Short block processing method in block encryption algorithm
A technology of group encryption and encryption algorithm, which is applied in encryption devices with shift registers/memory, digital transmission systems, electrical components, etc., can solve problems such as inability to realize secure data transmission, eliminate potential safety hazards, ensure transmission efficiency, The effect of ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
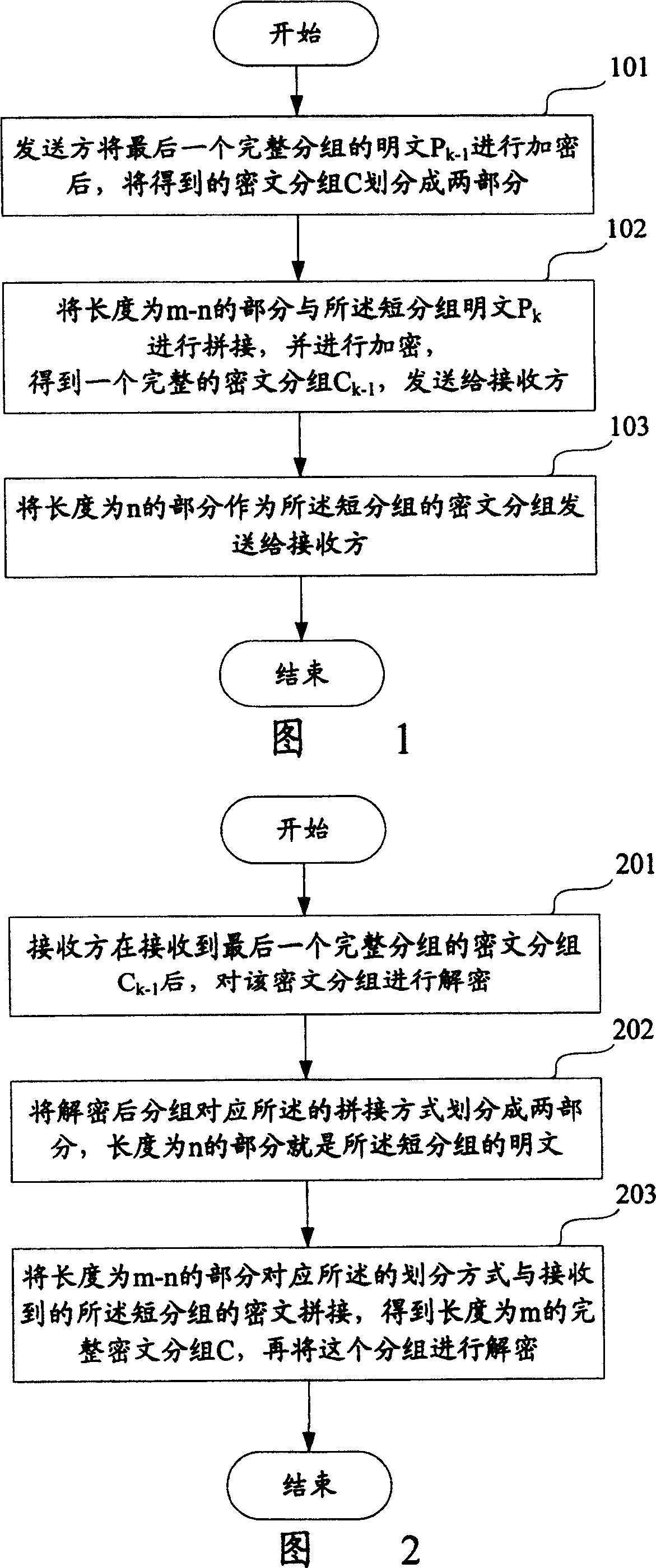
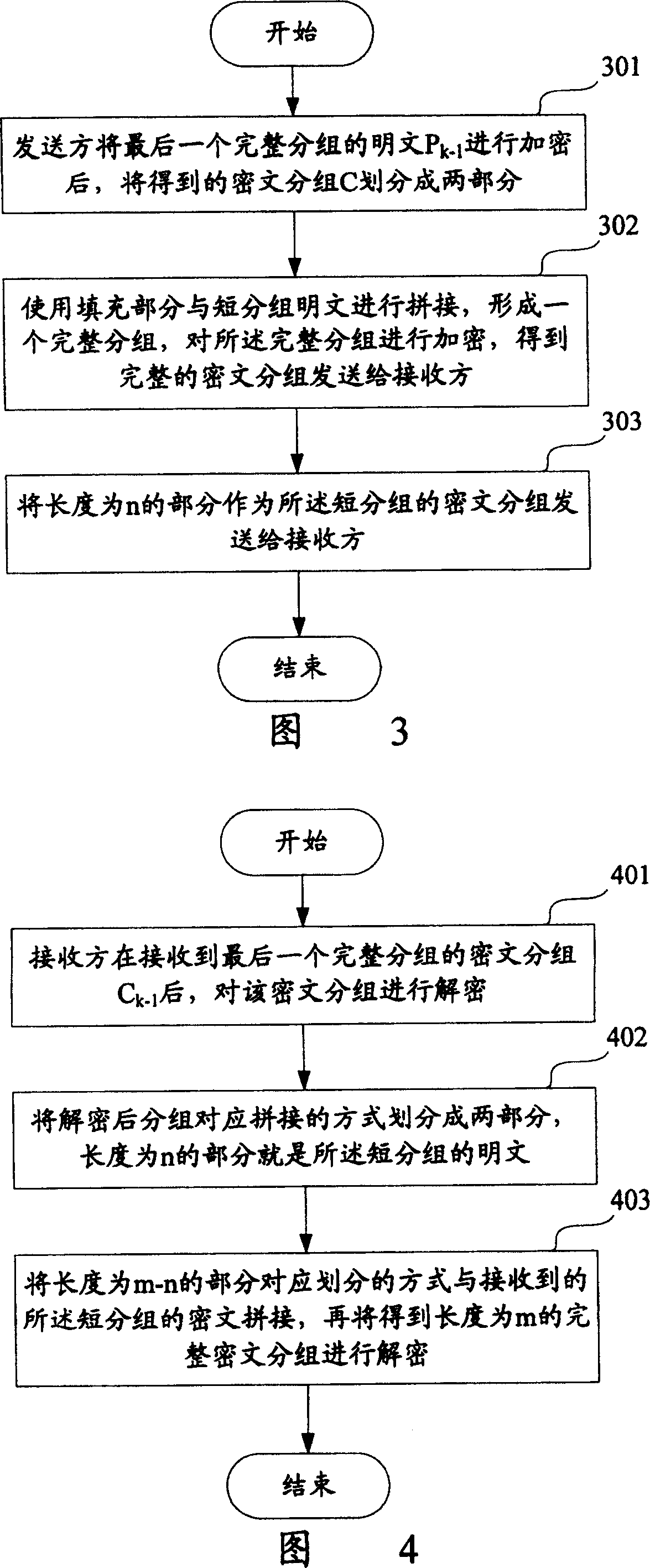
[0058] In order to solve the problems existing in the prior art, the present invention provides a method for processing short packets in a packet encryption algorithm. The main idea of the method is: fill the short packets into a Complete group, and then use the existing encryption algorithm to encrypt the complete group, so as to ensure that all plaintext data sent by the sender is encrypted, and improve the reliability of system data transmission.
[0059] The method of the present invention is applicable to the situation that the length of the plaintext of the data block to be encrypted is greater than the length m of the complete group, that is, the group contains at least one complete group with the length m after grouping.
[0060] Fig. 1 shows a flow chart of a sender encrypting a short packet according to a preferred embodiment of the present invention. Here, it is assumed that the data blocks that need to be encrypted are divided into k groups according to the size ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com