Systems and methods for anonymous authentication using multiple devices
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
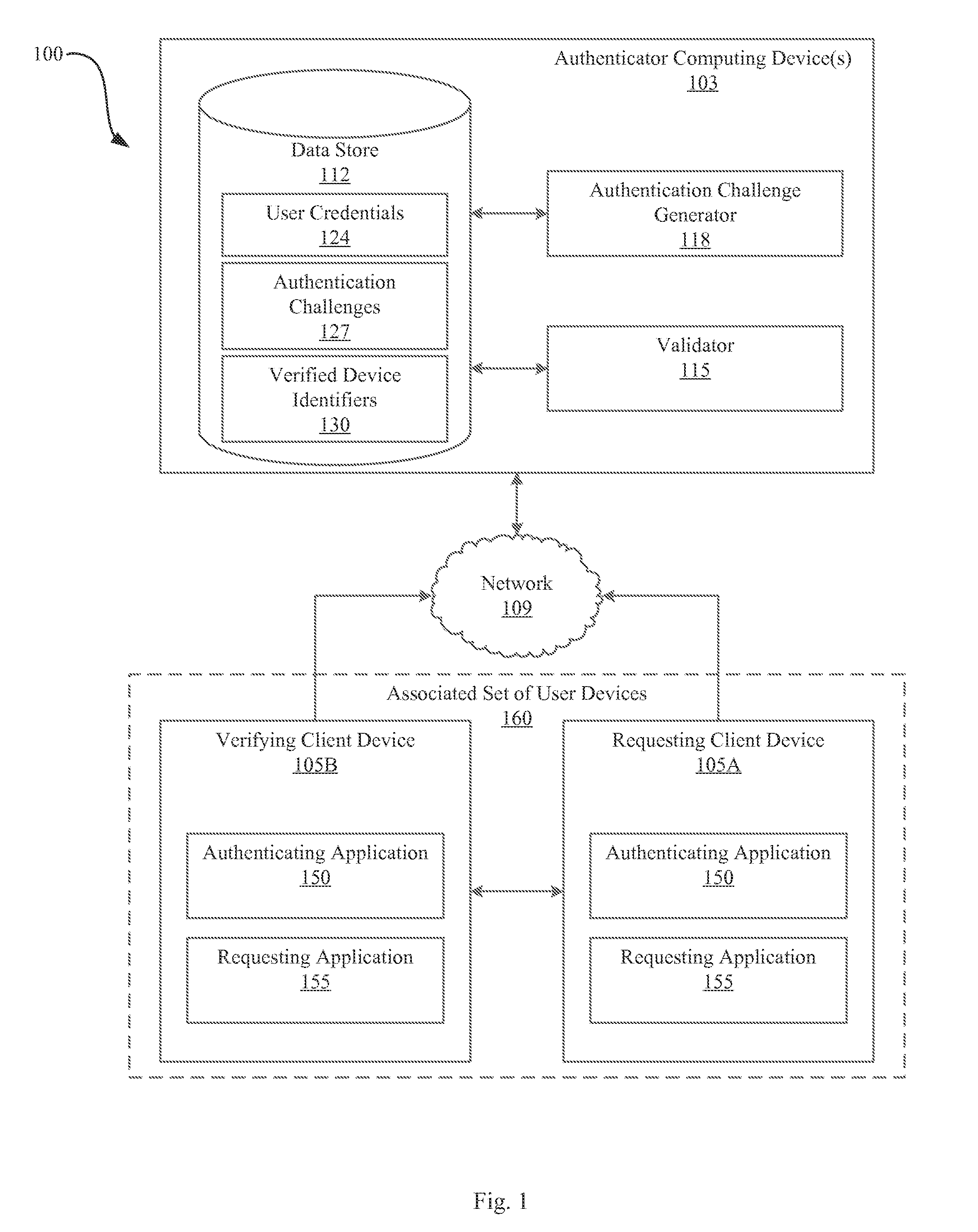
[0025]The present disclosure describes systems and methods for authenticating “users” (which can be human users, devices, processes, clients, etc.). Authentication decisions can be based on the existence of cryptographic signatures from some set of devices (sometimes referred to as “tokens”) associated with the user, During registration, the authenticator (e.g., an “authentication server”) can associate devices with users and / or each other. This description therefore uses the term “registered” to mean “associated”; the devices “registered” with a user are “associated” with that user and / or with each other. Each device can have one or more associated cryptographic keys (which, in some embodiments, can be shared with the authenticator and / or other devices). Although the authenticator can associate a plurality of devices with each user, the associated devices need not store any data indicating or identifying the existence of other devices associated with the same user. Instead, the aut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com