Data protection method and system
A data protection and data technology, applied in the direction of protecting storage content from loss, preventing unauthorized use of memory, etc., can solve problems such as illegal deletion of files, attacks, application software threats, etc., achieve a high level of security, prevent information loss, and prevent The effect of illegal theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
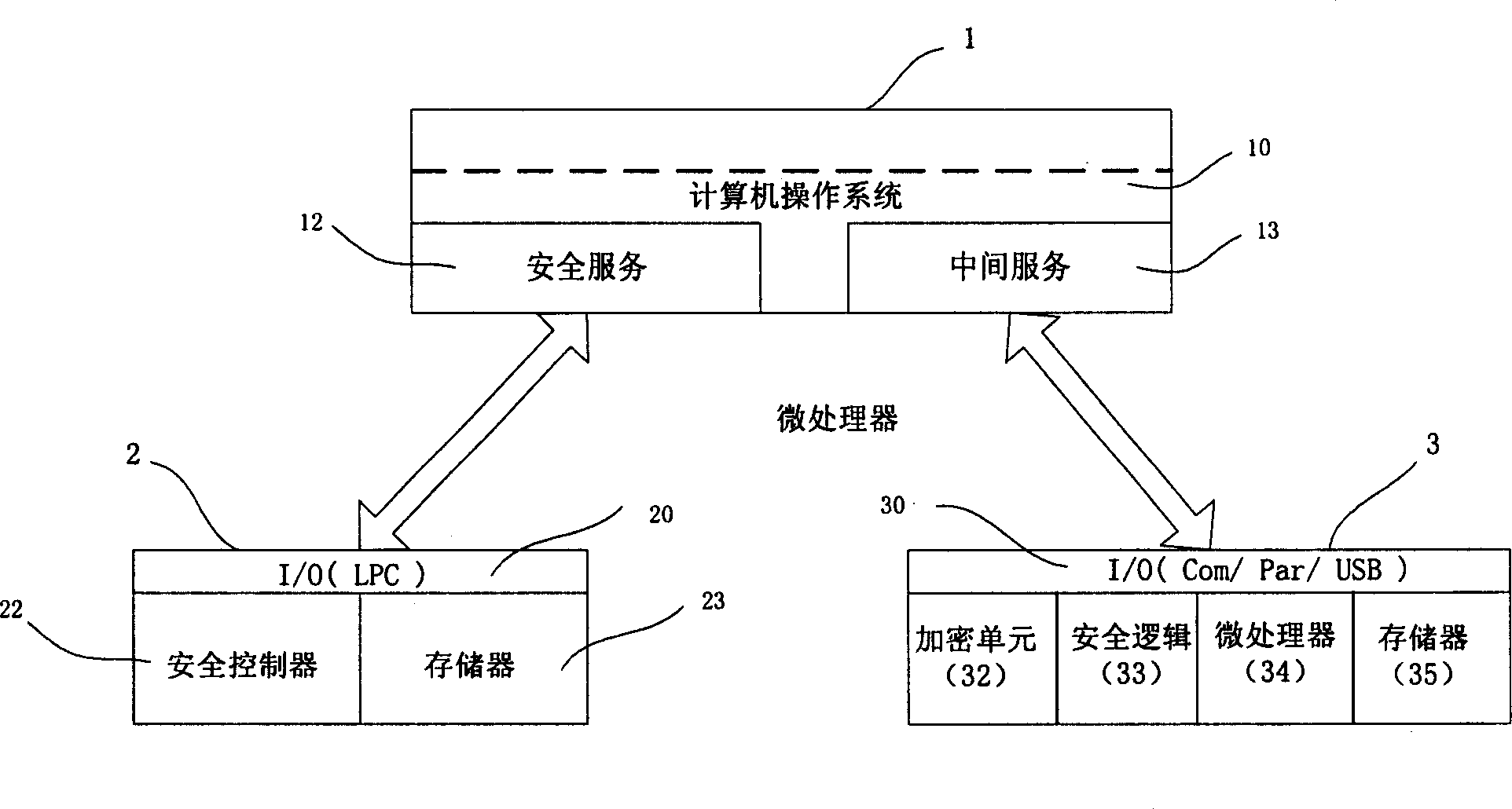
[0025] Please refer to figure 1 As shown, the data protection system of the present invention realizes data protection based on the security chip 2 and the hardware token 3 located on the motherboard of the computer 1 .
[0026] Therefore, the data protection system of the present invention includes a computer 1, a security chip 2 and a hardware token 3 connected to the computer 1, which are respectively described below:
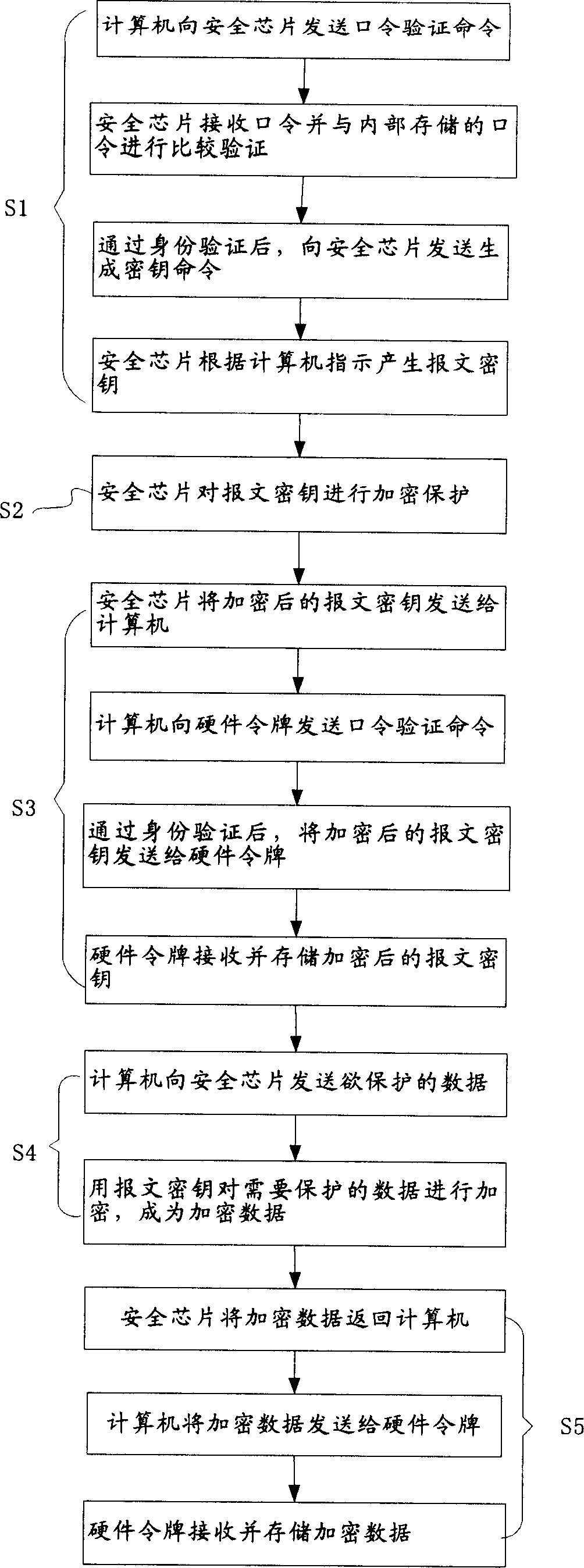
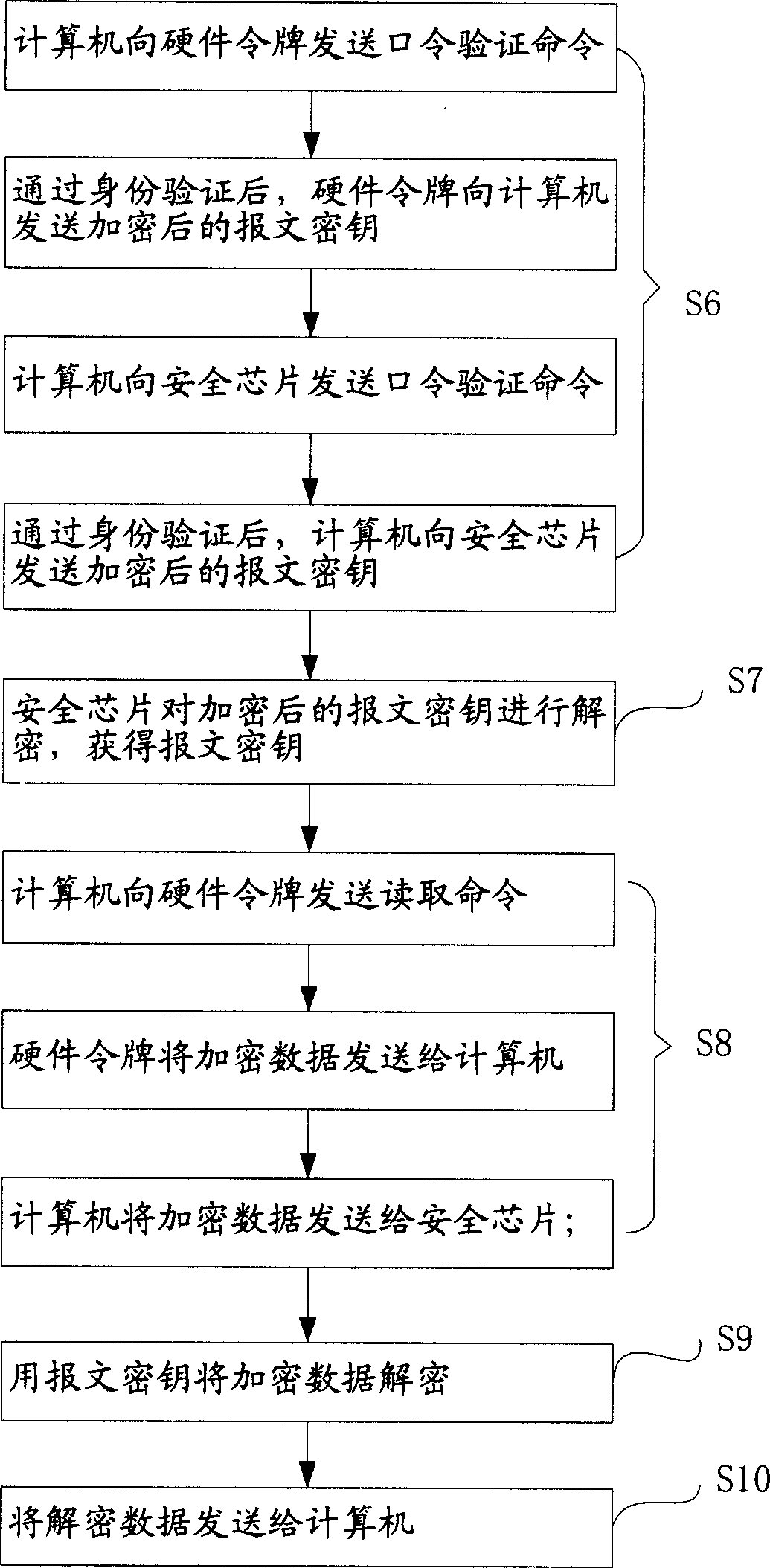
[0027] Computer 1 is used to establish data interaction between security chip 2 and hardware token 3. When encrypting, send the data to be encrypted to security chip 2, and send the encrypted message key and encrypted data to hardware token 3 for storage ; Send the encrypted message key and encrypted data to the security chip 2 for decryption during decryption. The operating system 10 in the computer 1 is provided with a security service module (TSS, Trusted Software Stack) 12 and an intermediate service module 13 for data interaction with the security chip...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com