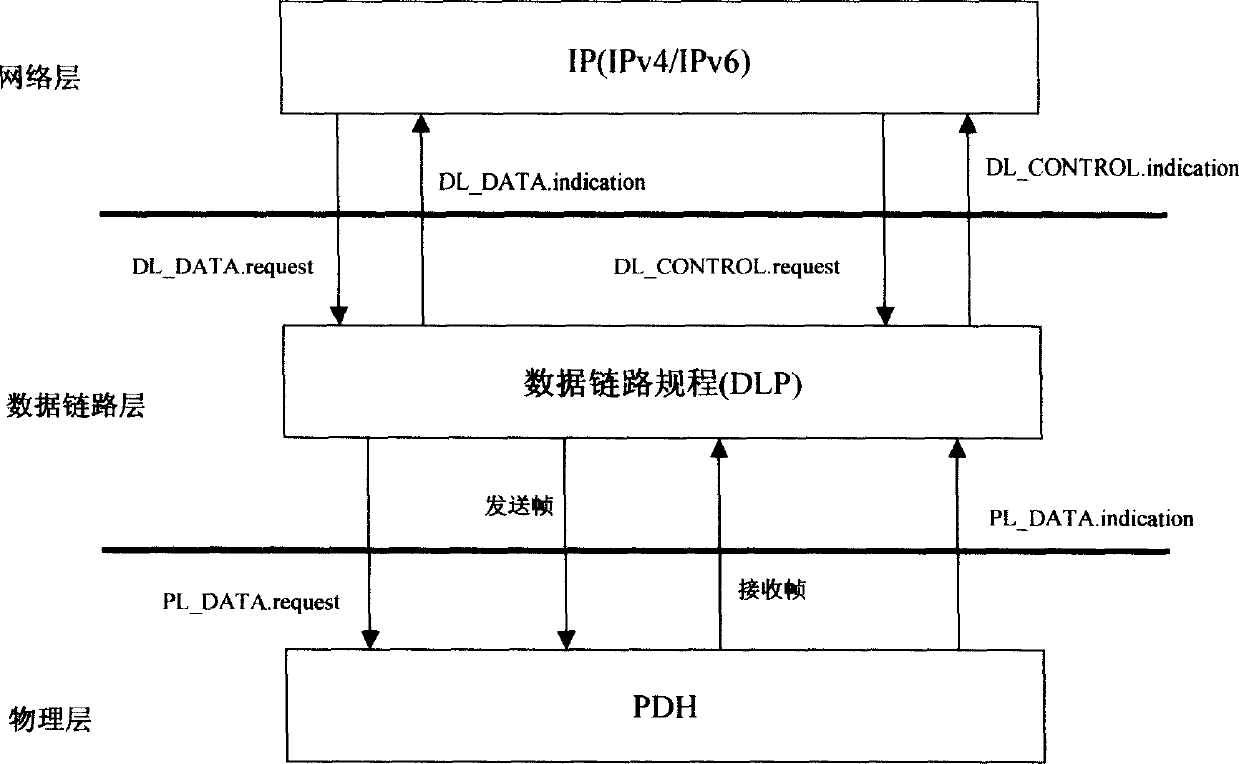
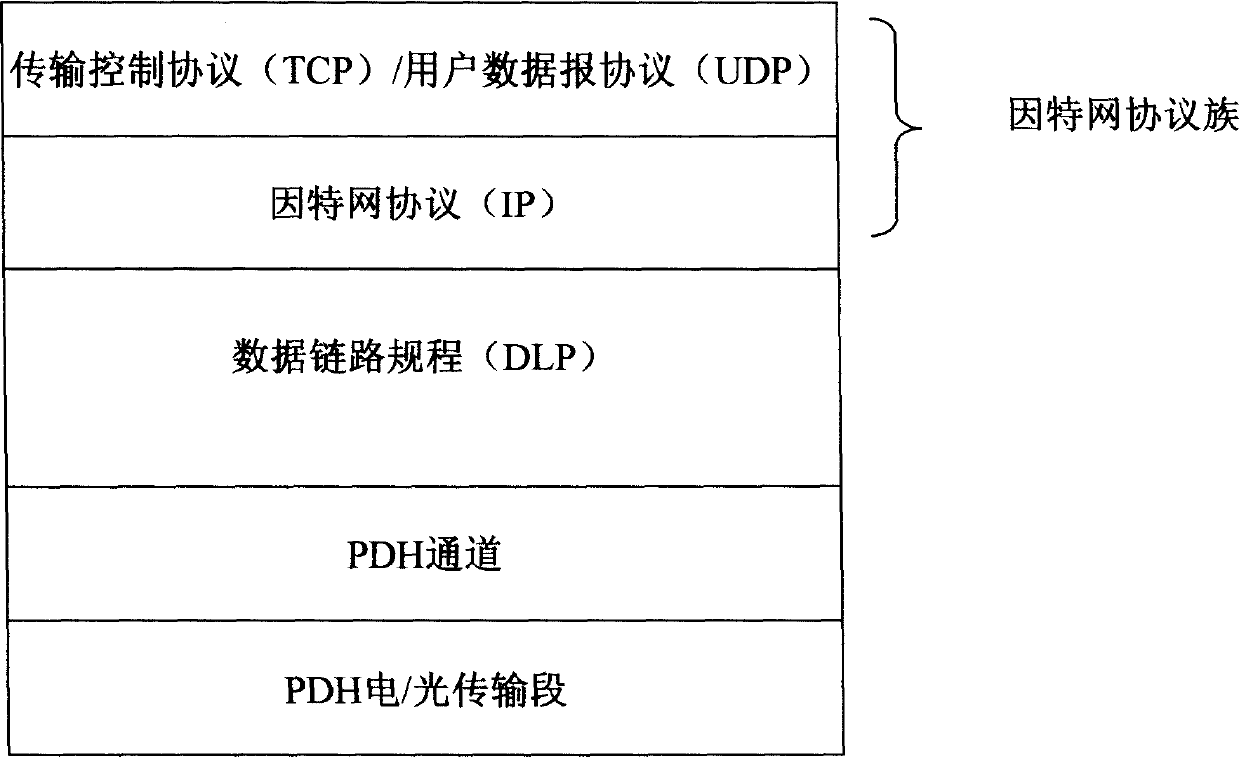
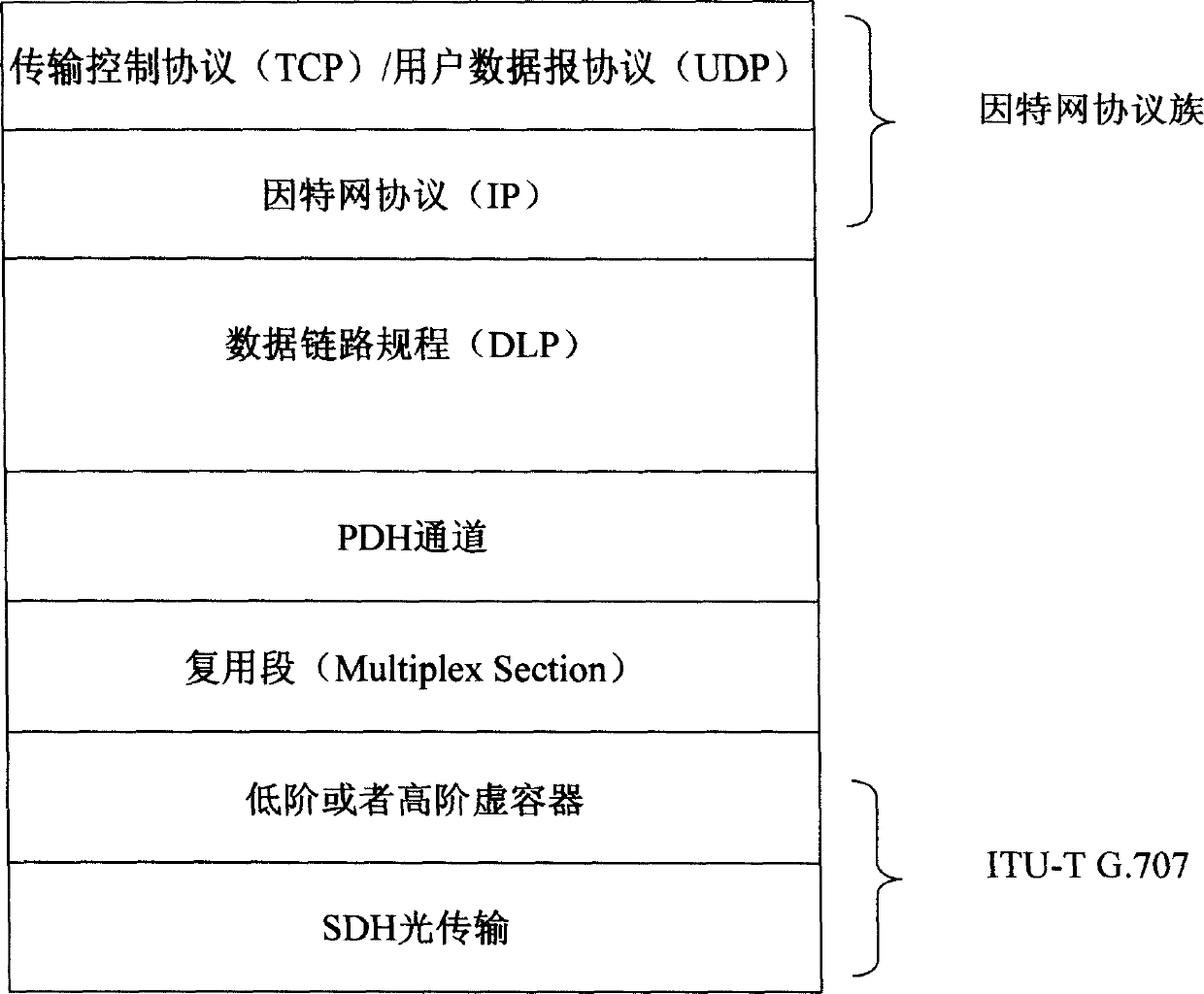
[0009] (1) The above three adaptation methods are all point-to-point connection solutions. The main
advantage is to solve the problem of point-to-point transmission of IP packets, but these adaptation methods are very complicated and inefficient. When a node maps an IP packet through these three methods, each node must perform a series of complex
processing on each IP packet. Specifically, every time an IP packet passes through a node, each IP packet must be processed once. A series of
processing from the first layer to the third layer, and then from the third layer to the first layer, that is, to extract the
data link layer protocol frame (respectively PPP+HDLC or LAPS or GFP frame) from the physical frame (PDH frame)
signal, and then Extract the IP packet from the
data link layer protocol frame (PPP+HDLC or LAPS or GFP frame), and then forward each IP packet through the
routing protocol according to the destination
IP address in the IP header in the IP packet, that is, forward it to Different ports; when forwarding, first encapsulate the three-layer IP packet into the second-layer
data link layer protocol (that is, the
data link layer protocol of the above three encapsulation methods, respectively PPP+HDLC, LAPS or GFP), and then Then encapsulate the data
link layer protocol frame of the IP packet into the
payload of the first layer
physical layer, that is, the PDH frame, that is, encapsulate the PPP+HDLC or LAPS or GFP frame into the
payload domain of the PDH frame. The
processing is not only very complicated but also inefficient, especially for the core nodes, the amount of data processed is very large, which has become an important factor that seriously affects the quality of IP networks
[0010] (2) There is no network protection switching function. Since the IP network uses the
routing protocol to forward the IP packet according to the destination
IP address in the IP packet, when the physical link fails, the IP network using the above three adaptation methods The network must recalculate the
route. On the one hand, this may lead to
packet loss. On the other hand, if IP is used to carry important services such as real-time services, since the
switching time of the IP network is actually within a few seconds, it is difficult to meet the requirements of real-time services.
[0011] (3) Since the IP network uses two types of routing protocols, namely, the
interior gateway protocol and the exterior gateway protocol to realize the routing selection of IP packets, this method has no
traffic engineering capability, which may cause even if there are multiple connection links between two nodes. However, the IP network may forward all IP packets to one link and transmit them through one link, causing congestion on this link, resulting in
packet loss, while the other link is in an idle state.
[0012] (4) Since the above three adaptation methods do not perform any service classification on data services, everyone is the same and has the same priority, resulting in no
quality of service guarantee for this IP network
[0013] (5) Since these three adaptation methods use point-to-point connection processing, each data packet must be processed at each node. If the network is an all-optical network, a series of optical-electrical-optical Conversion processing cannot realize all-optical switching, especially for dense
wavelength division
multiplexing systems using SDH frame structure,
optical wavelength switching cannot be realized, and direct switching of virtual containers or synchronous
transfer mode granular PDH circuits cannot be realized
[0014] (6) For the first and second adaptation methods that adopt PPP+HDLC and LAPS, since HDLC frames and LAPS frames use specific bytes (0X7E) to realize frame delimitation, IP packets need to be transparently processed. This method has two flaws, one is
network security issues, if those malicious people set all the
payload information to the specific two bytes (0X7D, 0X7E), then this will double the traffic of the network , if a joint
attack is adopted, it may lead to
network congestion; in addition, since these two adaptation methods have no error correction function, if the frame delimitation
byte is wrong (theoretical
probability of error is 1 / 2 8 =1 / 256=0.00390625, which is about 3.9 per thousand), it may cause
packet loss[0015] (7) The IP network using the above three adaptation methods has no security at all
[0016] (8) The above three IP and PDH adaptation methods can be used for IPv4 and IPv6, that is, the adaptation of IPv4 and PDH and the adaptation of IPv6 and PDH can be realized, but because IPv4 and IPv6 are incompatible, and because of the above All three adaptation methods need to process each IP packet at the
network layer. Using the above three adaptation methods makes IPv4 and IPv6 networks incompatible
[0017] (9) In the network using the above
adaptation method, the traditional voice service is separated from the IP
network service, but now it is generally believed that the unified
public network will adopt
packet switching technology in the future. , so that the integration of packetized voice services and IP networks is of no help
 Login to View More
Login to View More  Login to View More
Login to View More