Method for binding of access terminal and operators
A technology for access terminals and operators, applied in user identity/authority verification, data exchange through path configuration, digital transmission system, etc., to achieve the effect of simple implementation, avoiding vicious competition, and not changing the networking mode
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
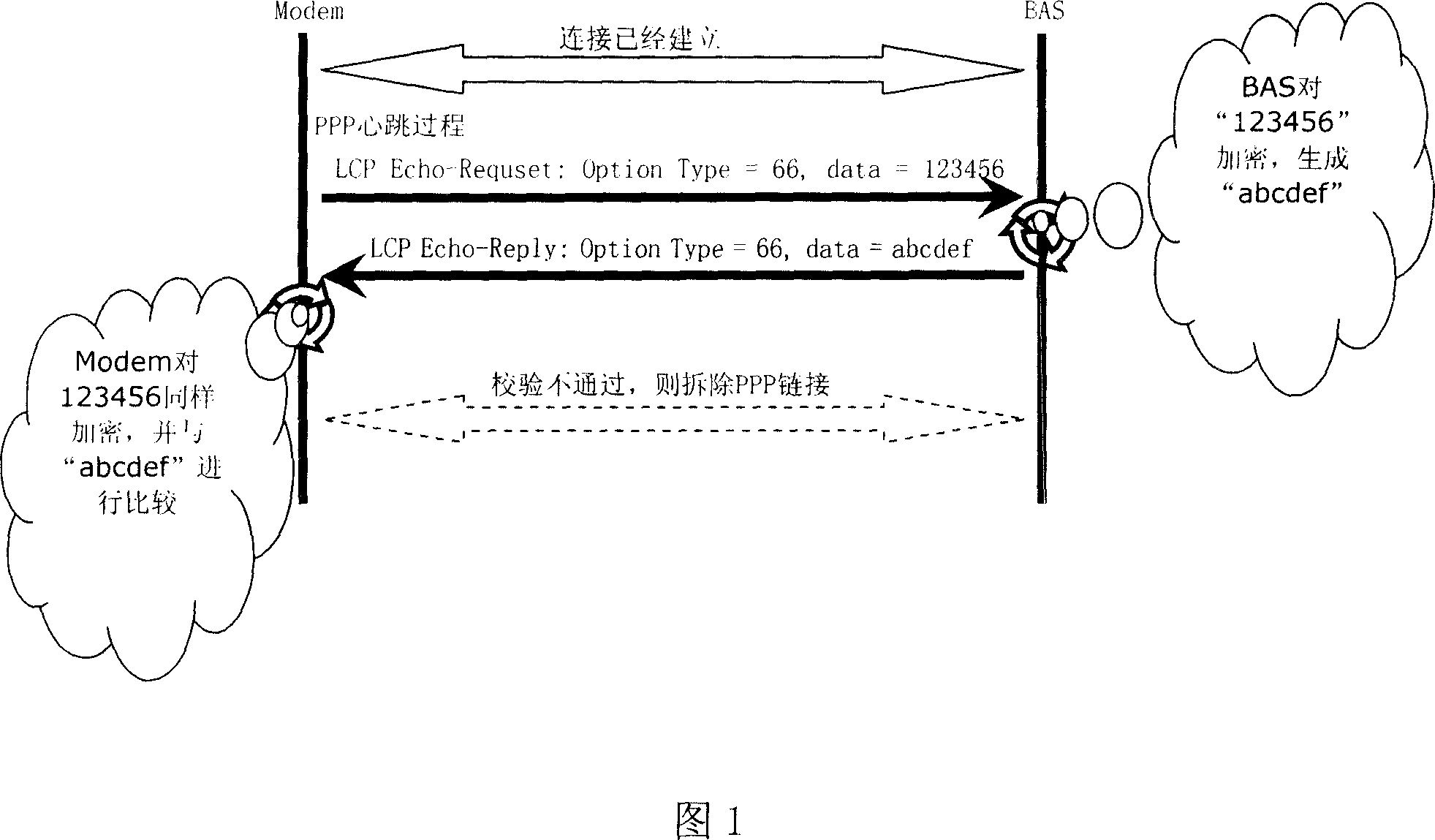
[0048] Embodiment 1: Identifying the access network through private information in routing mode
[0049] In routing mode, PPPoE dialing is initiated by Modem. The Modem adds the custom option to the LCP message, randomly generates the Data string, and the BAS encrypts the Data field and sends it back to the Modem through a response message. The Modem encrypts the Data field with the agreed encryption algorithm, and then the Modem Compare the encrypted Data field with the Data field received from the BAS, and if the two are inconsistent, the link is torn down.
[0050] The following takes the PPP heartbeat message as an example to illustrate this process, and the process is shown in Figure 1.
[0051] 1. After the connection is established, the Modem sends a heartbeat message to the BAS, which carries a custom option, option TYPE=66, and randomly generated Data=123456;
[0052] 2. BAS encrypts 123456 to generate abcdef;
[0053] 3. The BAS returns a heartbeat response messag...
Embodiment 2
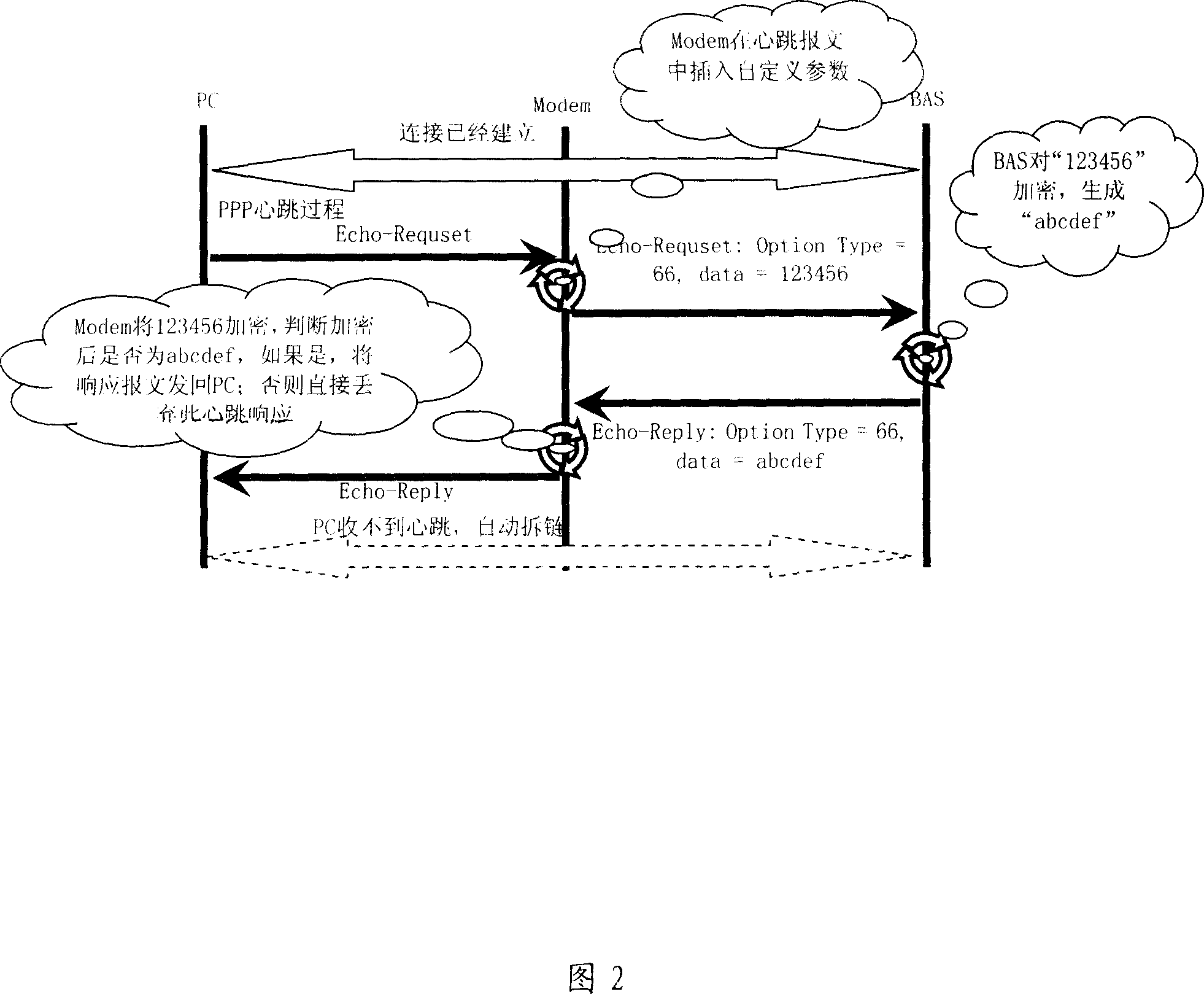
[0056] Embodiment 2: Identifying the access network through private information in bridge mode
[0057] In the bridging mode, the PPPoE dialing process is initiated by the PC, and a PPP detection point is added in the bridging process to intercept and analyze PPP packets. If it is uplink data, the Modem inserts extended parameters into the original message and sends it to the BAS for authentication. If it is downlink data, it will be verified by the Modem first, and then the extended parameters will be stripped off and sent to the PC.
[0058] Also take the heartbeat message as an example, the process is shown in Figure 2:
[0059] 1. The PC sends a heartbeat message to the BAS. If the Modem detects that it is a PPP message, it intercepts and analyzes it, inserts a custom option in the heartbeat message, option TYPE=66, randomly generated Data=123456, and then which is forwarded to the BAS;
[0060] 2. BAS encrypts 123456 to generate abcdef;
[0061] 3. The BAS returns a h...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com