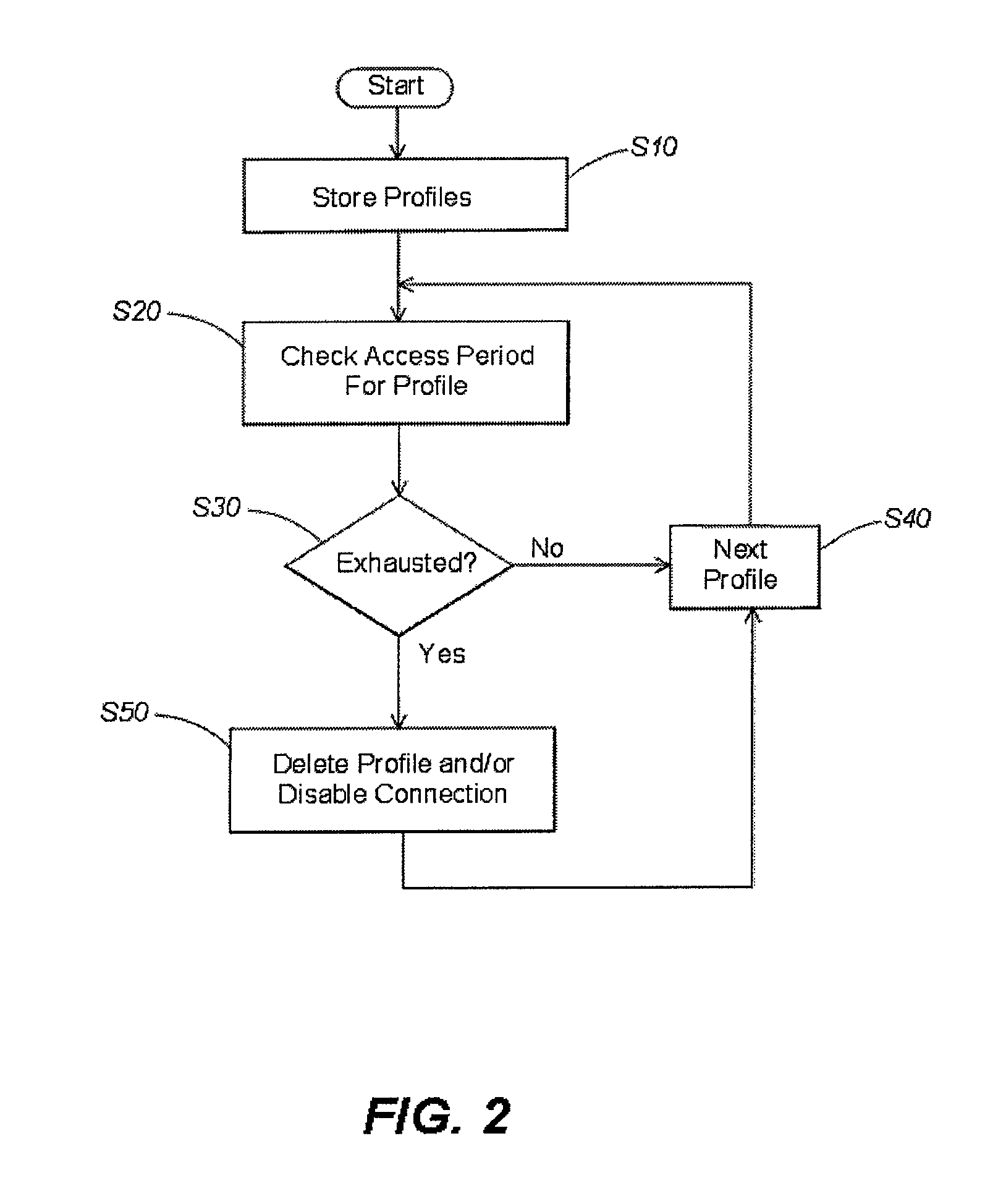
[0018]Aspects of the invention are described below with reference to illustrative embodiments. However, it should be appreciated that aspects of the invention are not limited to any of the particular embodiments. For example, examples are provided below regarding communication of a computer with one or more wireless networks. However, it should be appreciated that aspects of the invention may be employed in environments in which the computer communicates with one or more wired networks or other arrangements. In addition, the examples below include the computer acting as a client within the network. However, it should be understood that the computer may function as an access point or other similar device in a network, as well as functioning as a client in one or more other networks. Also, as mentioned above, illustrative embodiments are described using the term “computer” to refer to the device on which network profiles or other network access parameters are managed. However, it shou...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com