A mobile proxy safeguarding method similar to biological self-protection
A mobile agent, security protection technology, applied in the direction of security communication devices, digital transmission systems, electrical components, etc., can solve problems such as difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
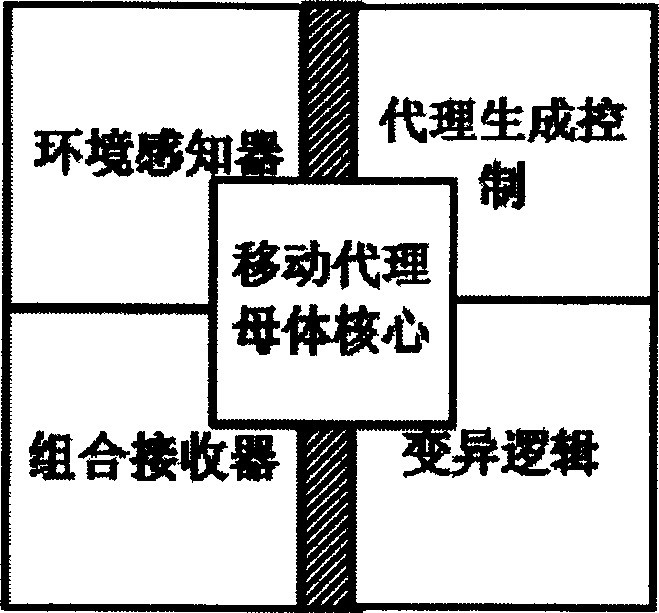
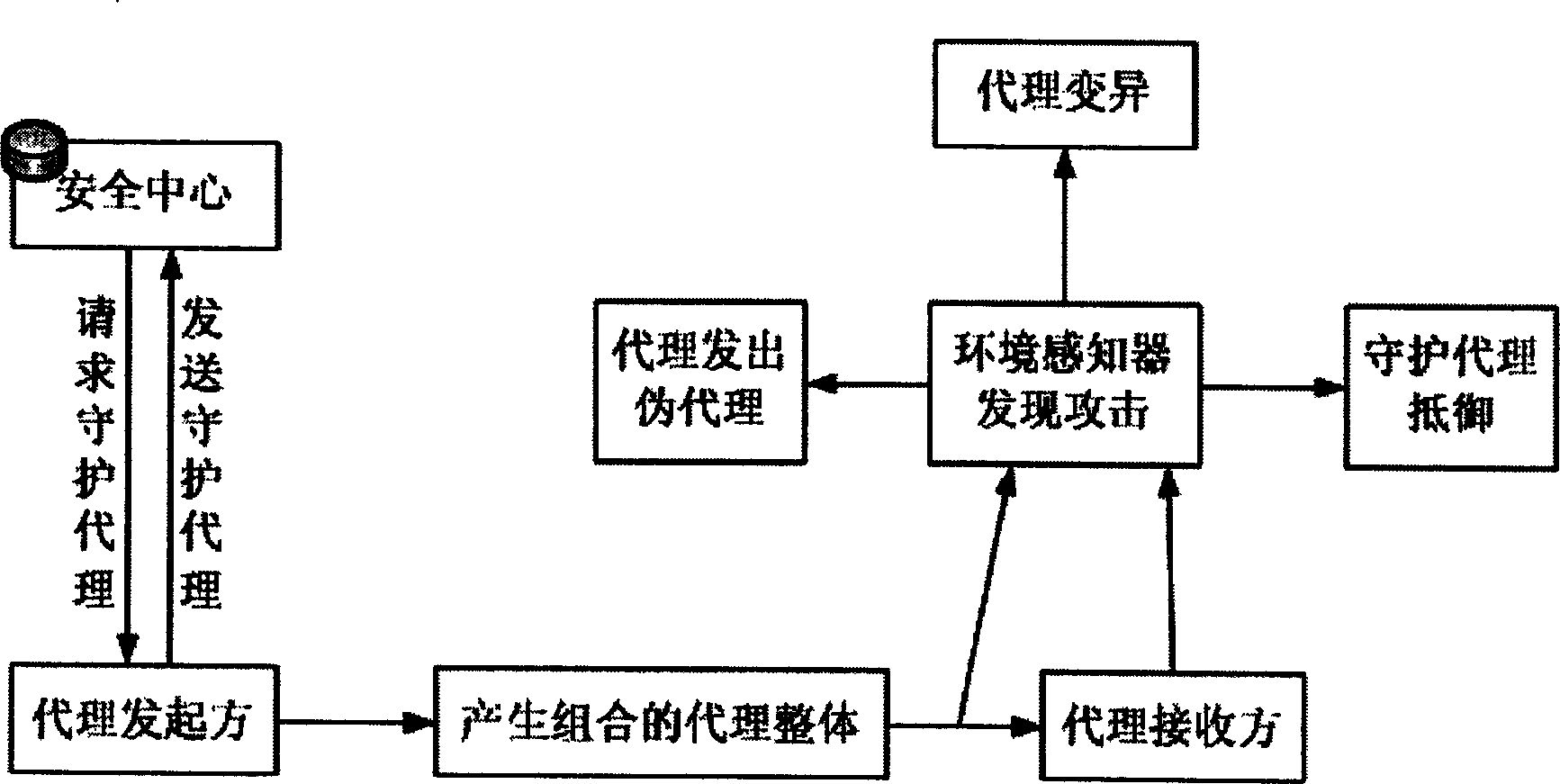
Image
Examples
specific Embodiment approach
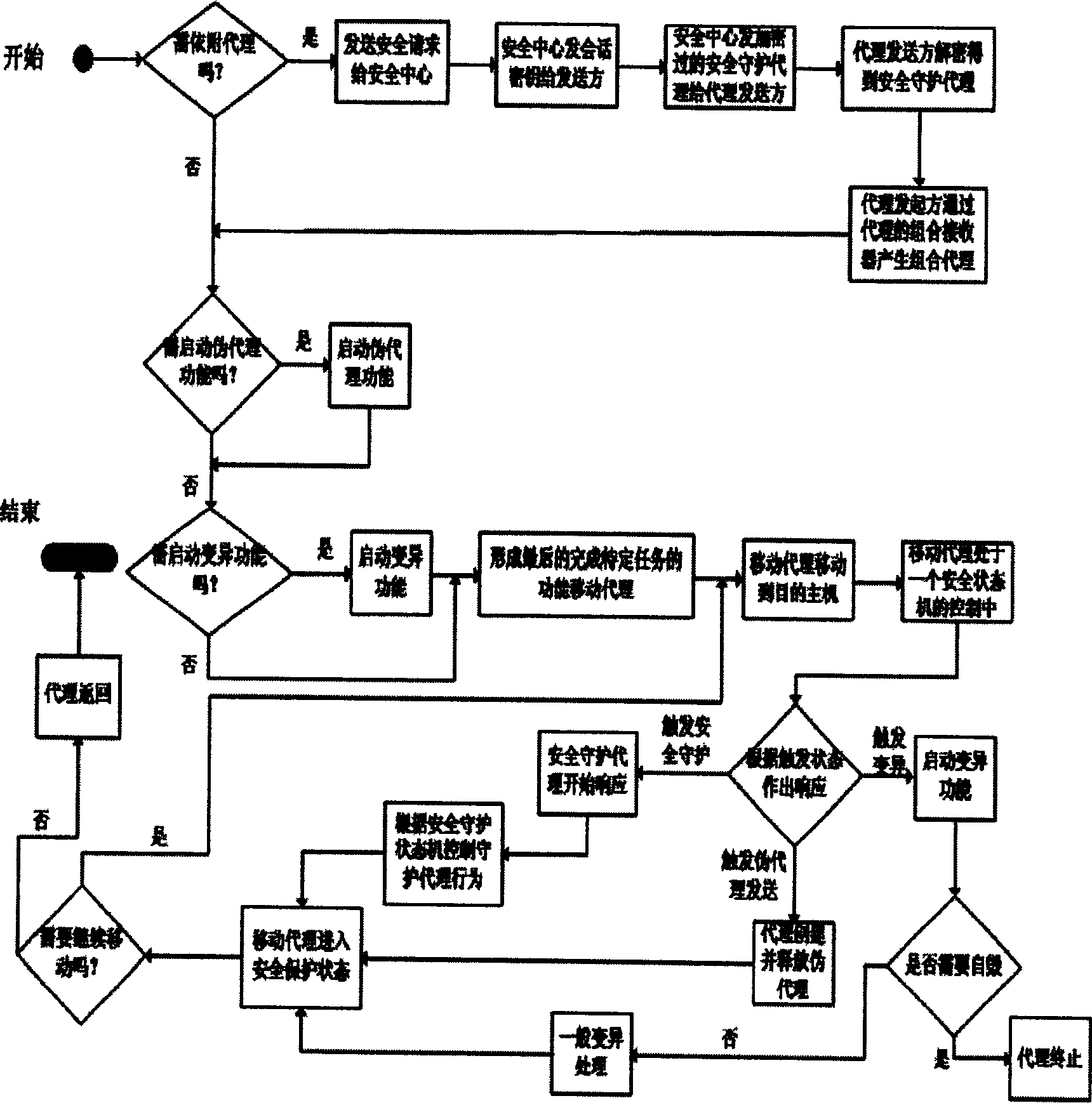
[0104] Then its specific implementation method is:
[0105] (1) The agent initiator creates a mobile agent A
[0106] Since it is assumed that the daemon agent function is enabled, proceed with the following steps;
[0107] (2) The proxy initiator (set as A) sends a request to the security center (set as B)
[0108] Step 1: A initializes the request according to the parameters;
[0109] Assume that the parameters here include security level=1 (initial level), security function=anti-data tampering;
[0110] Step 2: A signs and encrypts the request;
[0111] Can use RSA algorithm to sign and encrypt;
[0112] Step 3: A sends the request to B, for example, using the TCP / IP-based Socket method;
[0113](3) B decrypts the request and verifies the signature of the sender. If it is determined that the verification is from A, then B sends the session key (indicated by k) to A, and d is encrypted, and the encryption key is A's public key;
[0114] (4) B uses d to encrypt the requ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com