Fair safe electronic exchange method without third party
A safe transaction and fair technology, applied in the field of information security, can solve problems such as the inability to guarantee that the third party will not make mistakes, deceive or even collude, the third party cannot be reassuring, and the buyers and sellers cannot trust each other. The effect of realizing and enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
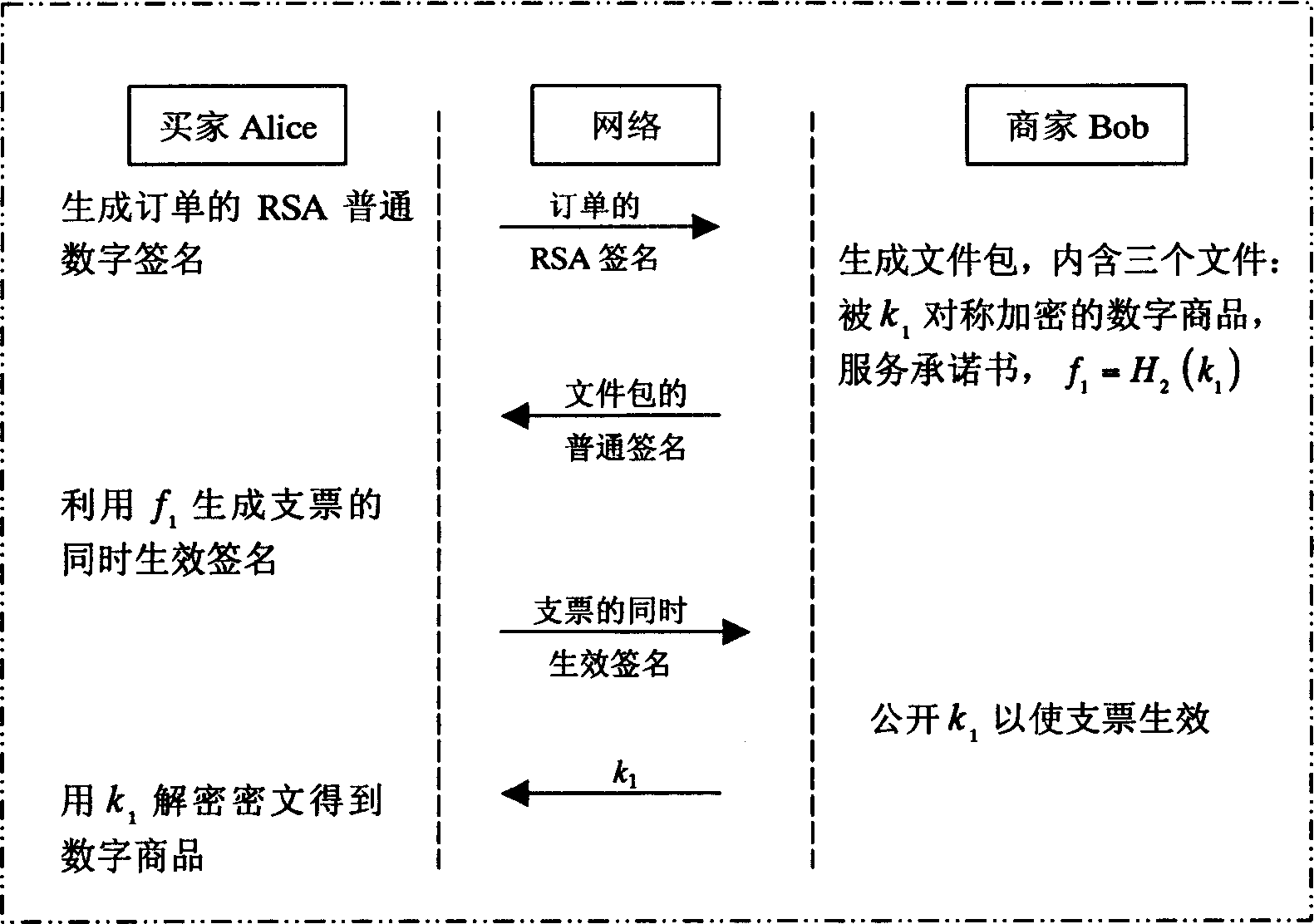
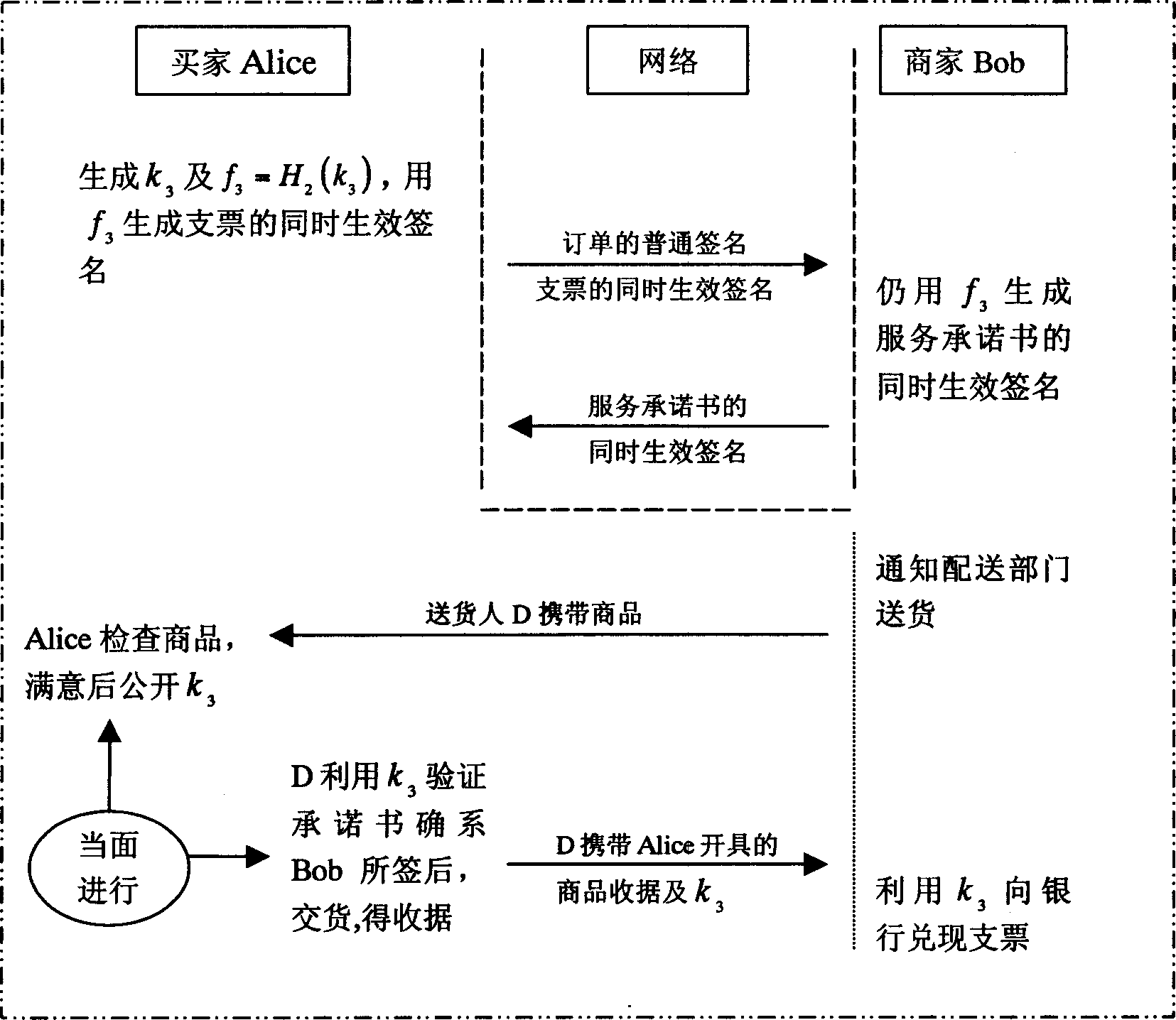
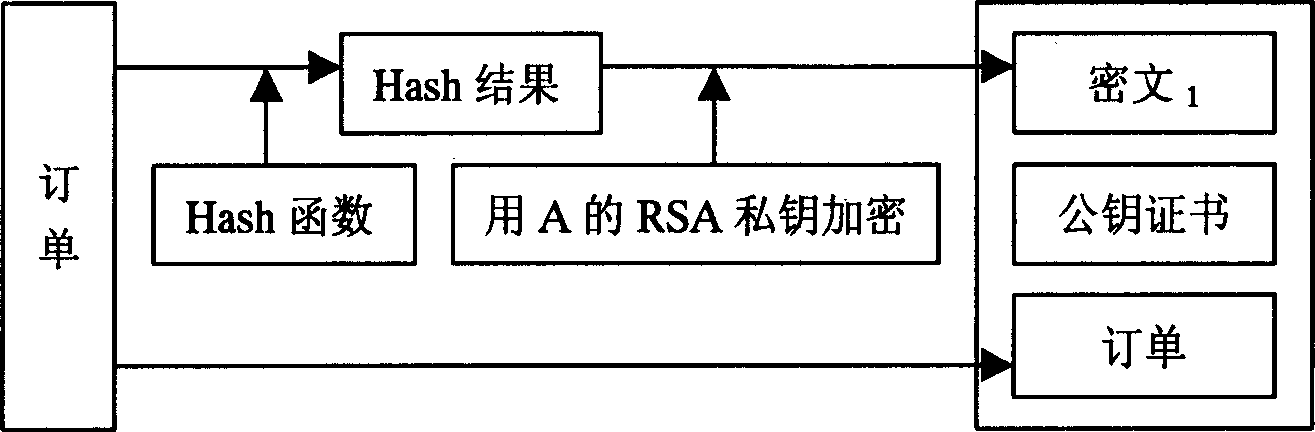
[0046] In order to illustrate the implementation of the present invention more clearly, the principle of concurrently valid signatures is firstly introduced here. The simultaneous effective signature consists of five parts, which are described in detail as follows:
[0047] 1) Establish all parameters including keys
[0048] First choose two large prime numbers p, q, and satisfy q|p-1, g is the group Z p * A q-order element of ;
[0049] Then choose two one-way Hash functions H 1 , H 2 : {0, 1} * → Z q ;
[0050] Then select the private key x∈Z q , public key y=g x mod p;
[0051] Assuming that the party participating in the exchange is Party A, and the other party participating in the exchange is Party B, then Party A will get the private key x A ∈ Z q and public key y A = g x A mod p , And party B will get the priva...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com