Access control method for implementing binding MAC/IP of network device
A technology for access control and network equipment, applied in user identity/authority verification, data exchange through path configuration, electrical components, etc., can solve the problems that the switch cannot be connected in series with the hub, the maintenance work is large, and it is difficult to implement. , to achieve the effect of solving the problem of device access control, occupying low network bandwidth, and preventing malicious attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
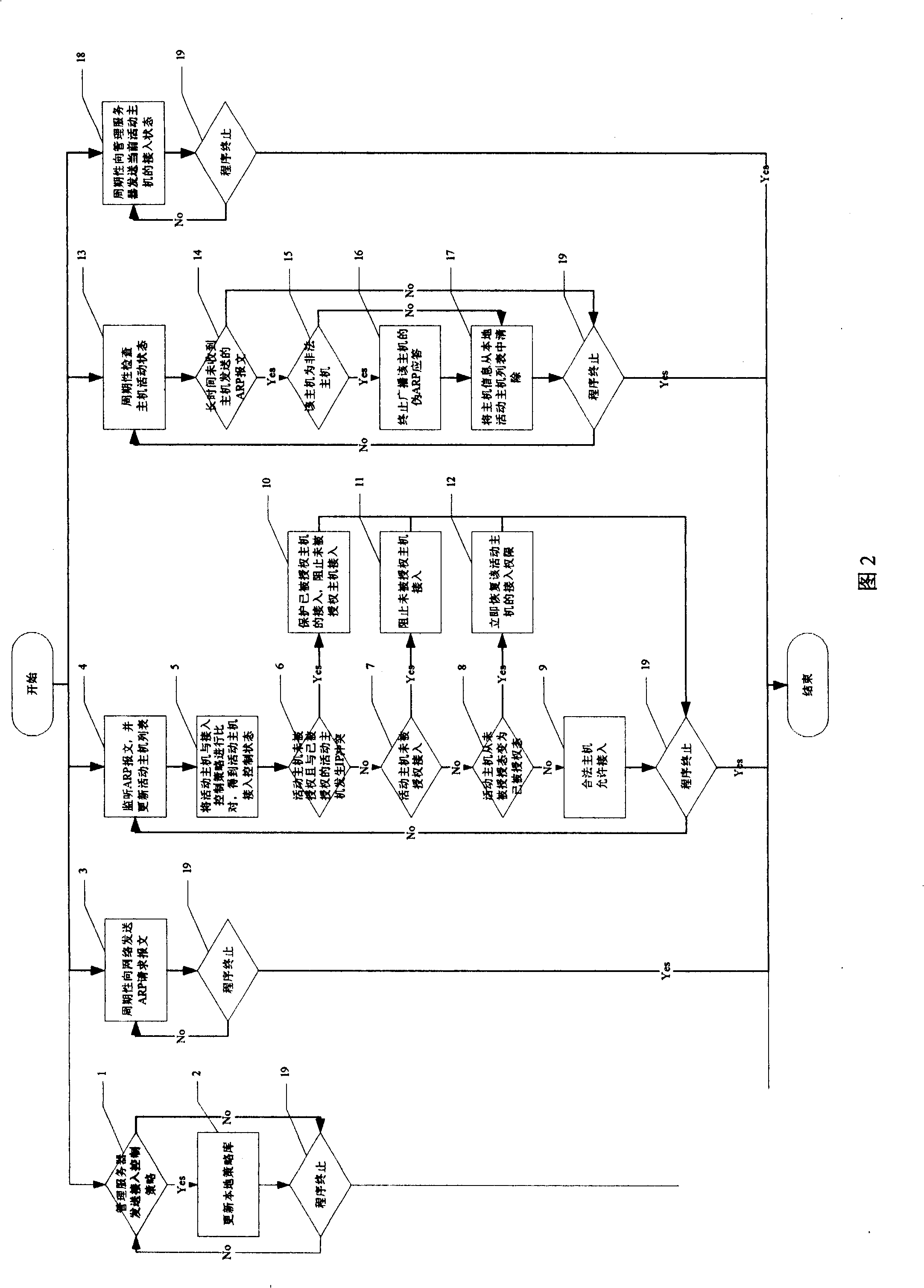
[0036] In order to further understand the content, characteristics and effects of the present invention, the following examples are given, and detailed descriptions are as follows in conjunction with the accompanying drawings:
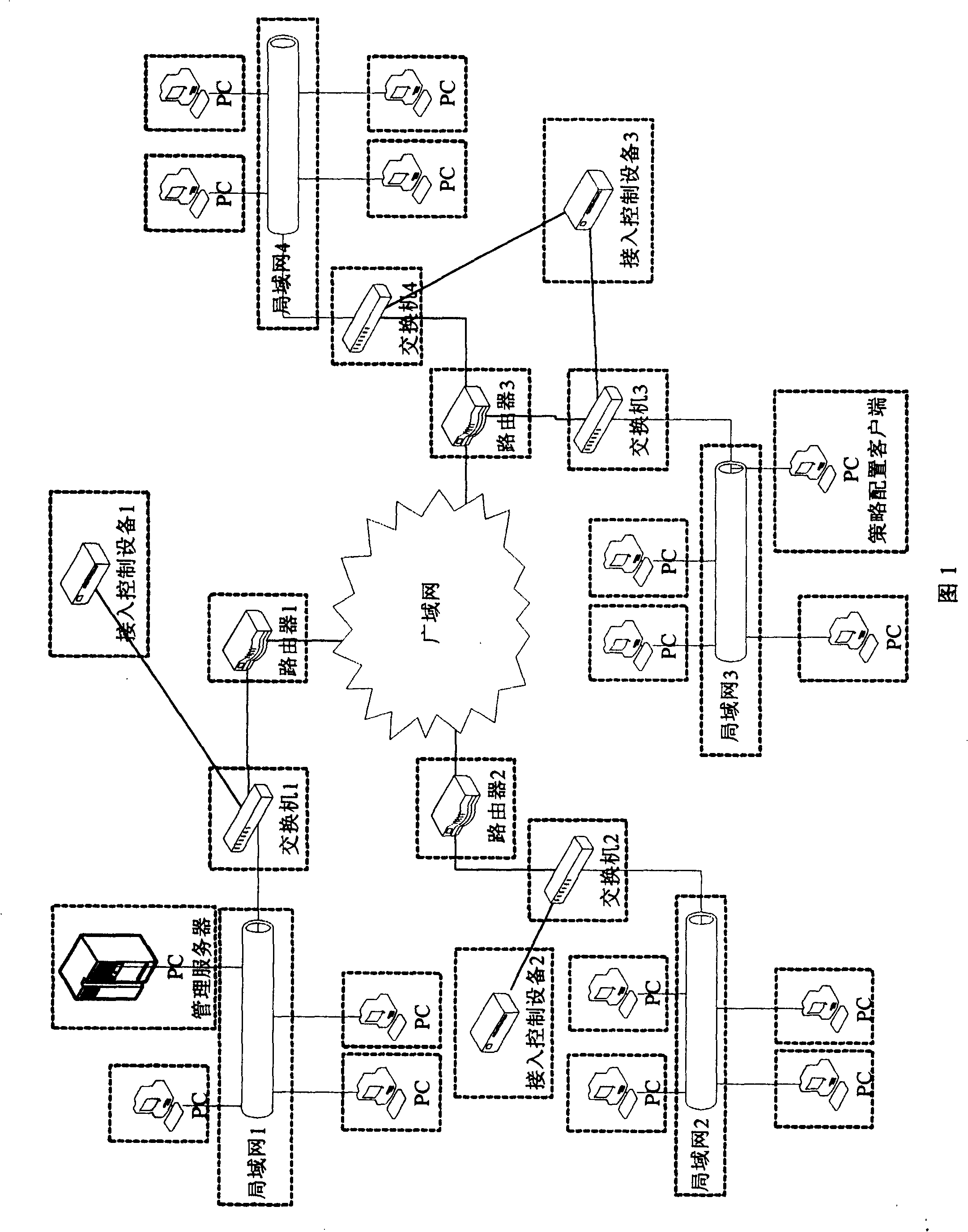
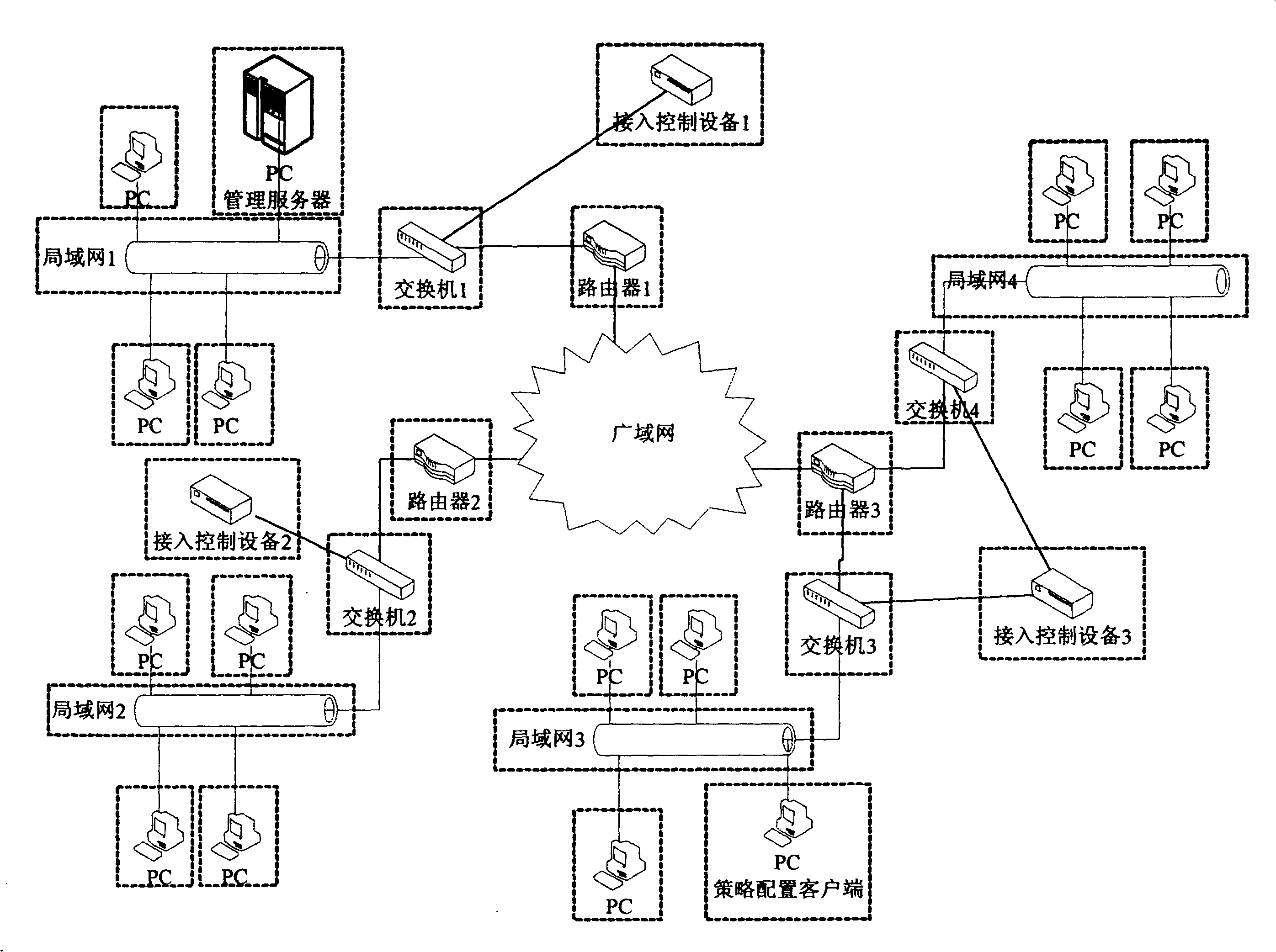
[0037] see figure 1 , if an enterprise has three physical locations: the first physical location has a LAN 1, which is connected to the WAN through the switch 1 and router 1 corresponding to the same network segment of the LAN 1; the second physical location also has a LAN 2, which is the same through the corresponding LAN 2 The switch 2 and router 2 of the network segment are connected to the WAN; the third physical location has LAN 3 and LAN 4, which are connected to the WAN through the switch 3 corresponding to the same network segment of LAN 3, and the switch 4 and router 3 corresponding to the same network segment of LAN 4 . The access control device 1 is connected to the switch 1 , the access control device 2 is connected to the switch 2 , and t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com