IPSEC nesting strategy match correcting method
A verification method and strategy technology, applied in the field of information security in the field of information technology, can solve problems such as time-consuming and performance bottlenecks of IPSEC communication systems, and achieve the effect of improving efficiency and performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
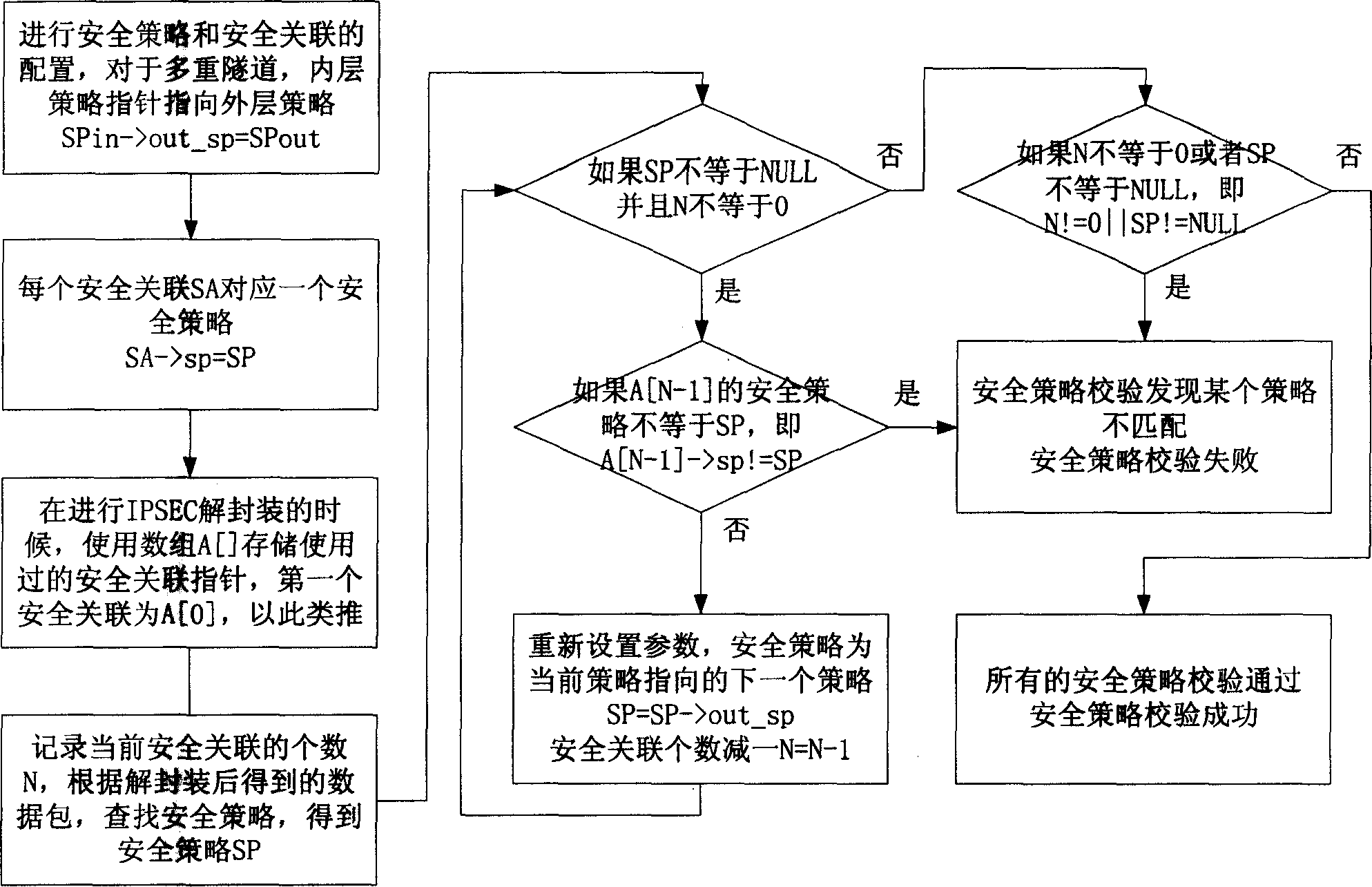
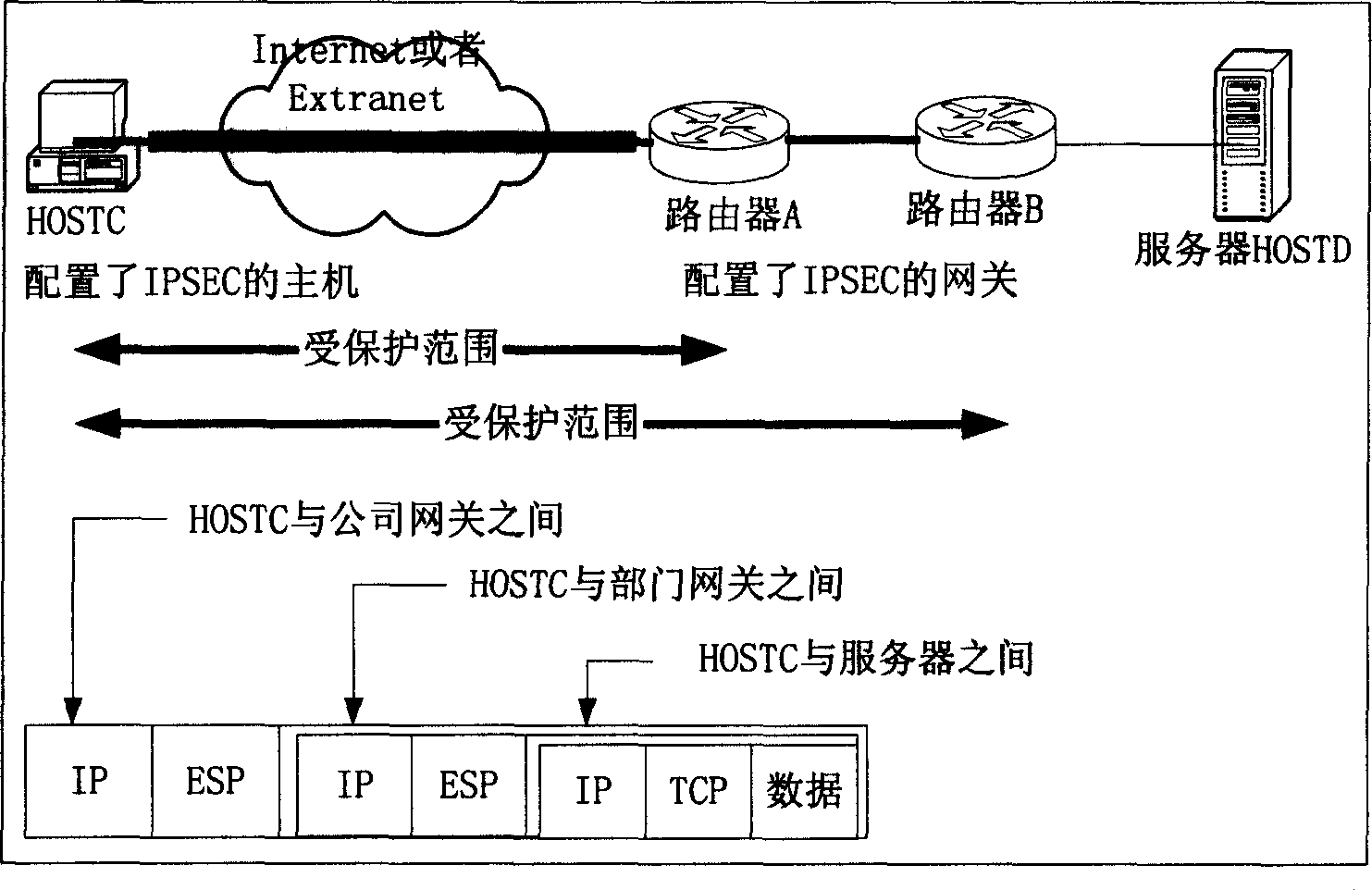
[0026] The IPSEC nested policy matching verification method of the present invention will be specifically described below in conjunction with the embodiments. First define the relevant data structures of security association SA and security policy SP:
[0027] The security association SA includes the following fields: destination IP address (dest_ipaddr), security protocol (proto), security parameter index (spi), cryptographic algorithm and other parameters (crypto), and attribution security policy (sp).
[0028] The security policy SP includes the following fields: source IP address (source_ipaddr), destination IP address (dest_ipaddr), tunnel source IP address (tunnel_source_ipaddr), tunnel destination IP address (tunnel_dest_ipaddr), upper layer protocol (proto), corresponding security association (sa) , Outer security policy (out_sp).
[0029] Use a security association array to store the SA that operates on a data packet, and this array is SAG[].
[0030] N represents t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com