Access authentication method of 802.1x
A technology for access authentication and authentication system, which is applied in the field of 802.1x VMI logic port control and address acquisition, can solve the problems that restrict the application of 802.1X authentication mode, cannot solve address conflicts well, and restrict the development of wireless broadband networks. Eliminate single point of failure, eliminate network authentication and billing bottlenecks, and facilitate multi-service operations
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
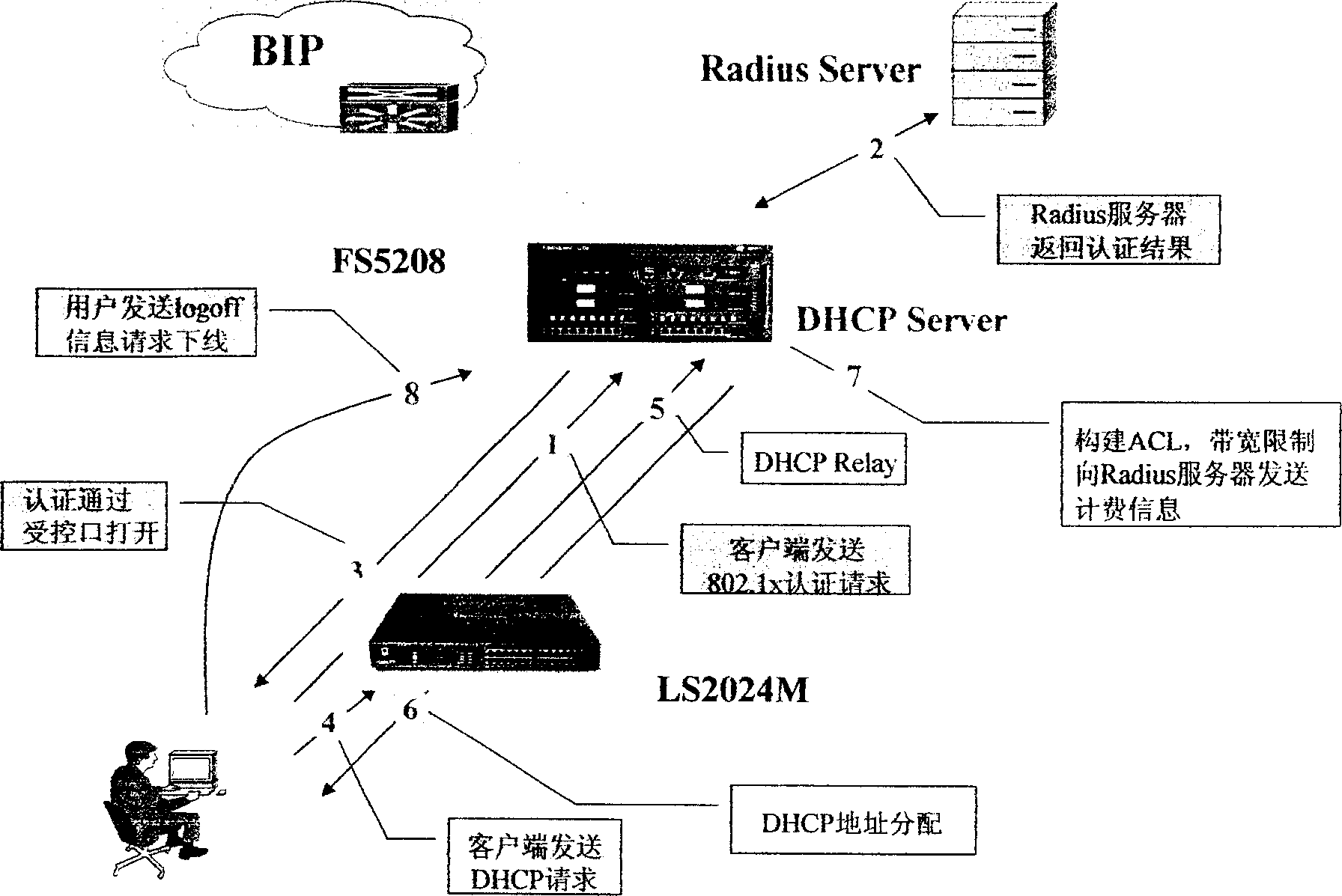
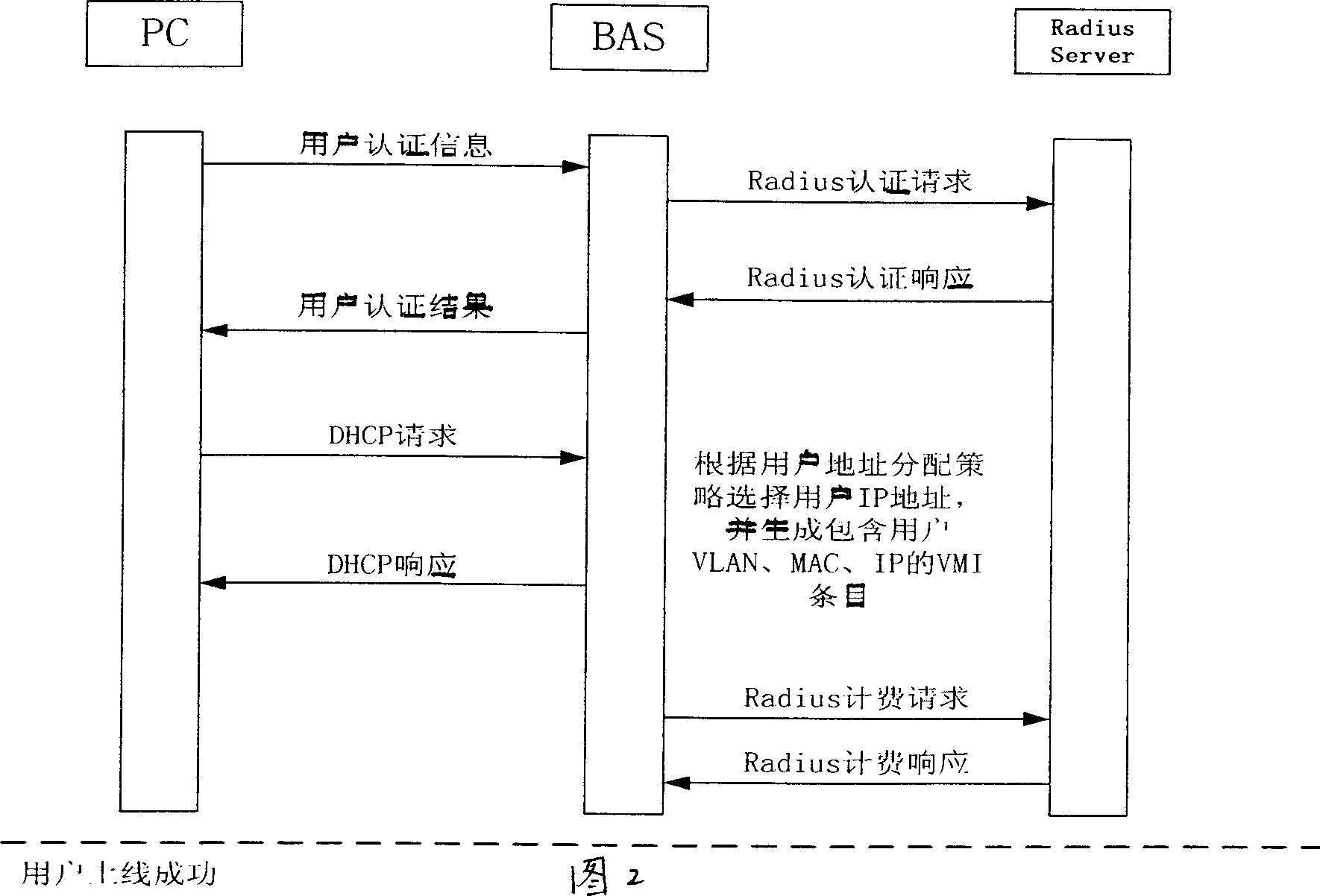
[0056] (1) The client initiates an 802.1x authentication request message, which is transparently transmitted to the access control device (BAS) through the Layer 2 network
[0057] (2) The BAS initiates an authentication request to the RADIUS server through the RADIUS CLIENT
[0058] (3) If the authentication is passed, the BAS returns an 802.1x authentication success message to the client
[0059] (4) The client initiates a DHCP address allocation request message
[0060] (5) Layer 2 network transparently transmits DHCP message to BAS
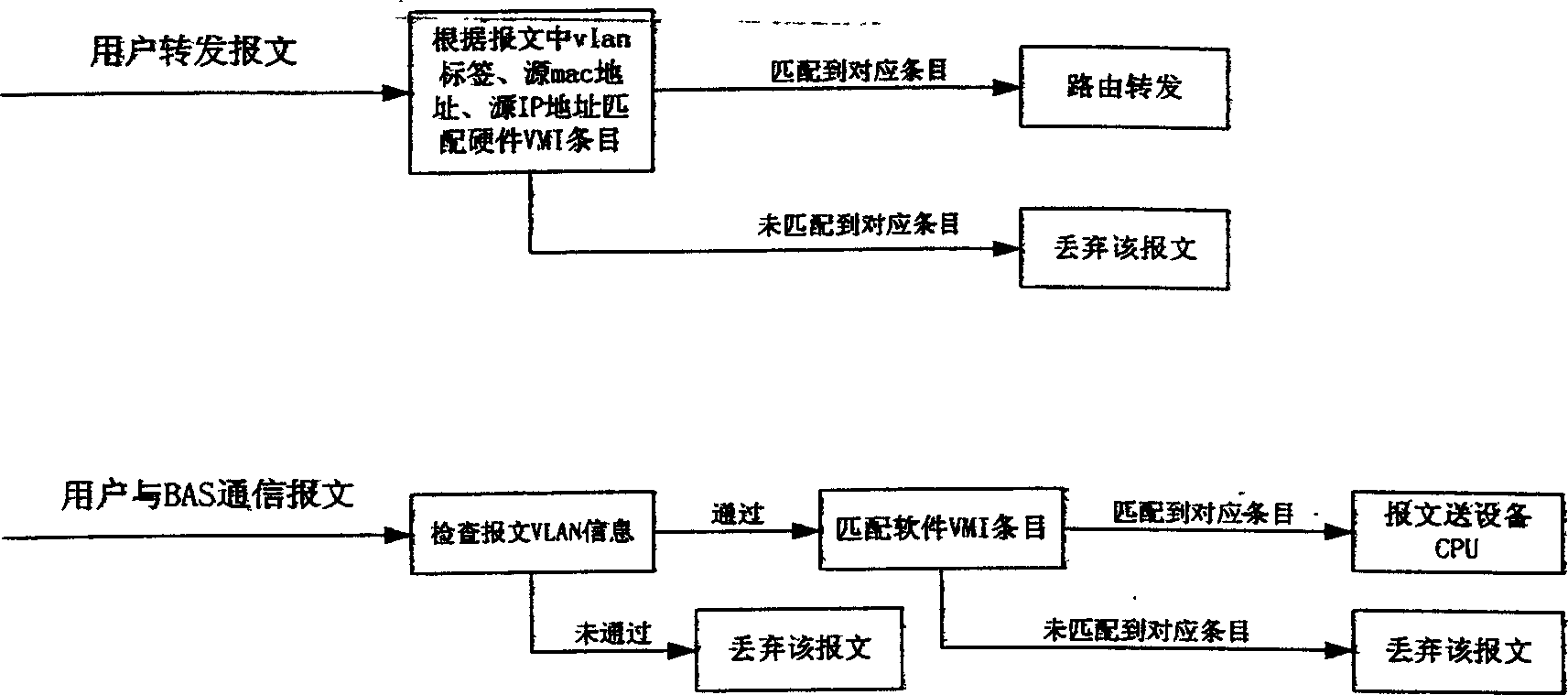
[0061] (6) The BAS assigns an address to the client. The client IP address allocation policy is specified by the radius server in the authentication pass response message. If the radius server does not specify a user address allocation policy, it is determined according to the user's domain. The DHCP server responds to the user's DHCP request according to the user's address allocation policy, and completes the assignment of the client's IP ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com