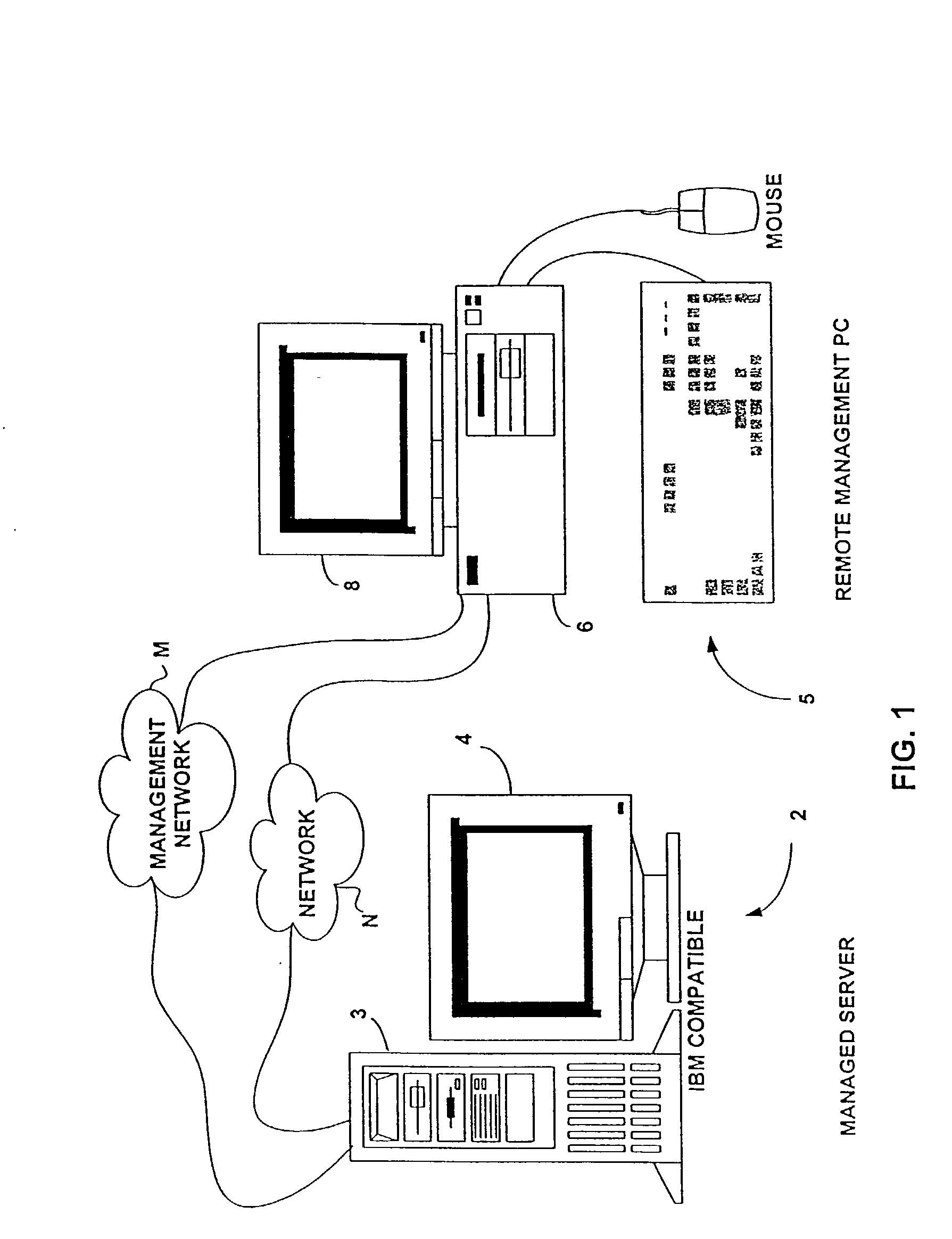
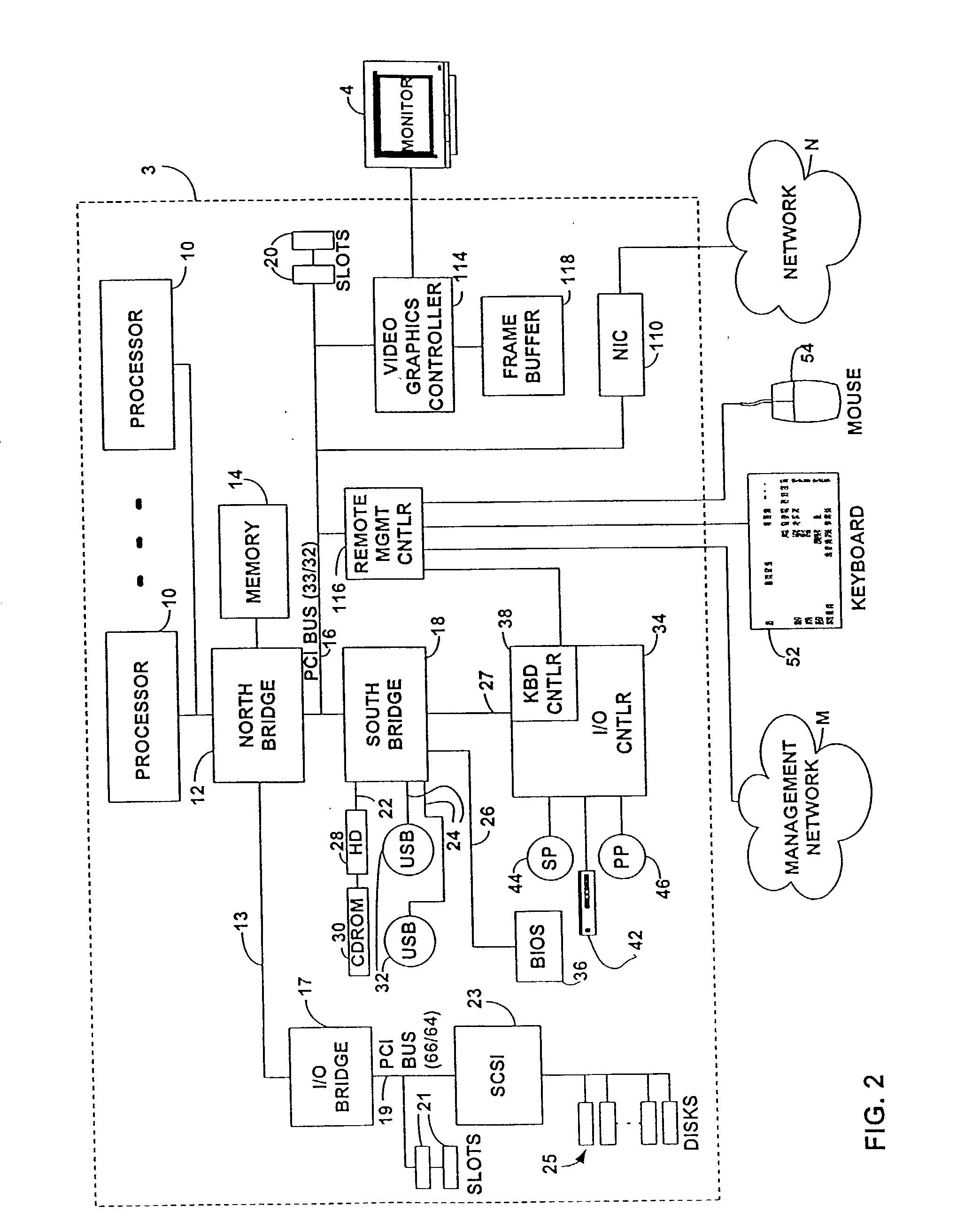
Method and apparatus for configuring security options in a computer system
a technology of security options and computer systems, applied in the field of computer security systems, can solve the problems of restricting in-band communication, presenting technologists with some challenging obstacles, and the sheer scope of modern computer networks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The following patents or patent applications are hereby incorporated by reference:
[0029] U.S. Pat. No. 5,898,861, entitled "Transparent Keyboard Hot Plug" by Theodore F. Emerson, Jeoff M. Krontz and Dayang Dai;
[0030] U.S. Pat. No. 5,790,895, entitled "Modem Sharing" by Theodore F. Emerson and Jeoff M. Krontz;
[0031] U.S. patent application Ser. No. 08 / 733,254, entitled "Video Eavesdropping and Reverse Assembly to Transmit Video Action to a Remote Console" by Theodore F. Emerson, Peter J. Michaels and Jeoff M. Krontz, filed Oct. 18, 1996; and
[0032] U.S. patent application Ser. No. 09 / 438,253, entitled "Operating System Independent Method and Apparatus for Graphical Remote Access" by Theodore F. Emerson and Wesley Ellinger, filed Nov. 12, 1999.
[0033] One or more specific embodiments of the present invention will be described below. In an effort to provide a concise description of these embodiments, not all features of an actual implementation are described in the specification. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com