Use of isogenies for design of cryptosystems
A computer and decryption key technology, which is applied in the field of cryptography and can solve problems such as the security of public key encryption systems.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The following discussion assumes that the reader is already familiar with cryptography. For a basic introduction to cryptography, readers are invited to read "Handbook of Applied Cryptography" written by A. Menezes, P. van Oorschot and S. Vanstone published by CRC Press, the fifth printing ( August 2001) original text.
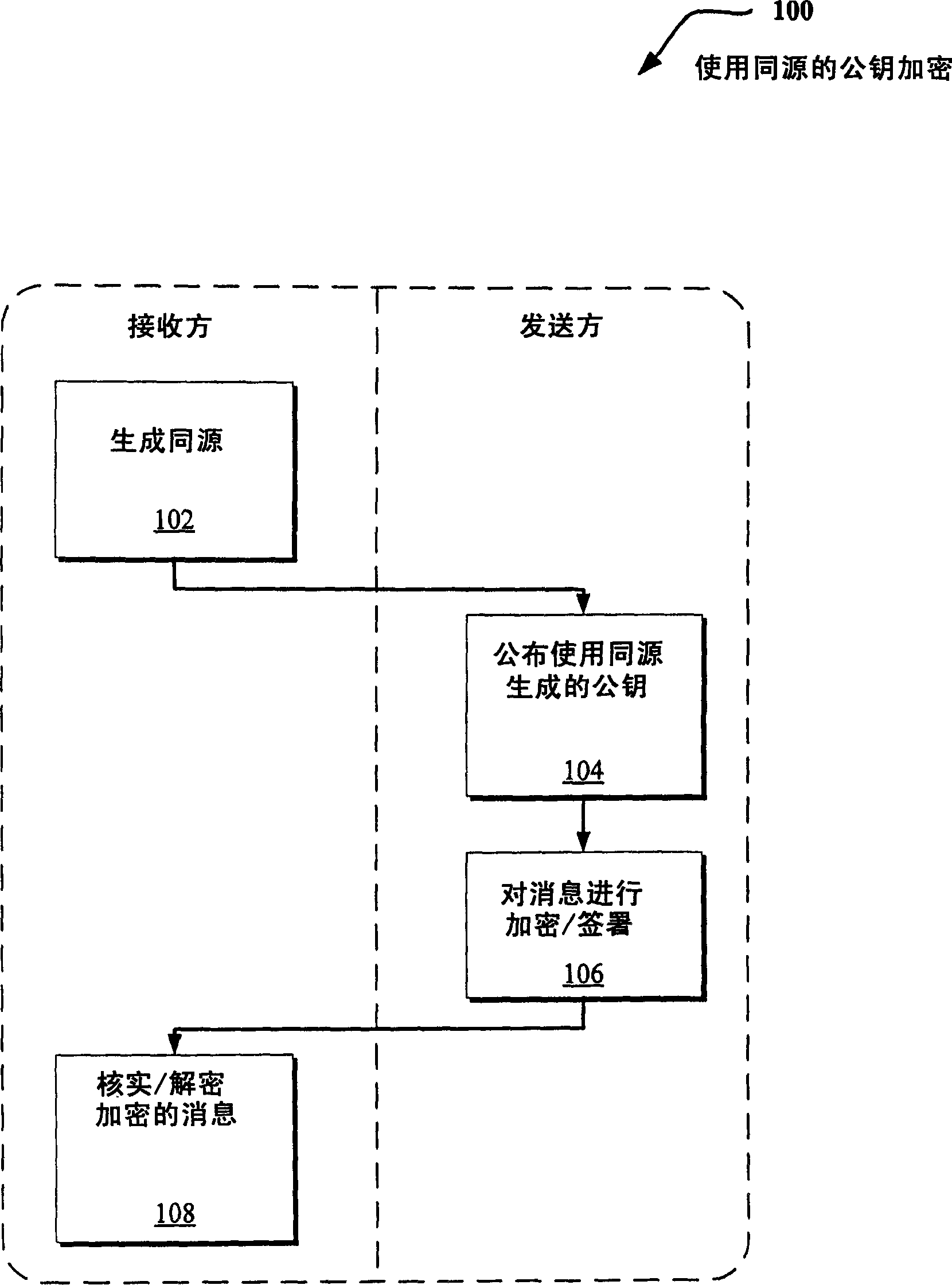
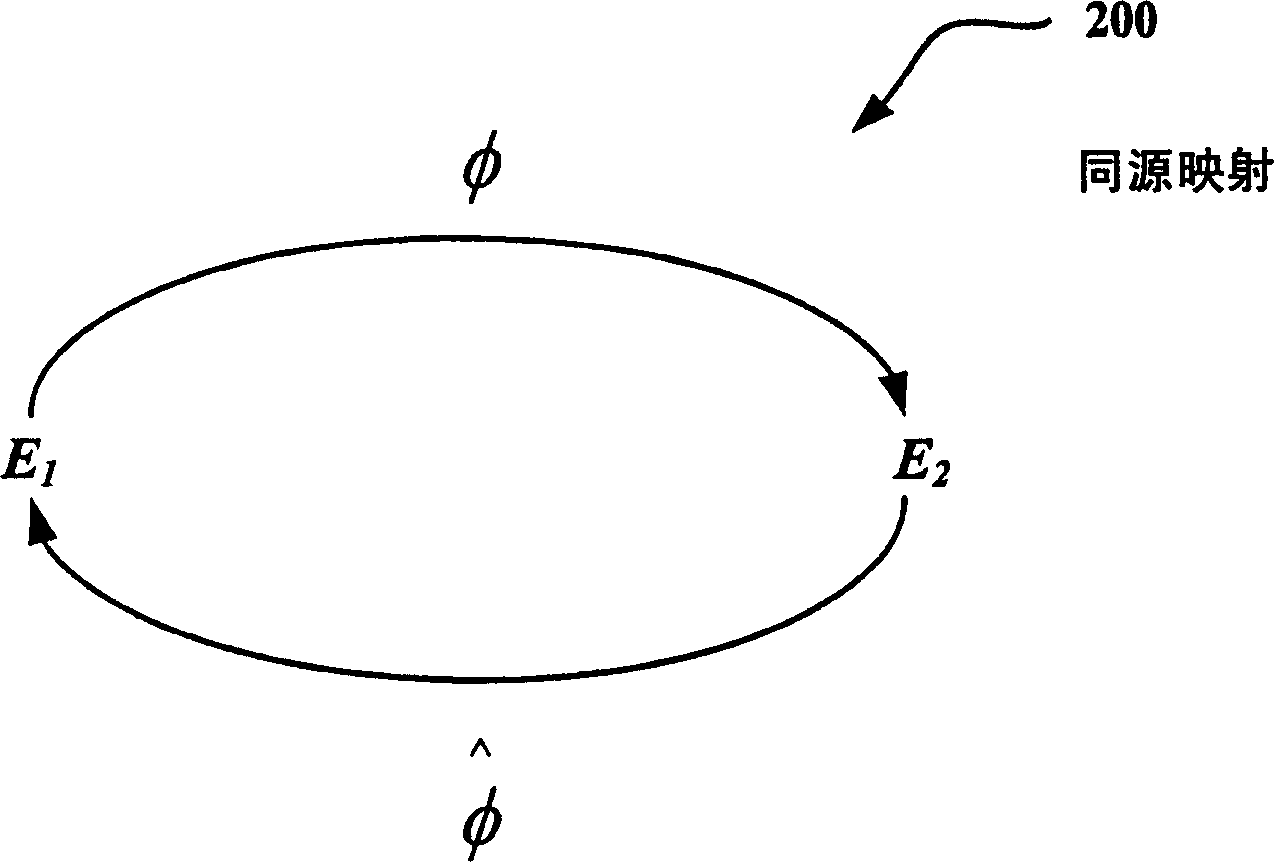
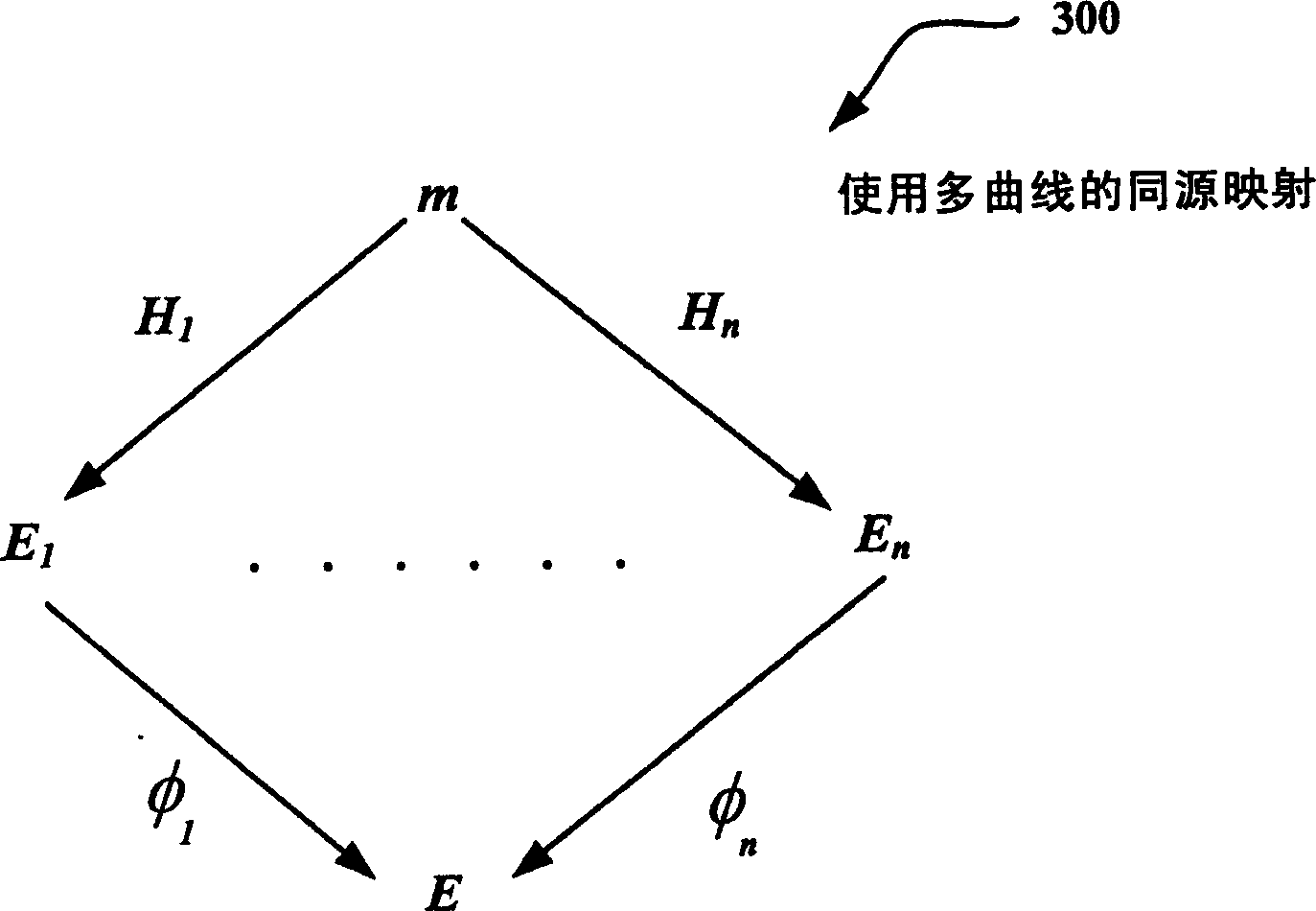
[0023] The following disclosure describes techniques for improving public key systems based on multiple elliptic curves (or Abelian varieties in general). Various techniques are disclosed for generating homology (or mapping) between curves. The resulting same-origin permission uses multiple curves instead of a single curve to provide public encryption. Additionally, the technique can be applied to relatively short digital signatures (eg, typed in by the user or sent over a low-bandwidth channel) and / or identity-based encryption (IBE) solutions (eg, allowing storable public keys). Short signatures also provide additional efficiencies through total ver...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com