Device and method for controlling computer access
A technology for controlling computers and equipment, applied in computer security devices, computing, user identity/authority verification, etc., can solve the problems that administrators cannot effectively manage computers, hinder the maximum performance of computers, and inconvenience administrators to manage, etc., to reduce resources Occupancy rate, low cost, and easy centralized management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
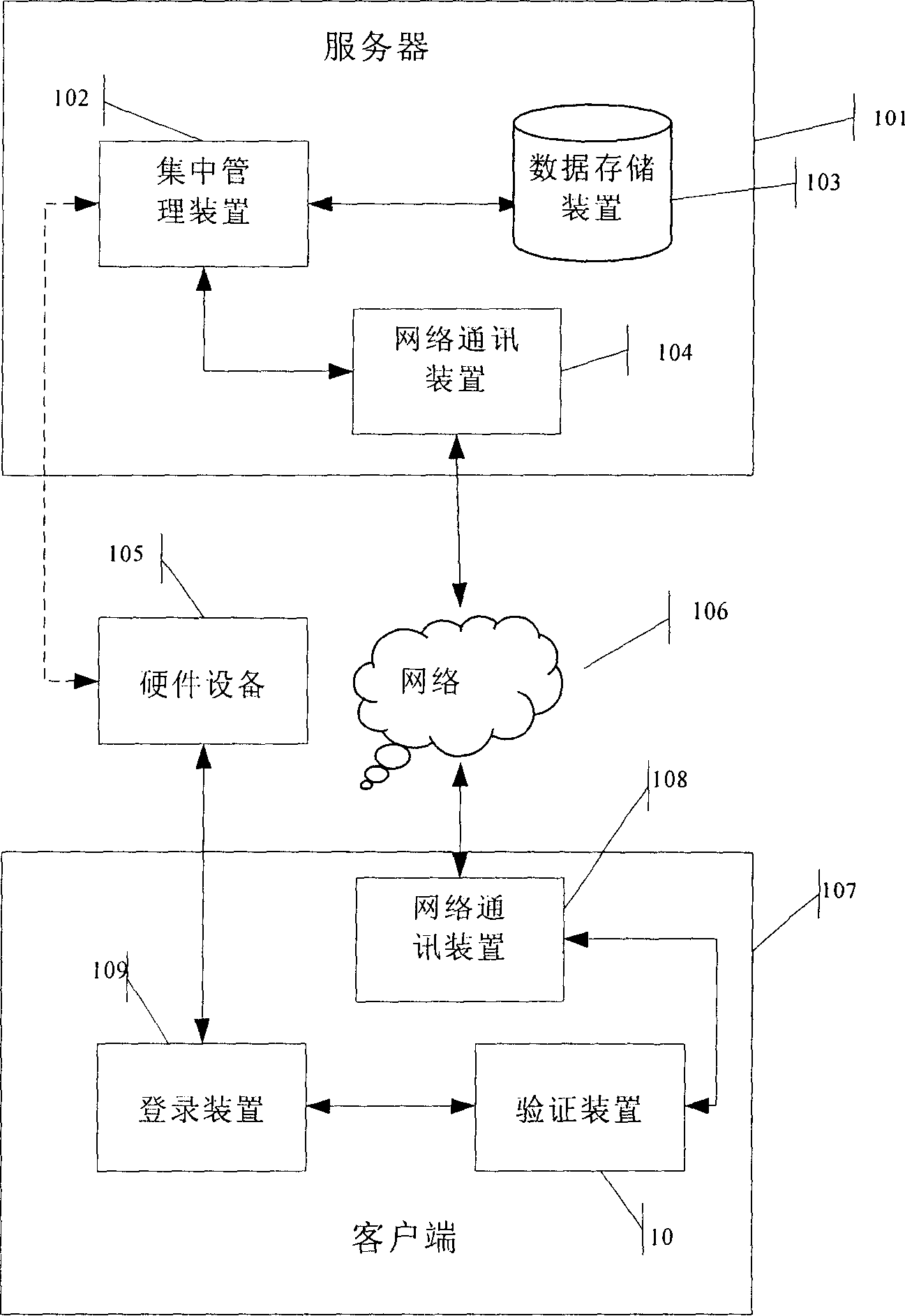
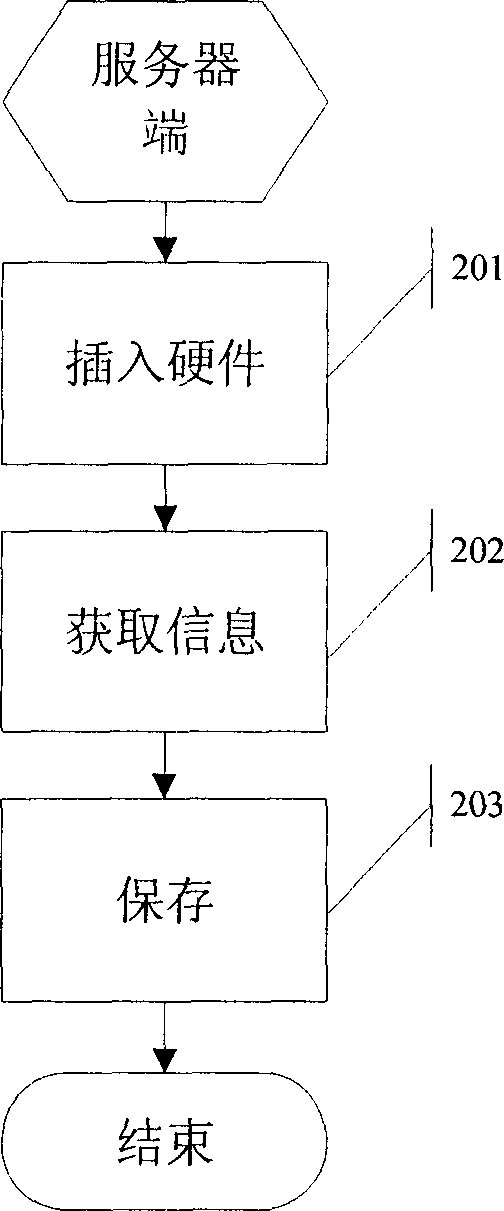
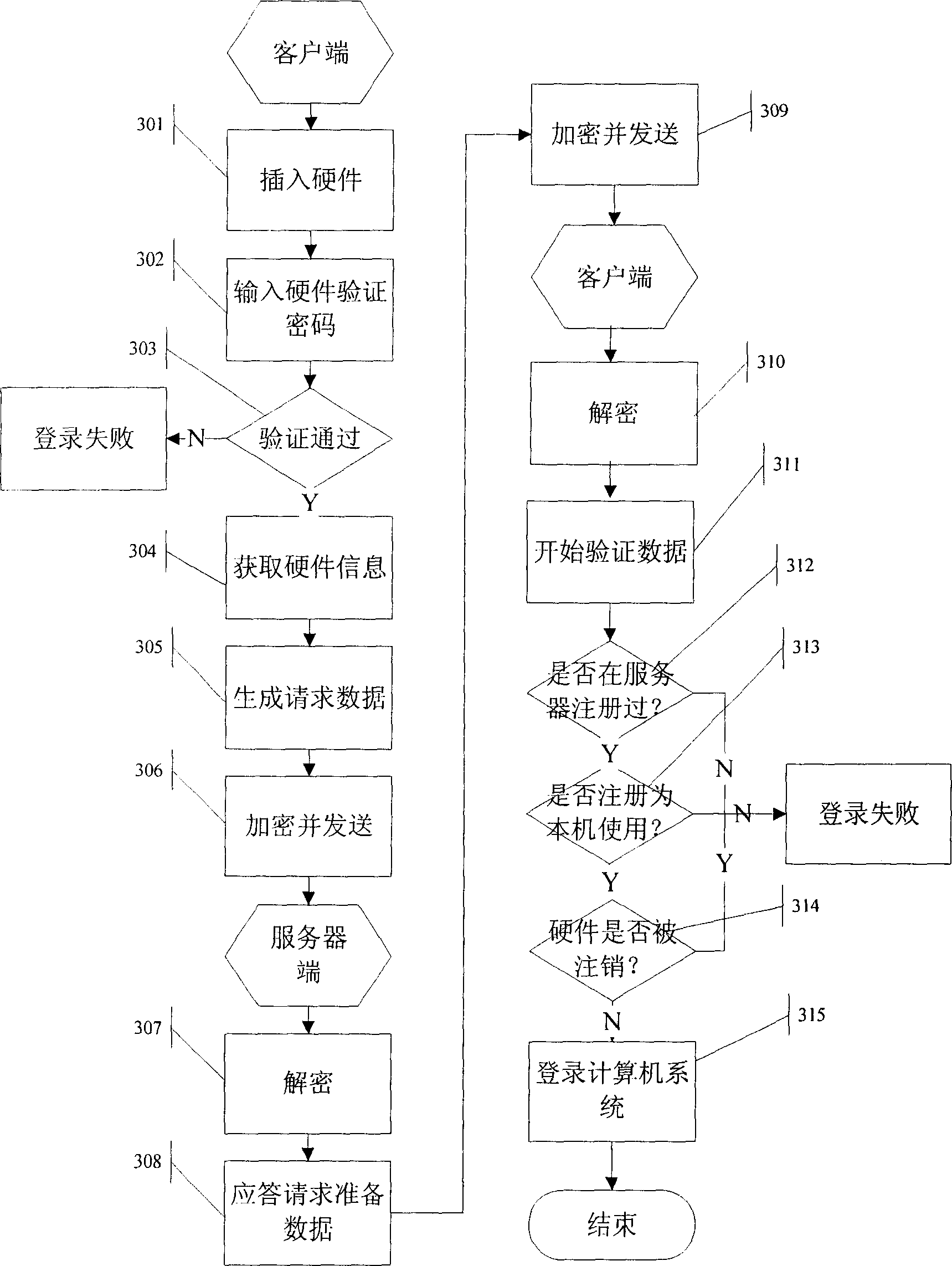
[0078] User A logs in to computer A with hardware device A: he inserts the hardware device A obtained from the administrator into the interface of computer A, computer A asks user A to enter a password, user A enters the password: "456", the computer prompts the user "password error , cannot log in", user A re-enters the password "123", the login device obtains the information of hardware device A and submits it to the verification device of computer A; The request data is submitted to the network communication device of computer A, and the network communication device encrypts the data and sends it to the network communication device on the server side through the network, and the server-side network communication device decrypts the data and submits it to the centralized management device; Read the information of the hardware device A from the storage device and submit the information to the server-side network communication device; the server-side network communication devic...
Embodiment 2
[0080] User B uses hardware device B to log in to computer A: he inserts hardware device B into the interface of computer A, computer A prompts to enter a password, user B enters the password "123", computer A obtains the information of hardware device B, and sends the server to obtain the hardware device For the registration information request of B, the server reads the information of hardware device B from the database according to the request of computer A and feeds it back to computer A. Computer A judges that hardware device B has been registered according to the feedback information of the server, but hardware device B is not registered as Log in to computer A, and computer A prompts that user B is an illegal user and cannot log in.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com