Voice-print authentication device and method of authenticating people presence
A technology for authentication equipment and authentication methods, applied in speech analysis, speech recognition, instruments, etc., to achieve the effect of low price, high equipment penetration rate, and improved security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The above and other objects, features and advantages of the present invention will become apparent from the following description taken in conjunction with the accompanying drawings of the present invention.
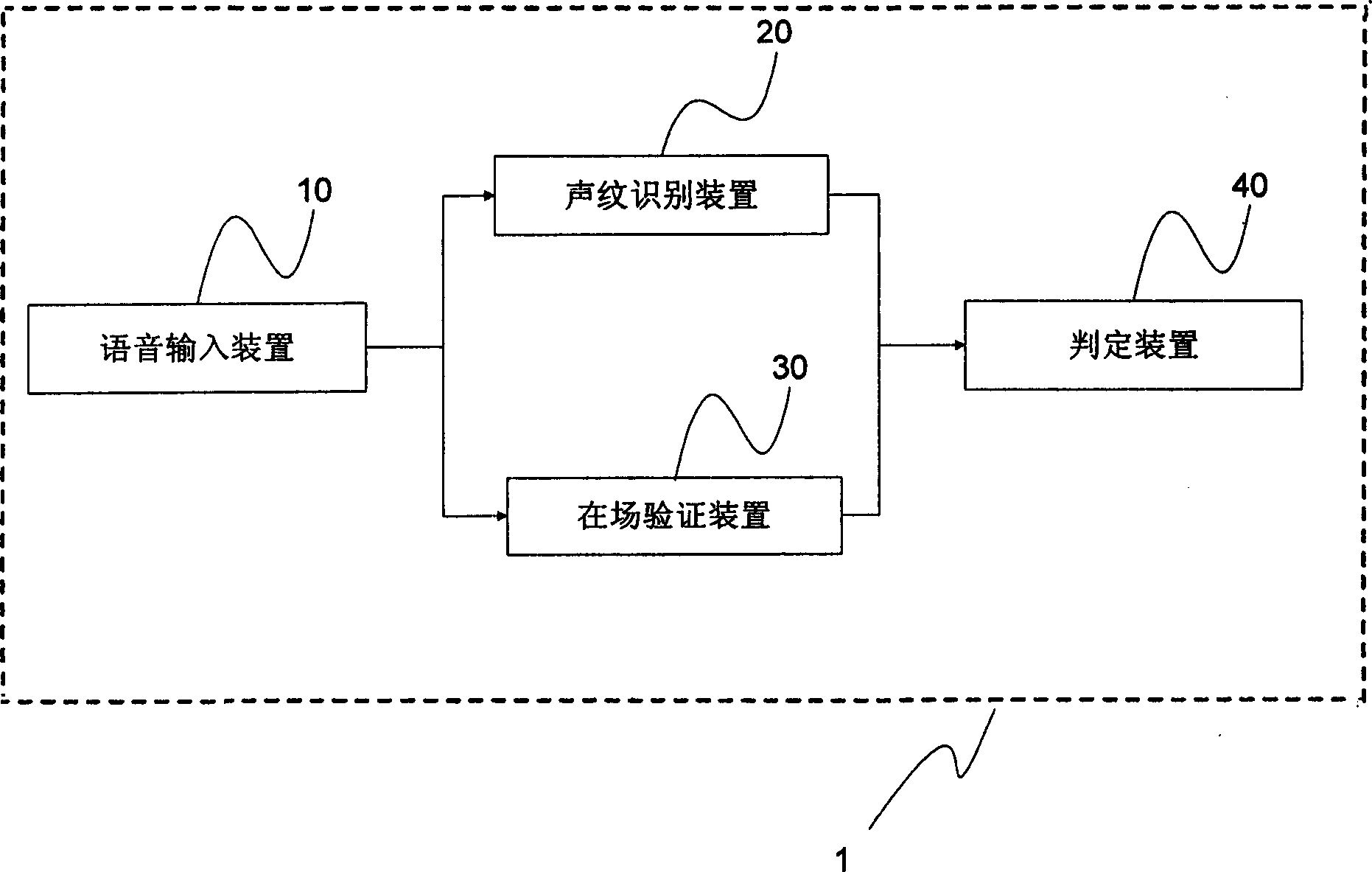
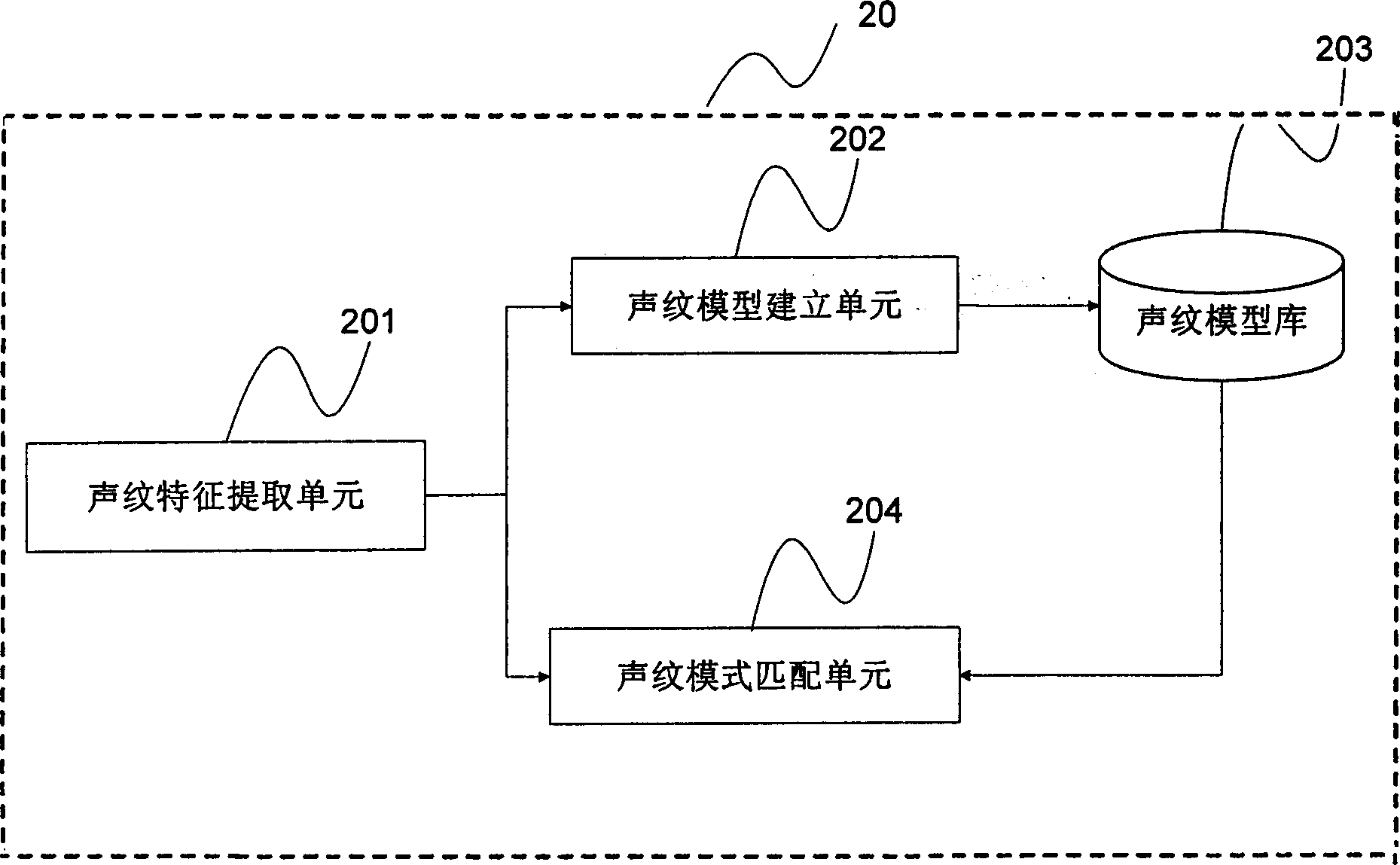
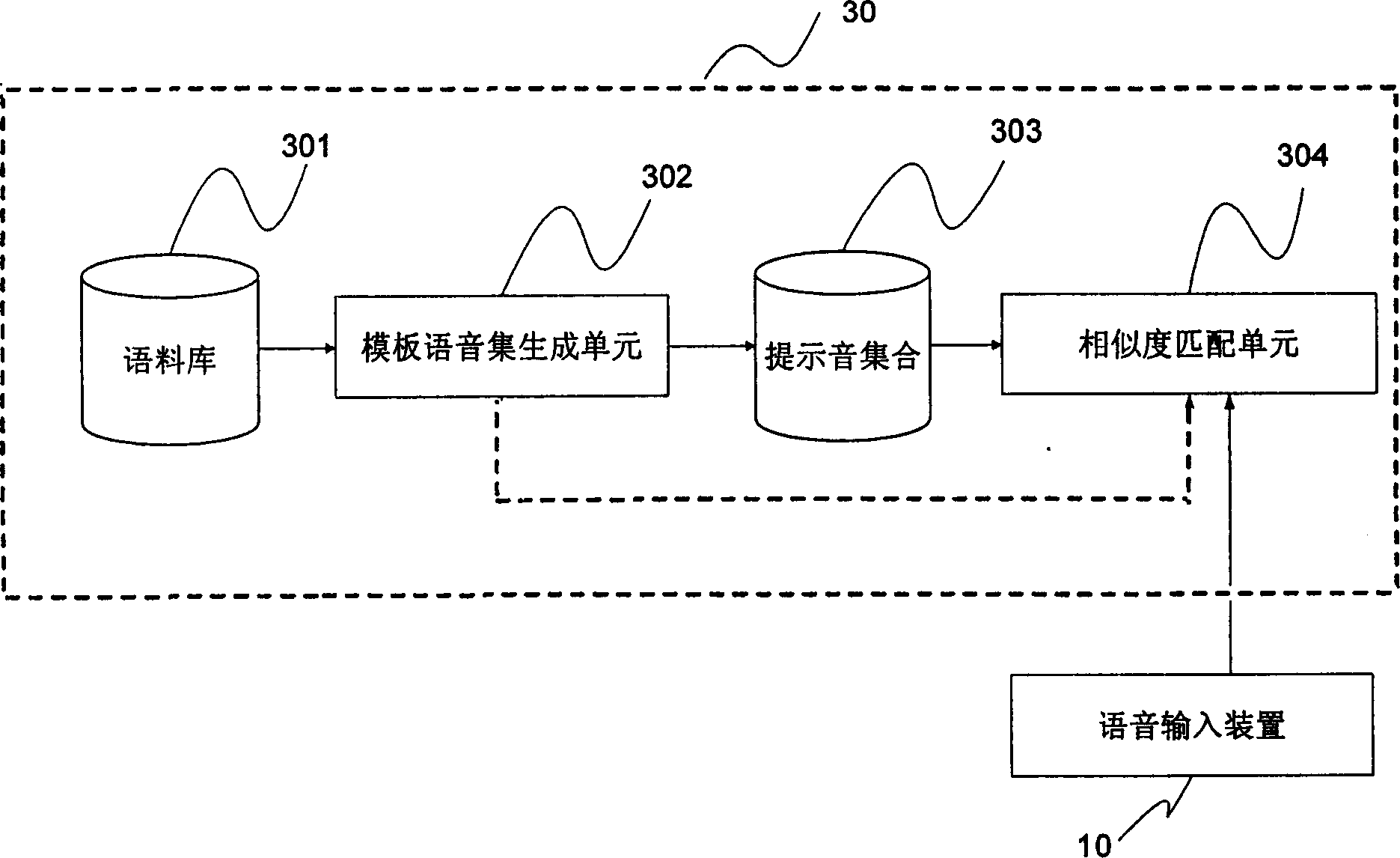
[0019] Voice is the most basic and convenient way of communication and transaction for human beings. The voice information generated by users using the authentication system can contain both user identity information and user personal wishes information. The present invention makes full use of the advantages of the voiceprint authentication technology, especially the text-independent voiceprint authentication technology, and at the same time combines the method of confirming the pronunciation status of a real person present to improve the overall security of the authentication equipment, and confirm the authenticity through the interactive authentication process. The pronunciation is in a state of clear consciousness.
[0020] figure 1 is a schematic diagram of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com