Method for selecting encrypted algorithm in radio communication system
A wireless communication system and encryption algorithm technology, which is applied in the field of selecting encryption algorithms to achieve the effect of ensuring interconnectivity, reasonable and simple logic, and high efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
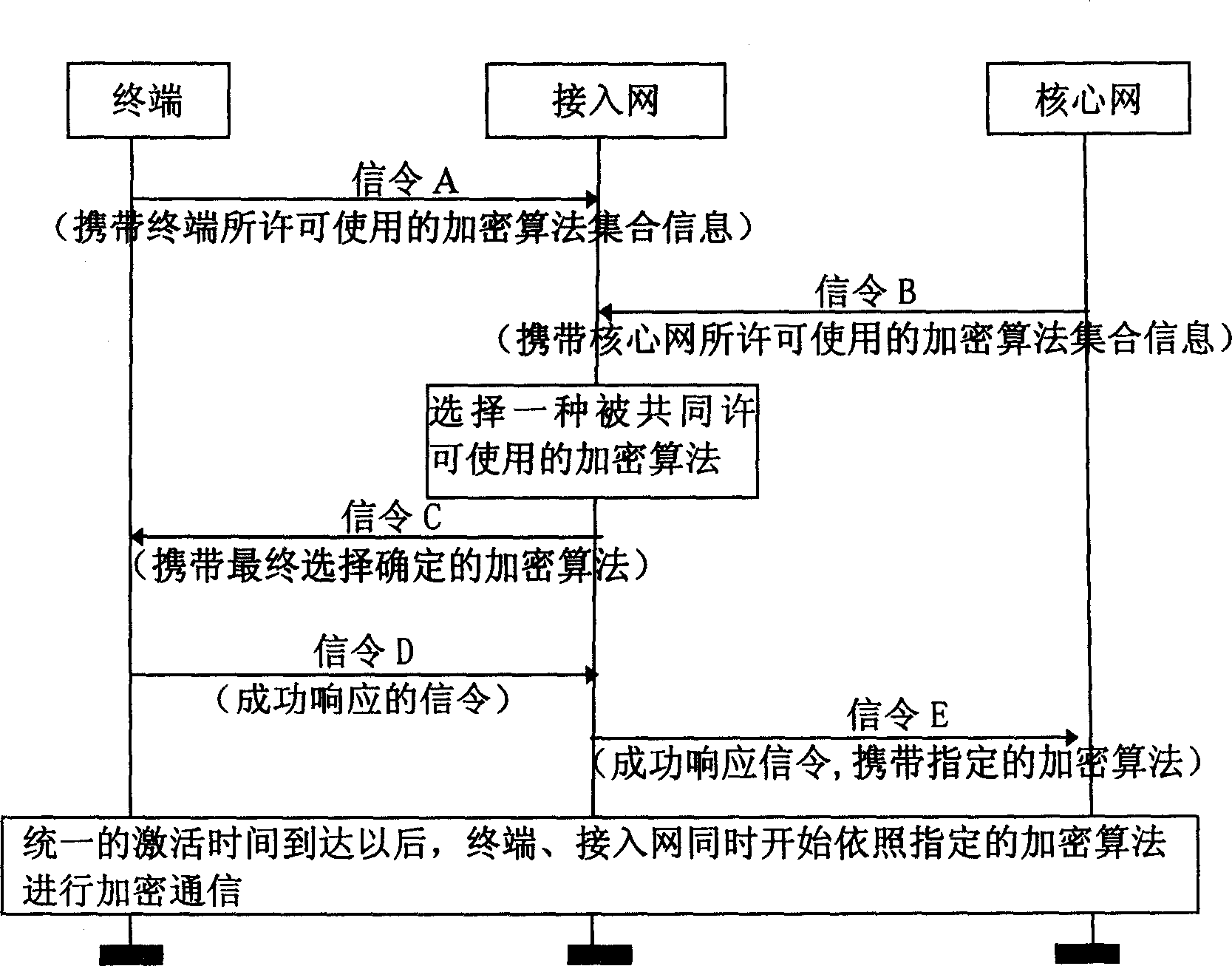
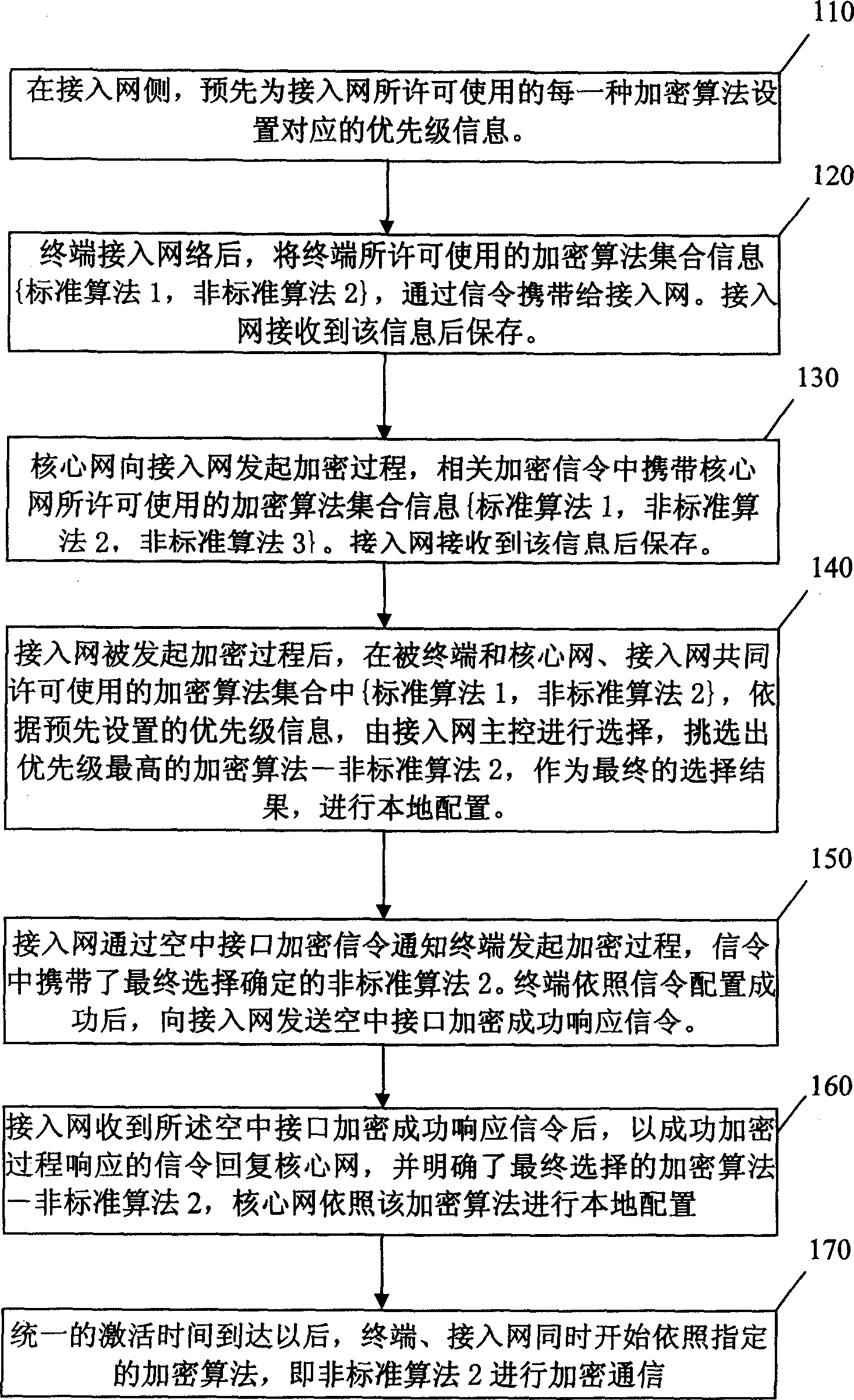
[0041] When the method of the present invention is applied in a wireless communication system, multiple encryption methods must be jointly approved by the terminal, the core network, and the access network; otherwise, the process of selecting an encryption algorithm will not be performed. Secondly, the terminal has the ability to report the set information of its licensed encryption algorithm to the access network, and the core network has the ability to initiate the encryption process to ensure that the encryption process can be processed normally.
[0042] Below in conjunction with accompanying drawing, the implementation of technical scheme is described in further detail:
[0043]This embodiment provides a method for selecting an encryption algorithm based on the encryption priority of the wireless access network. The encryption priority principle of the access network is used to select the encryption algorithm.
[0044] On the access network side, it is necessary to confi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com