Method, device and system for preventing illegal subscriber log-on
A technology for illegal users and users, applied in transmission systems, digital transmission systems, secure communication devices, etc., and can solve problems such as lack of
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
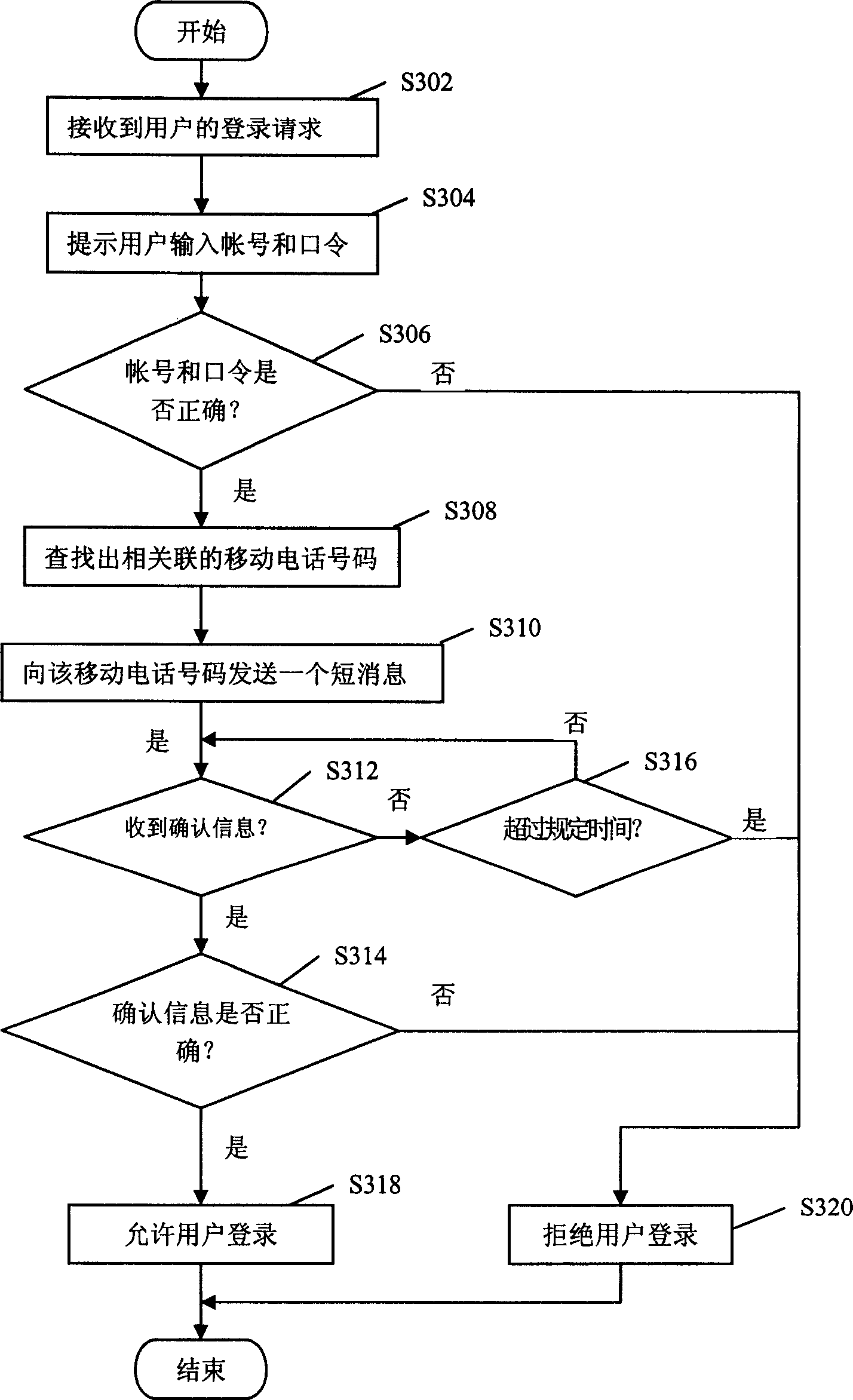
[0028] Next, embodiments of the present invention will be described in detail. It should be noted that the following description should not be used to limit the present invention. On the contrary, according to the inventive concept of the present invention, those skilled in the art can make appropriate changes, and these changes can fall within the scope of the invention defined by the claims.
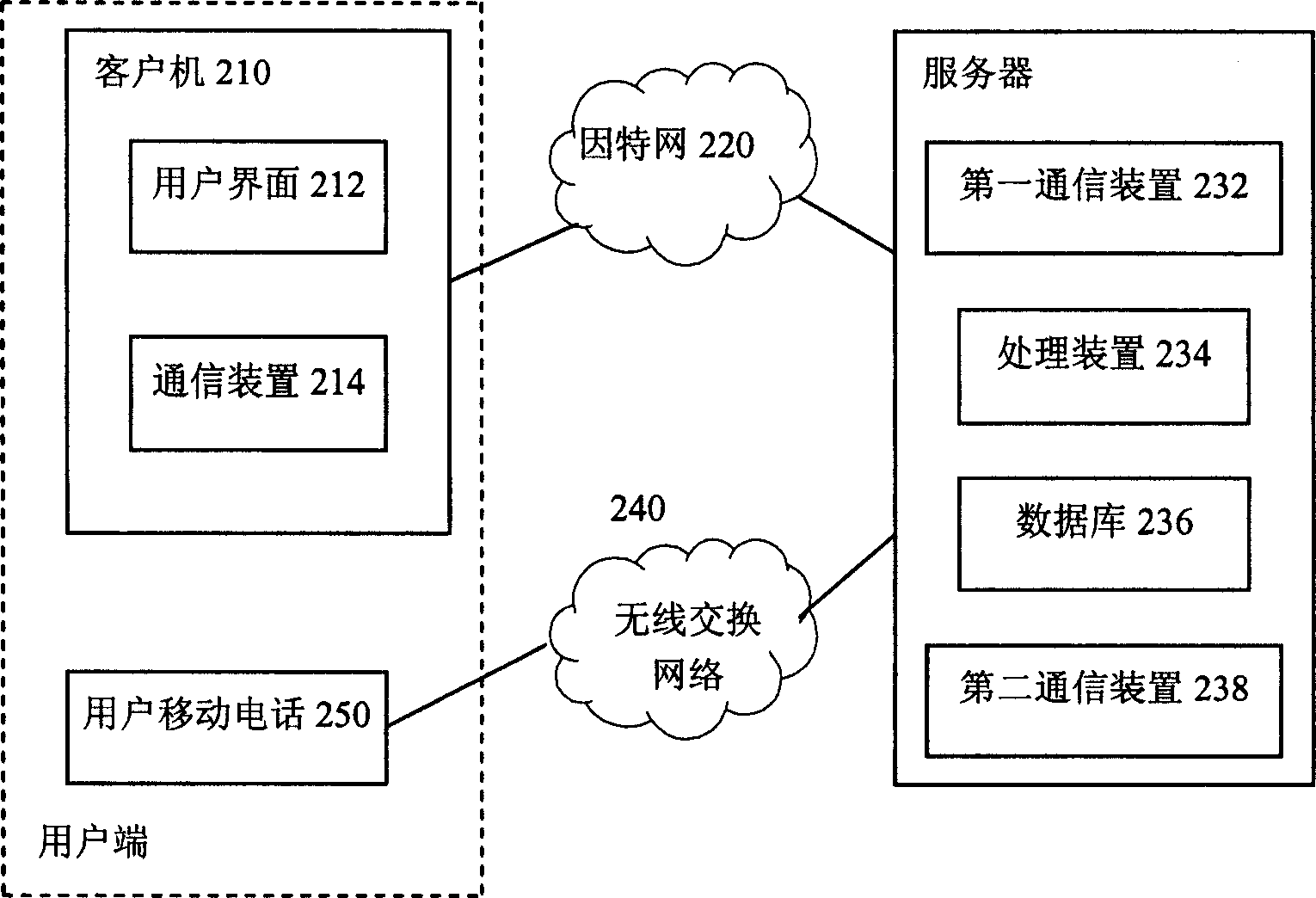
[0029] At the same time, it should be noted that although an online game is taken as an example here, those skilled in the art should understand that the present invention is not limited to the method and system for preventing illegal users from logging into online games. In online applications where passwords and other information verify user identities, the method and system of the present invention can be used to prevent illegal users from invading.
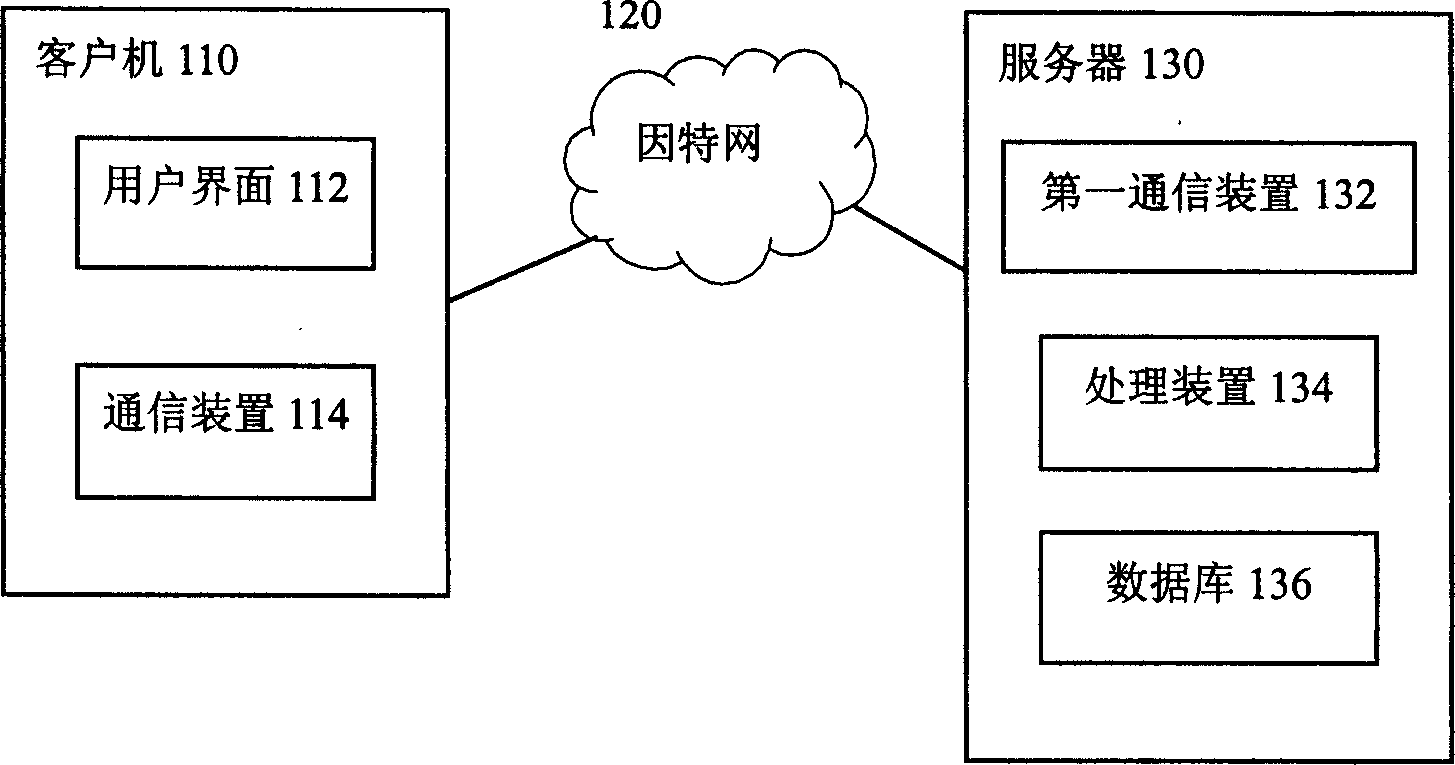
[0030] In order to describe the present invention more clearly, a system for implementing online games in the prior art is firstly d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com