Systems and methods for performing secure network communication
a network communication and biometric technology, applied in the field of systems and methods for performing biometrically secure transactions, can solve the problems of increasing difficulty in participating in certain online and in-person transactions safely and securely, fraud, and endangering the privacy of transactions performed using the host computer
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
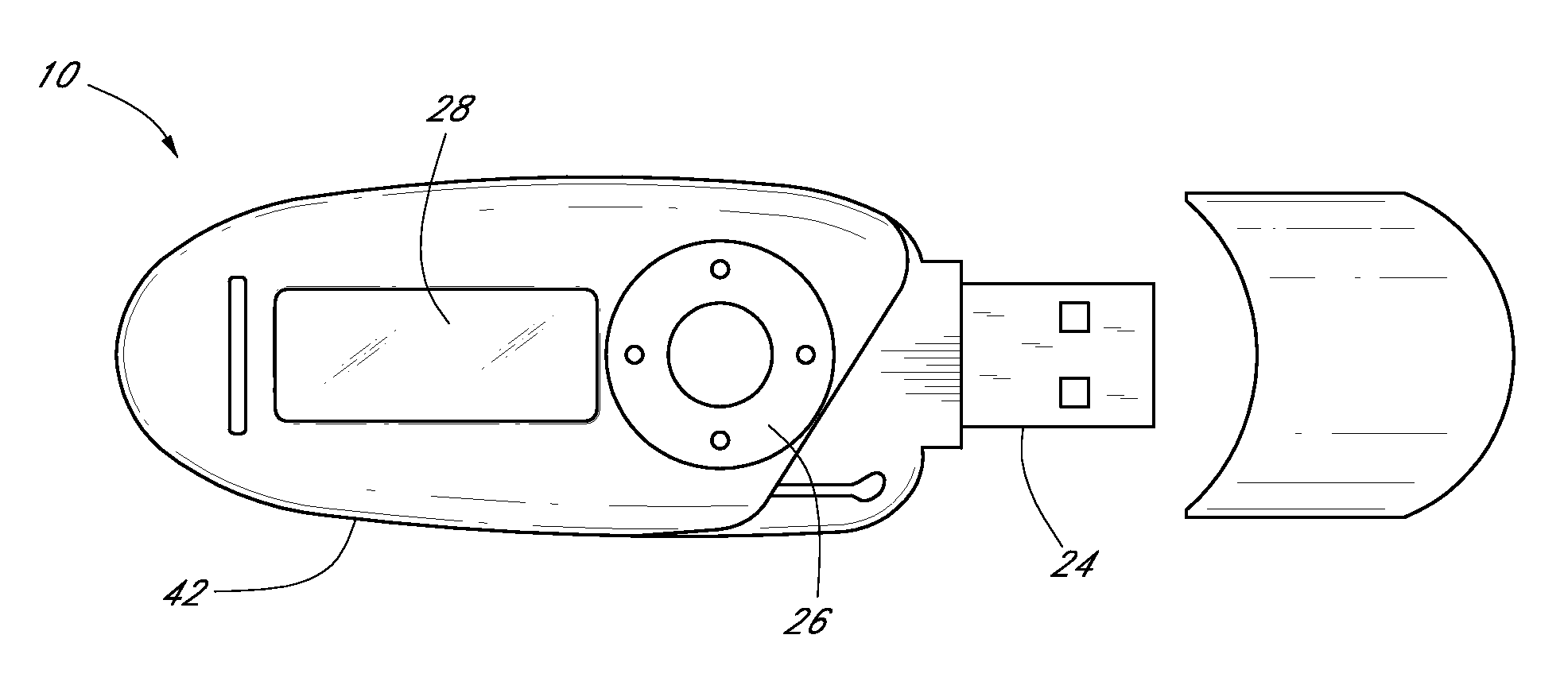
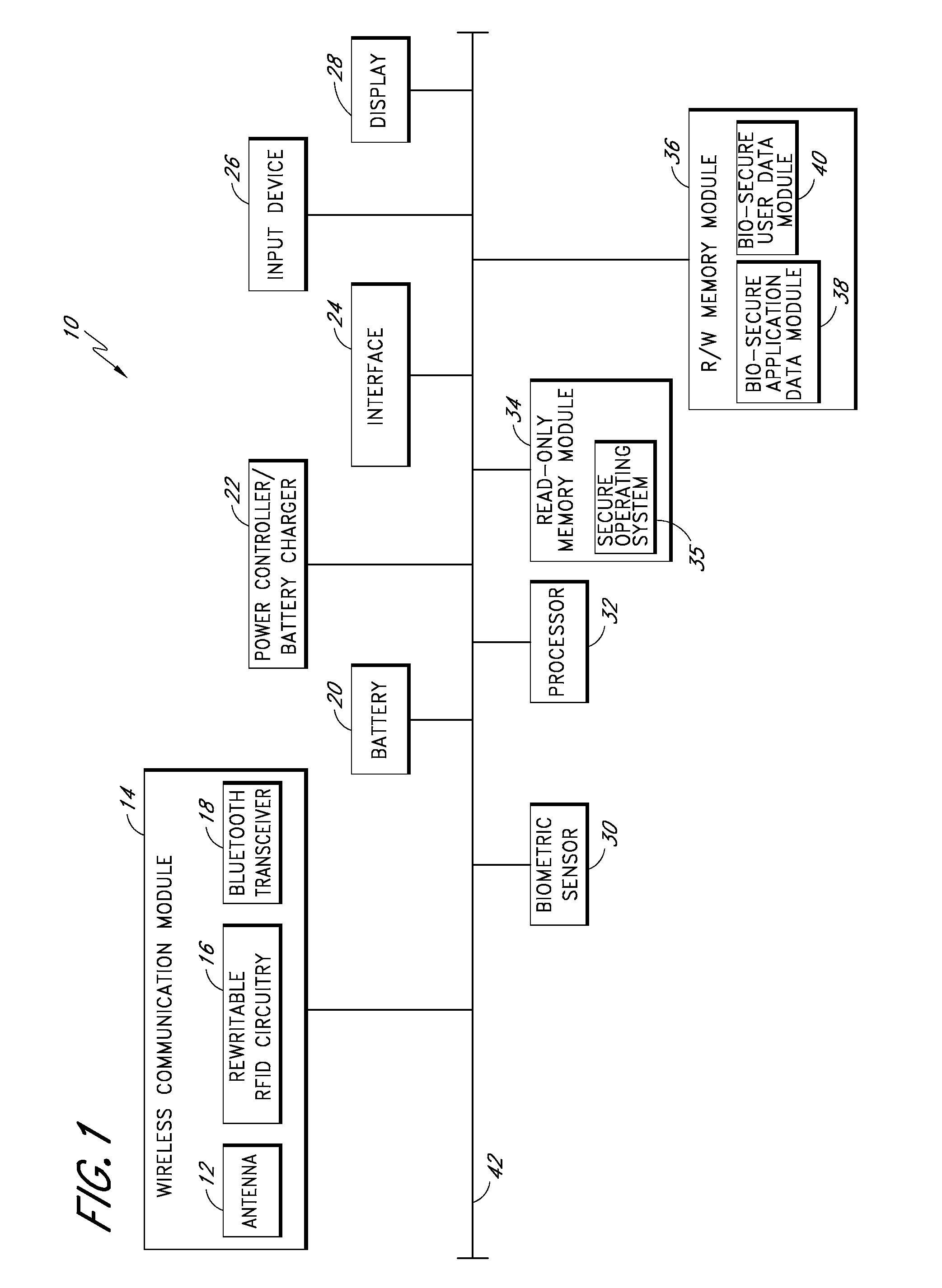
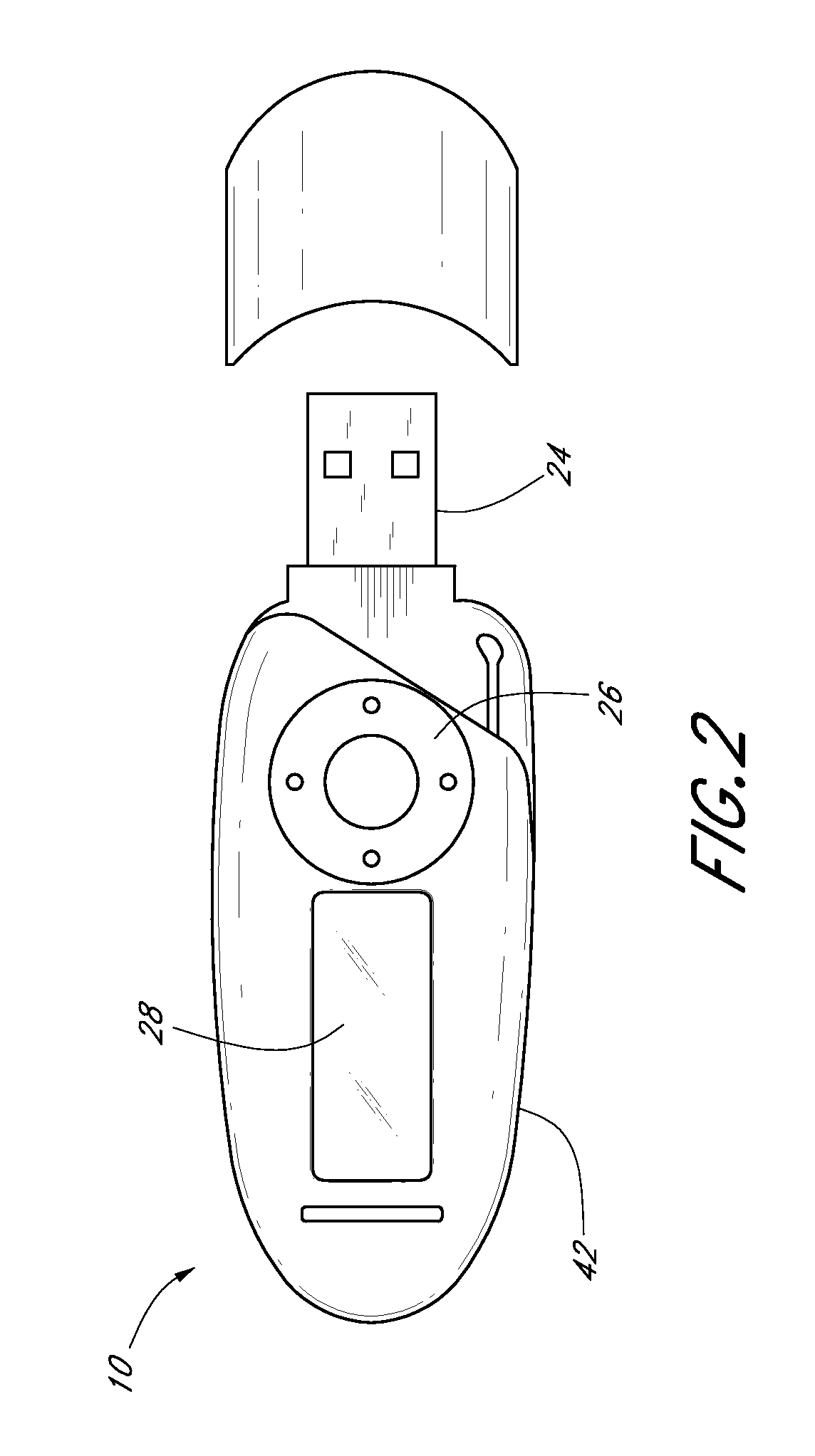
[0053] Devices, systems, and methods for performing biometrically-secured in-person and online transactions using a biometrically-secured device are disclosed. Various types of transactions are supported, including financial transactions as well as electronic person-to-person communications, such as sending and receiving emails. Other supported transactions include the transmission of entry codes for buildings or vehicles, for example, and the act of accessing electronic files from a remote computer or data storage device.
[0054] In certain embodiments, the biometrically-secured device is a portable device similar in appearance to a flash drive (e.g., a “jump drive” or a “thumb drive”). In some embodiments, the portable device includes a biometric sensor for performing biometric identity authentication of a user. Once the identity of a user has been biometrically authenticated, embodiments of the device can be used to complete a transaction involving a party whose identity is a desi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com