Transaction authorisation system & method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
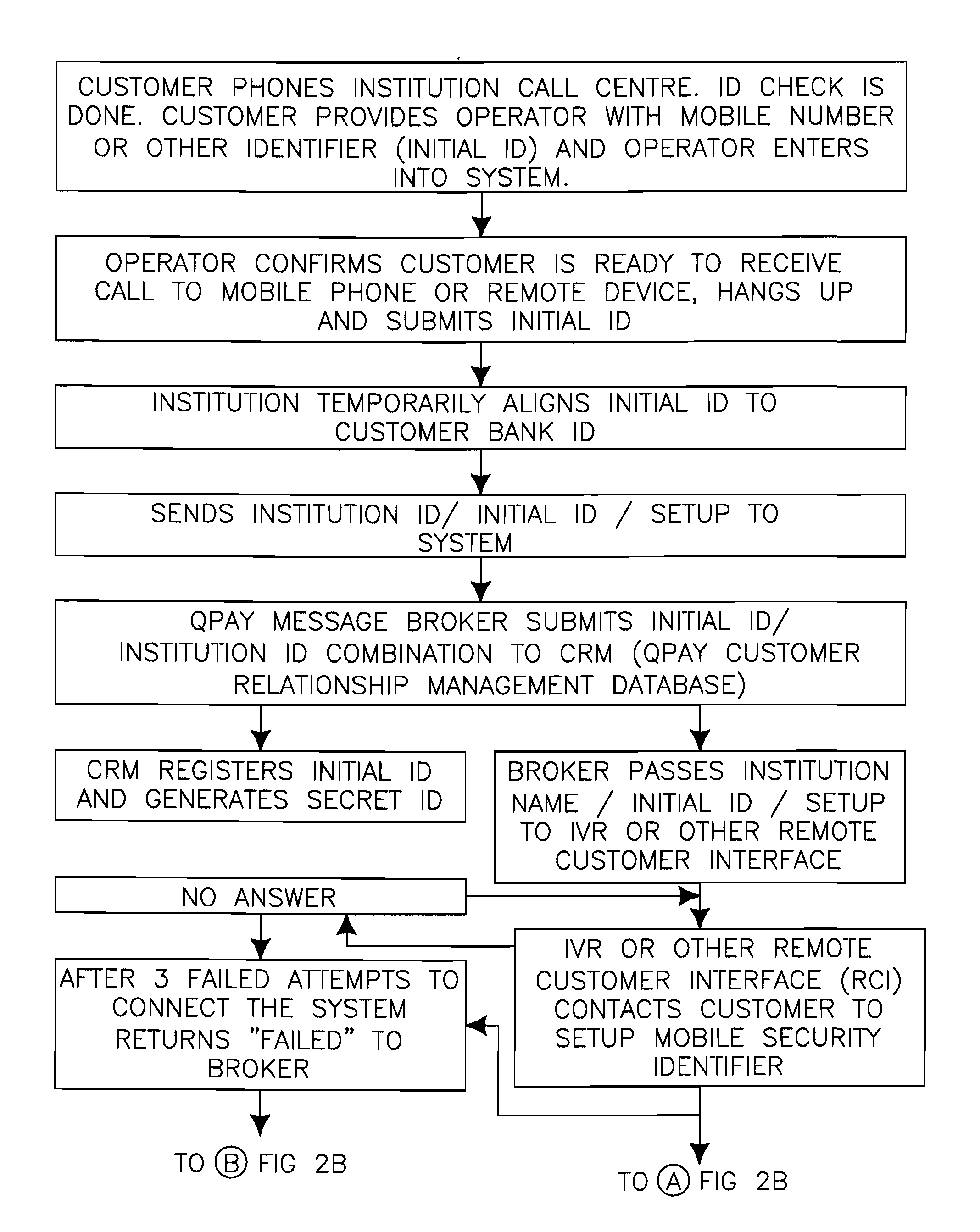
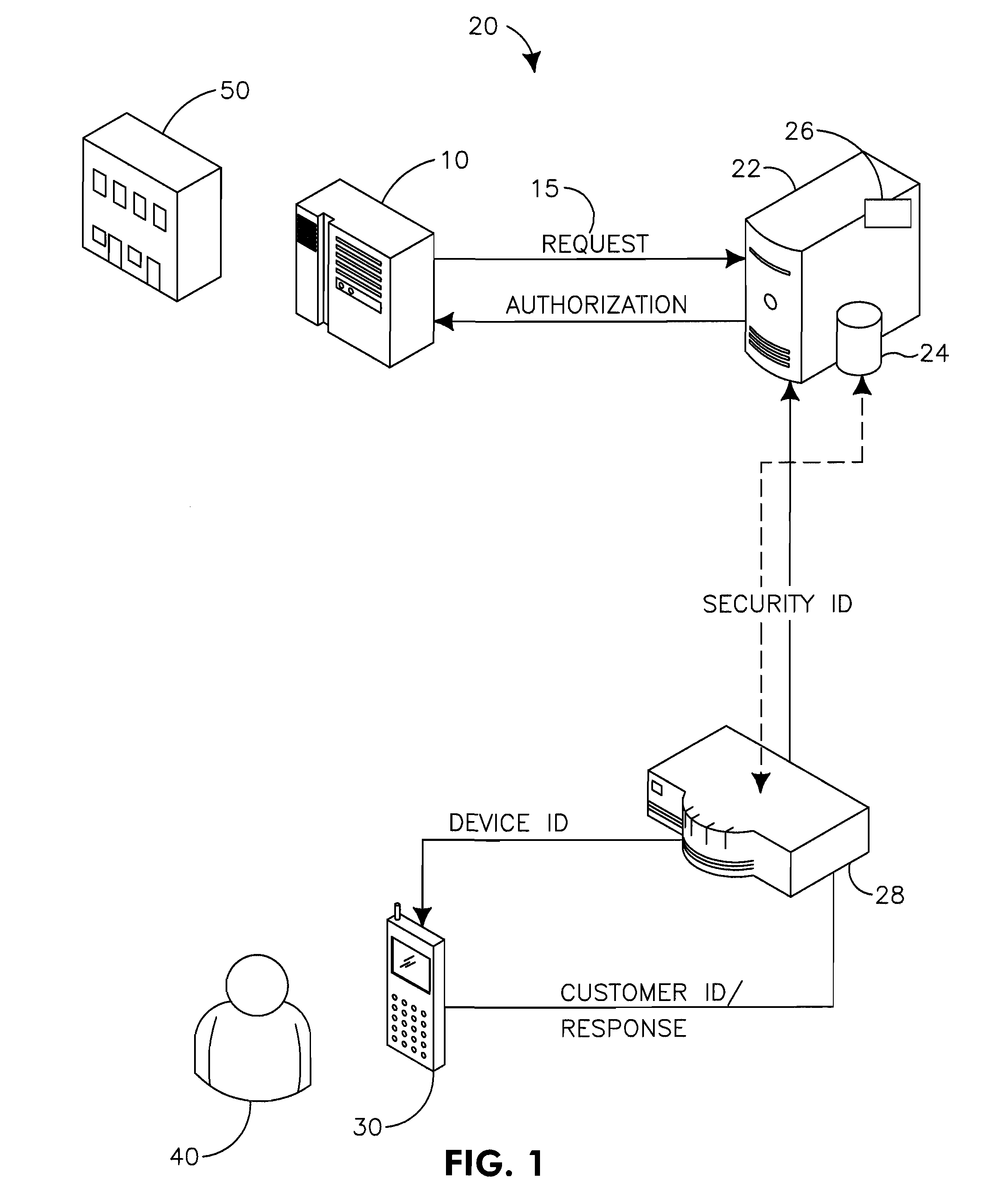
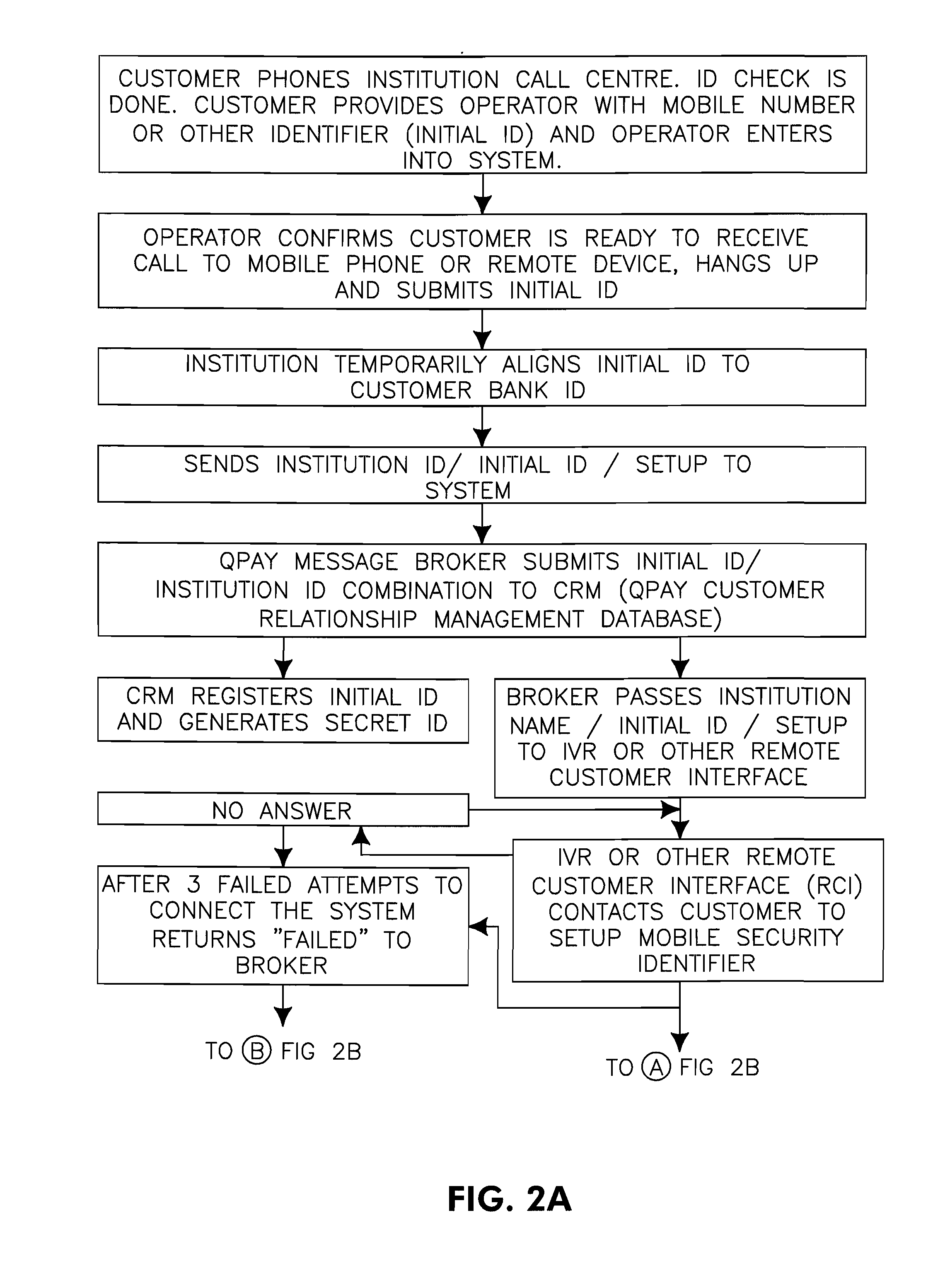
[0079]The present invention is not specific to any particular hardware or software implementation, and is at a conceptual level above specifics of implementation. It is to be understood that various other embodiments and variations of the invention may be produced without departing from the spirit or scope of the invention. The following is provided to assist in understanding the practical implementation of particular embodiments of the invention.
[0080]The authorisation system 20, as shown in FIG. 1, includes a data processing means, i.e. server 22, with communication means 26 which communicates with an institution system 10 of an institution 50 and a customer device 30 of a customer 40. The customer 40 is generally a customer of the institution 50, but may be an employee, supplier, citizen relating to a government agency or similar. In various circumstances, therefore, the customer 40 may be identified by the institution system 10 using any form of public identification data (Publi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com