Data query method, device and system based on exchangeable encrypted data confusion
A data query and encrypted data technology, applied in the field of privacy data processing, can solve problems such as data leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
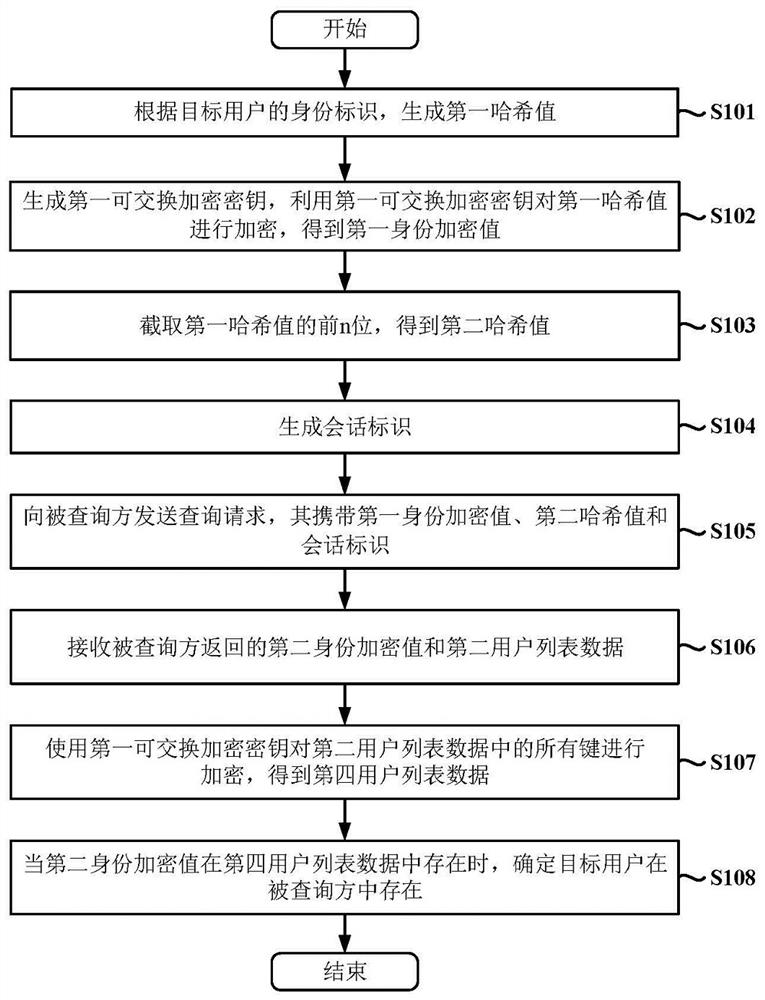
[0093] figure 1 This is a flow chart of a data query method based on exchangeable encrypted data obfuscation executed by a query party according to an embodiment of the present invention. like figure 1 shown, it includes the following steps:
[0094] S101: Generate a first hash value according to the identity of the target user;
[0095] Specifically, the identity identifier of the target user may include any one or a combination of any number of identity certification identifiers such as the user's mobile communication terminal number, identity card number, and passport number. In this step, the first hash value may be generated based on an information digest algorithm. Information digest algorithms include, but are not limited to, the md5 algorithm.
[0096] S102: Generate a first exchangeable encryption key, and encrypt the first hash value by using the first exchangeable encryption key to obtain a first identity encryption value;
[0097] S103: Intercept the first n b...
Embodiment 2
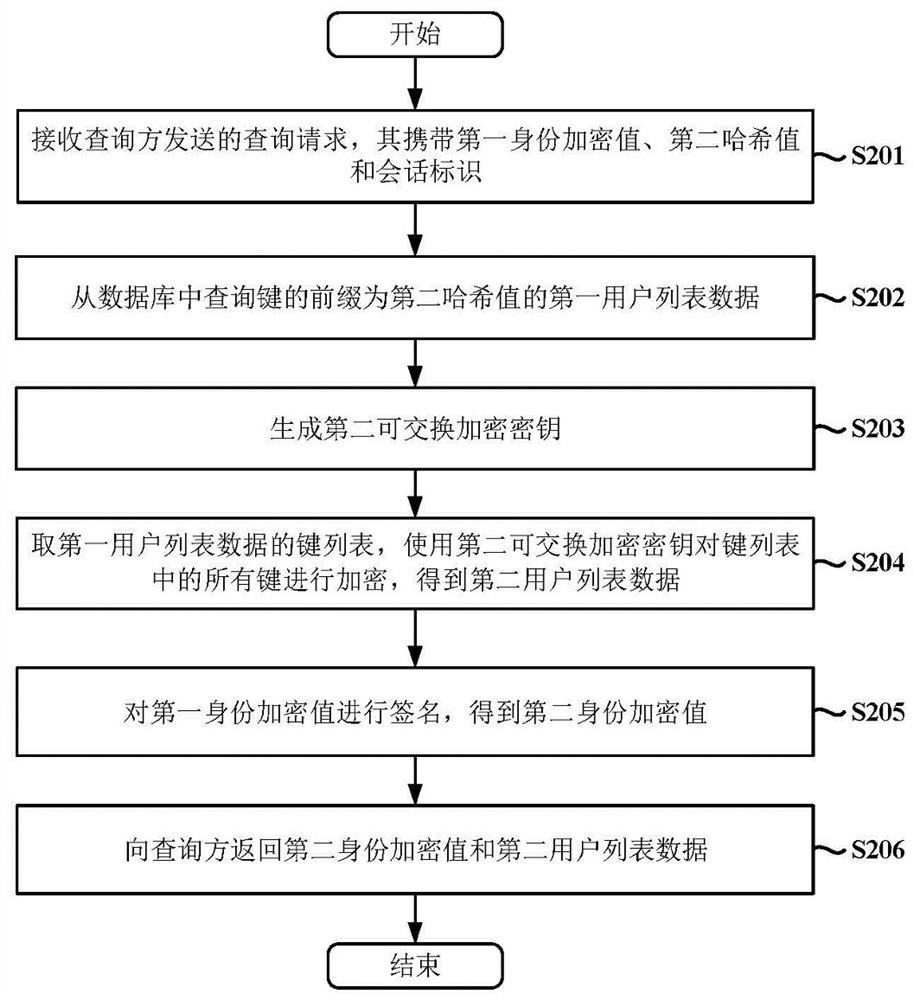
[0120] figure 2 This is a flow chart of the data query method based on exchangeable encrypted data obfuscation executed by the queried party according to the embodiment of the present invention. like figure 2 shown, it includes the following steps:
[0121] S201: Receive a query request sent by a query party, where the query request carries a first identity encryption value, a second hash value, and a session identifier;
[0122] S202: query the first user list data whose key prefix is the second hash value from the database;
[0123] S203: Generate a second exchangeable encryption key;
[0124] S204: Get the key list of the first user list data, use the second exchangeable encryption key to encrypt all keys in the key list, and obtain the second user list data;
[0125] S205: Sign the encrypted value of the first identity to obtain the encrypted value of the second identity;
[0126] S206: Return the encrypted value of the second identity and the data of the second u...
Embodiment 3
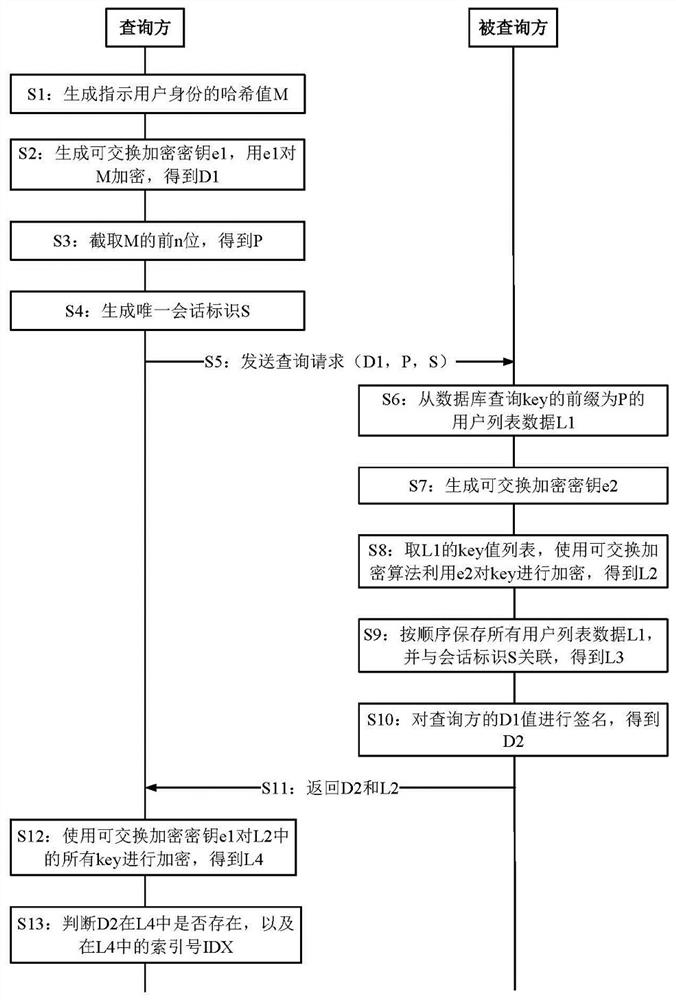
[0138] image 3 This is an overall flow chart of a data query method based on exchangeable encrypted data obfuscation executed by the system according to an embodiment of the present invention. like image 3 shown, it includes the following steps:
[0139] S1: The query party generates a target user key according to the user identity, which is a hash value M indicating the user identity.
[0140] The hash value M is a hash value of a unique identifier for identifying the user identity; the user identity identifier may be a mobile phone number or an ID number. The relevant calculation formula is as follows: key=md5 hash(mobile|IdNo).
[0141] In the embodiment of the present invention, md5 can be used to hash the query key to perform hashing and desensitization of the original key value; the advantage of the md5 algorithm is that the final hash value can be output with a uniform length regardless of the length of the input data; Good dispersion, that is, two similar inputs,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com