Method for protecting access security of IP multimedia subsystem based on TLS
A technology for multimedia subsystems and security protection, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve the problems that user terminals do not support the use of certificates, cannot authenticate UE identities, etc., and overcome the problem of weak two-way authentication. simple effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
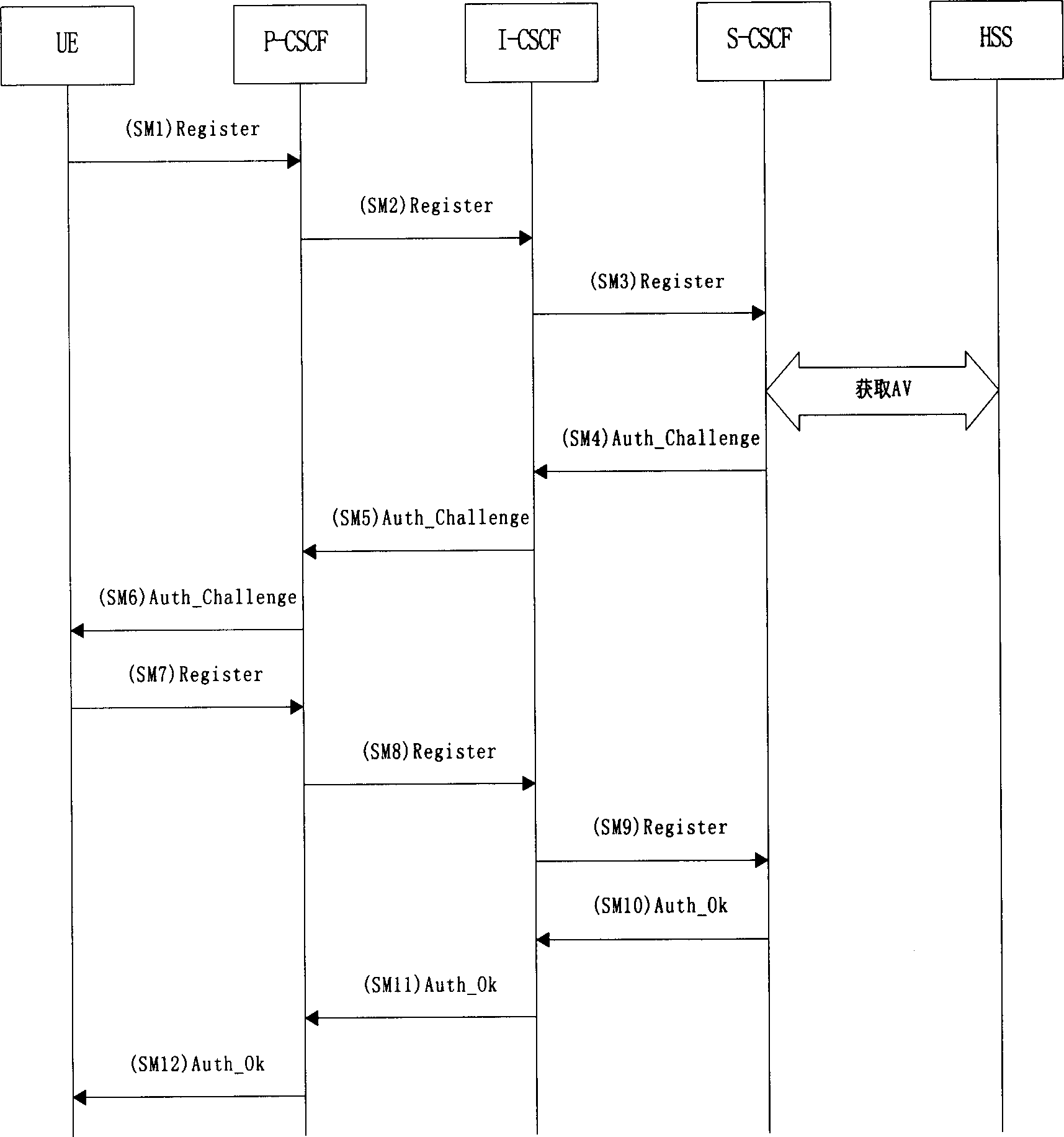
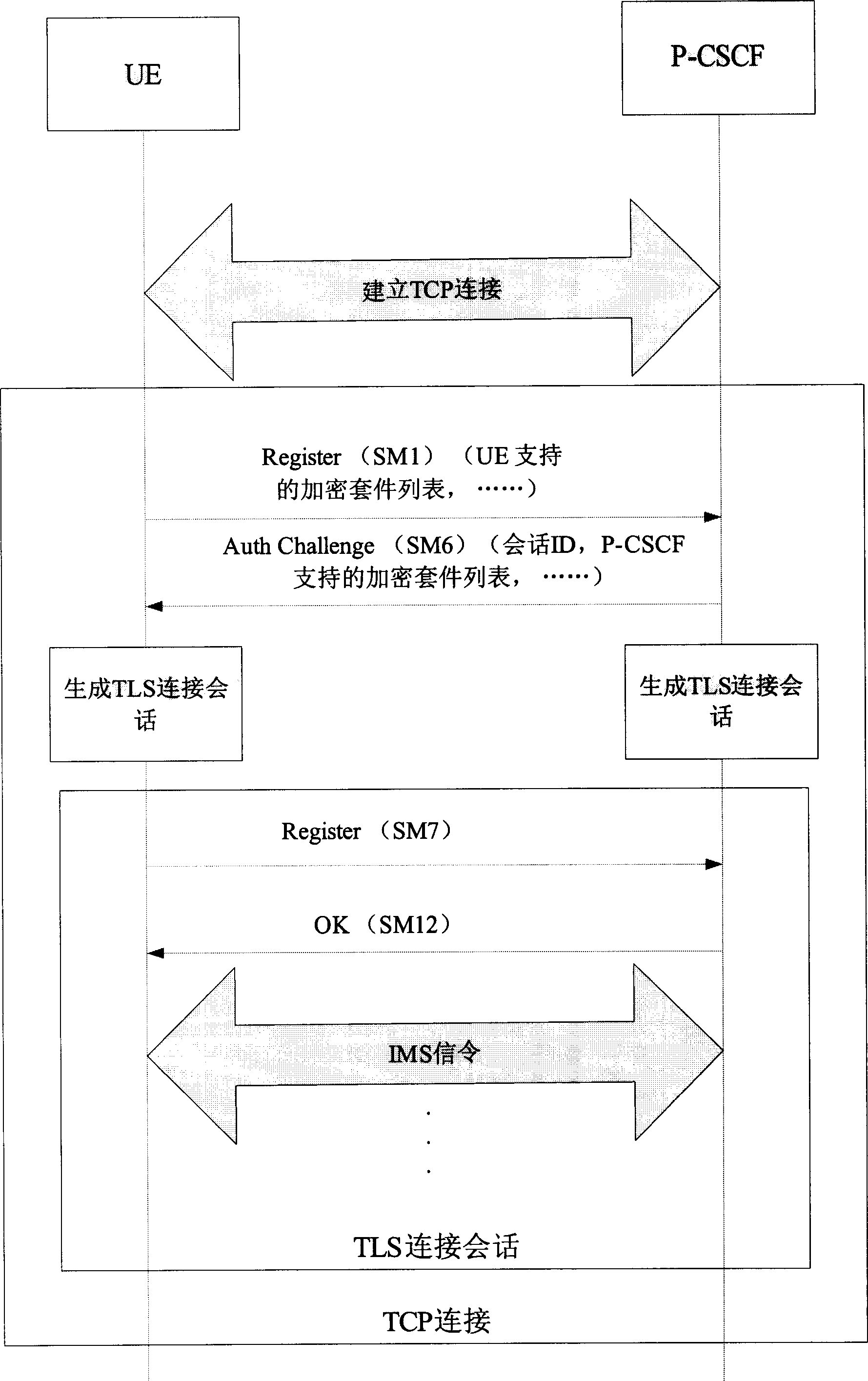
[0036] This embodiment takes figure 2 As an example, the method for protecting IMS access security by using the TLS / IMS AKA protocol in the present invention is described. In this embodiment, both the UE and the P-CSCF support the TLS / IMS AKA security mechanism. The cipher suites supported by the UE include TLS_RSA_WITH_IDEA_CBC_SHA, TLS_RSA_WITH_3DES_EDE_CBC_SHA, and TLS_RSA_WITH_DES_CBC_SHA. The cipher suites supported by the P-CSCF are TLS_RSA_WITH_3DES_EDE_CBC_SHA and TLS_RSA_ITH. The priority of the UE, the UE's IMS access process flow is as follows:
[0037] 1. The UE establishes a TCP connection with the P-CSCF.
[0038] 2. The UE sends an initial registration message (Register) SM1 to the P-CSCF, which includes the user's IMPI and IMPU, and the message also includes a list of cipher suites supported by the UE {TLS_RSA_WITH_IDEA_CBC_SHA, TLS_RSA_WITH_3DES_EDE_CBC_SHA, TLS_RSA_WITH_DES_CBC_SHA}. After receiving the registration message sent by the UE, the P-CSCF choos...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com