System and Method of Securing Private Health Information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
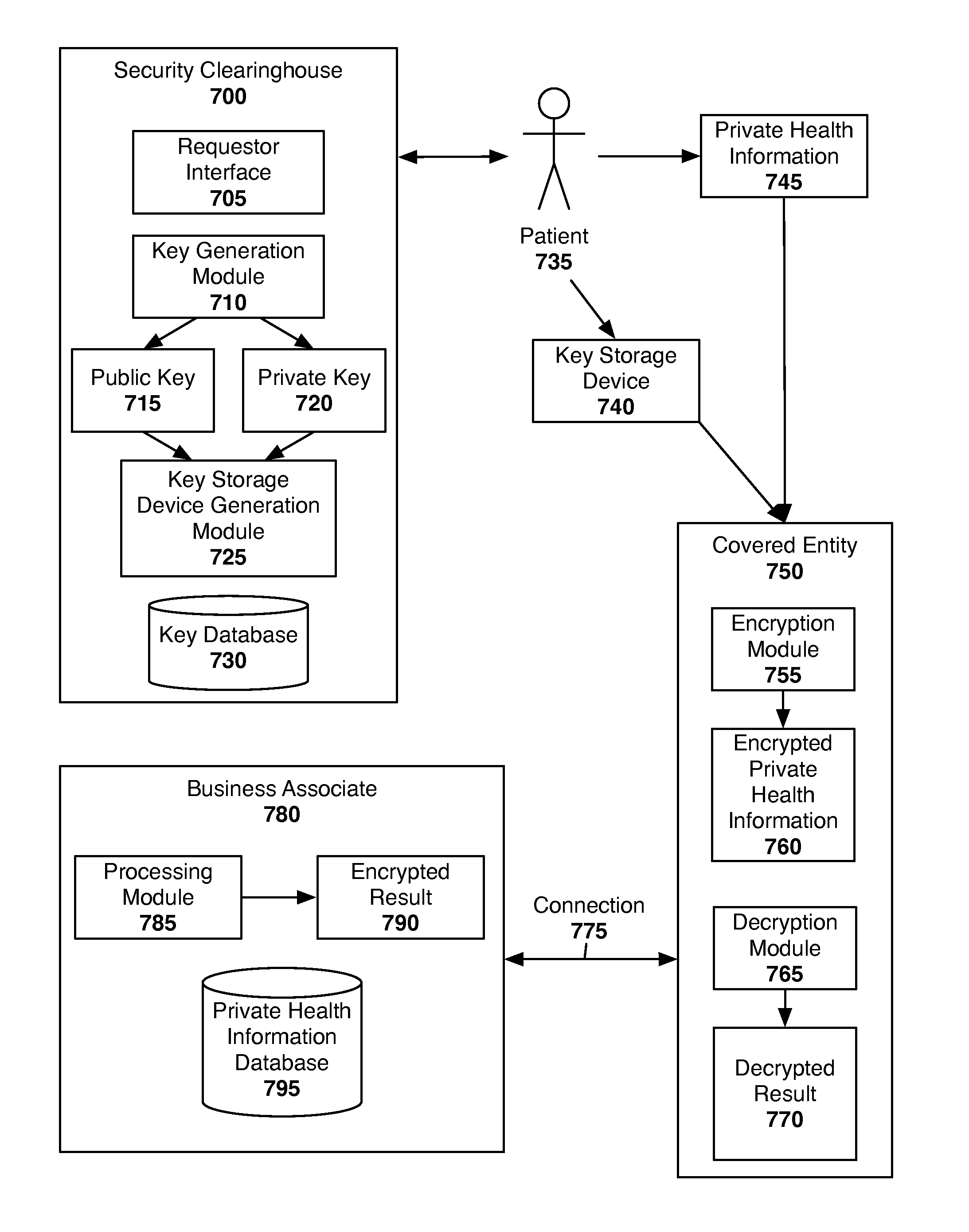
[0033]The preferred embodiment of the present invention will be described with reference to FIGS. 3 and 4.
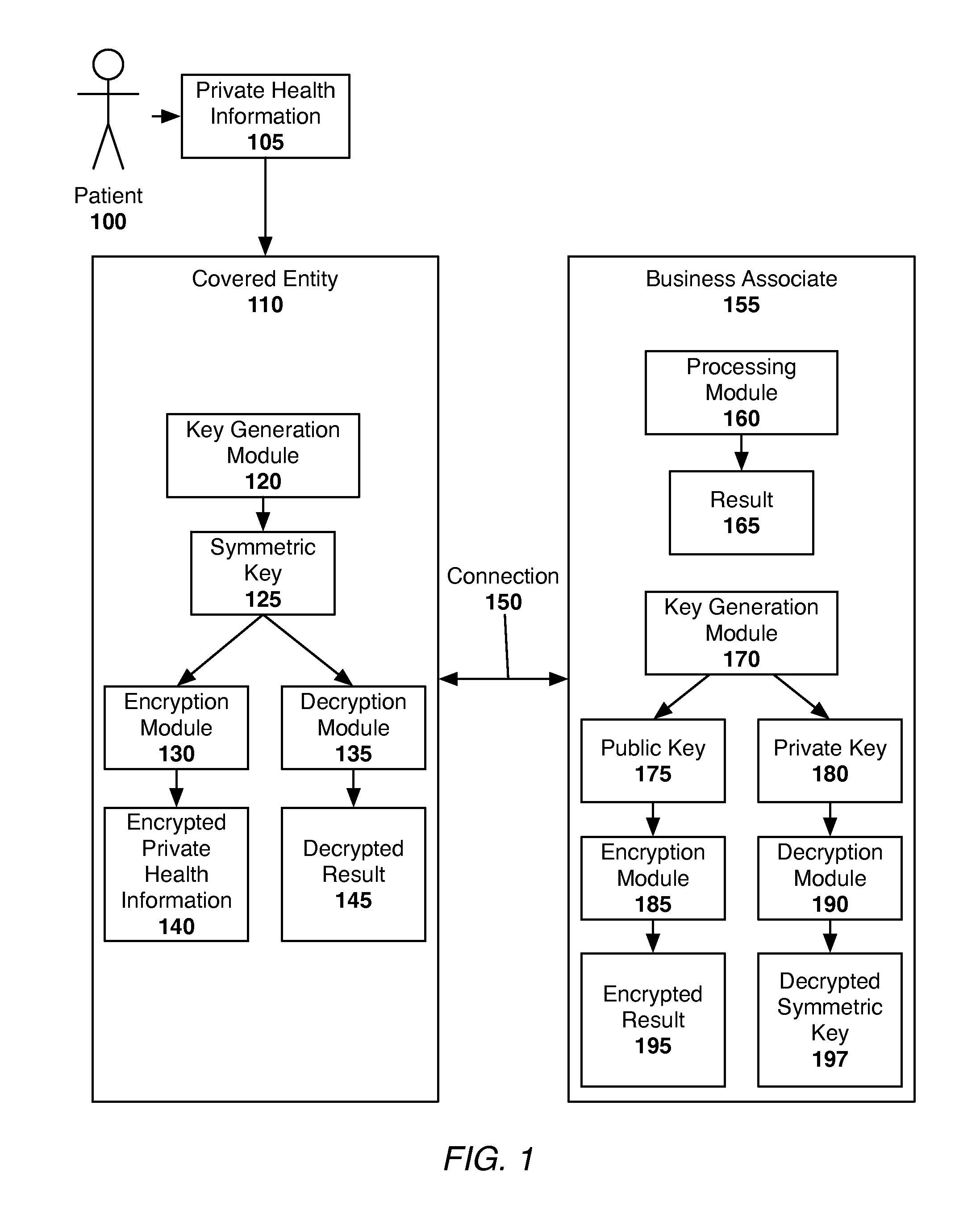
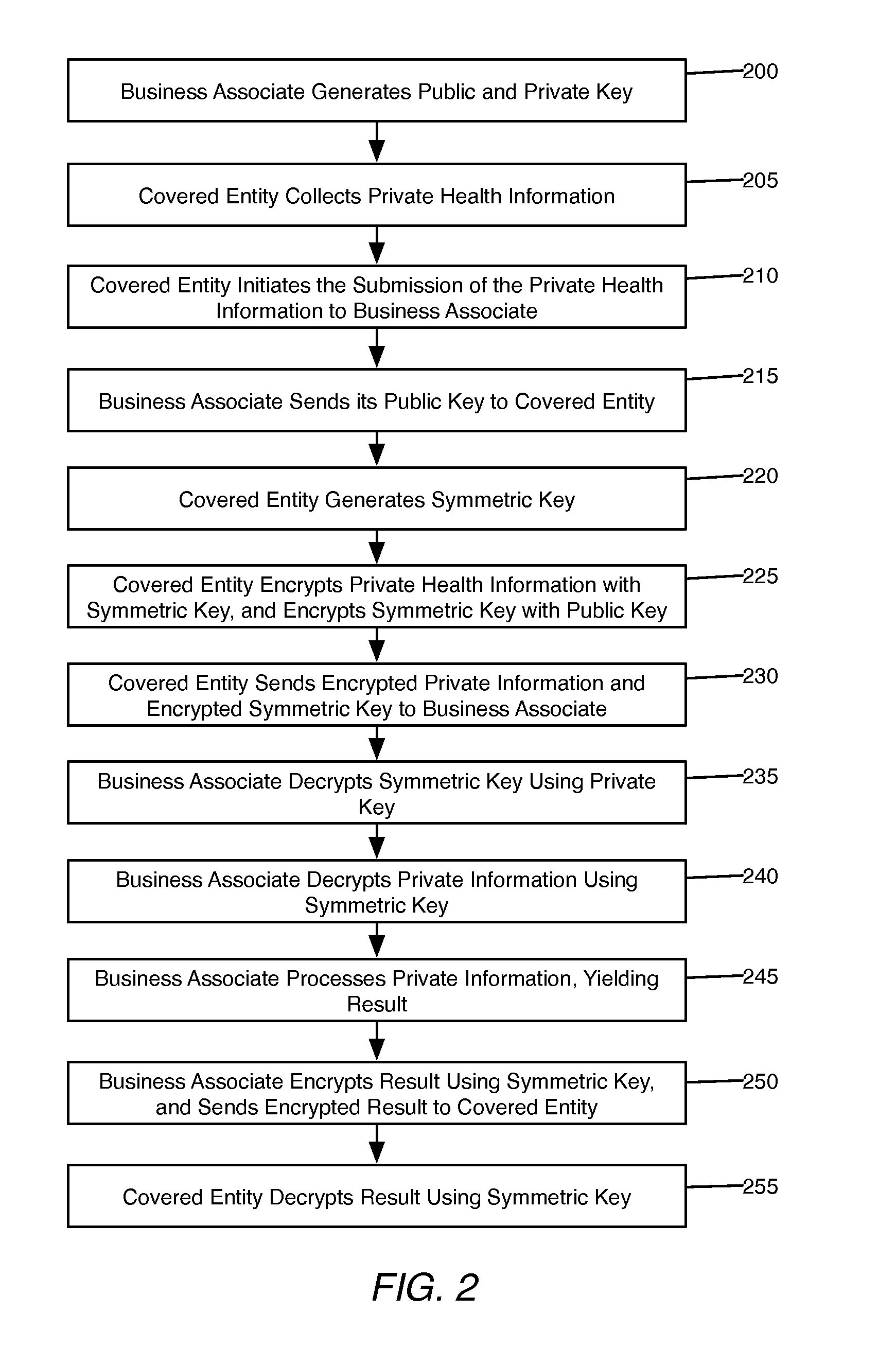
[0034]As depicted in FIG. 3, the patient 300 possesses private health information 305, which is provided to or collected by the covered entity 310. The private health information 305 may be any private information of the patient, such as information relating to the patient's physical or mental health or condition, the care provided to the patient, demographic information, or information regarding the patient's payment for care. The covered entity 310 may be any person or entity that collects private health information of patients, such as a health care provider, a medical professional, a health care clearinghouse, or a health plan. The covered entity 310 wishes to take advantage of the services offered by the business associate 380. The business associate 380 may offer any number of services or software applications relating to the processing of private health information. For e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com